Updates (January 2026 to March 2026)
January 2026 — Updated the topic to add information about the rules supported in Traceable. For more information, see Integration Overview.
Akamai Web Application Firewall (WAF) is a robust, cloud-based security solution that protects web applications from malicious attacks, including SQL injection, cross-site scripting (XSS), and other common threats. Integrating Traceable with Akamai WAF enhances the security posture by leveraging Traceable's deep API observability, AI-driven insights, and advanced anomaly detection capabilities. This integration enables organizations to gain comprehensive visibility into their API traffic and security events, while also benefiting from the scalable protection that Akamai WAF provides. Together, they offer a powerful solution to detect, prevent, and respond to sophisticated threats targeting modern web applications and APIs.
What will you learn in this topic?
By the end of this topic, you will be able to understand:
An overview of the steps required to set up the integration.
The prerequisites for setting up the integration with Traceable.
The steps to integrate Akamai with Traceable.
The run-time behavior after integration.
Integration Overview
This section provides high-level information on integrating Akamai WAF with Traceable and managing threats.
Installation — Traceable allows you to choose from an agent-less or agent-based deployment option. For more information on Traceable agents, see Installation.
Integration Setup — After deploying the agent, you can retrieve the credentials and configure the Akamai integration. To do so, you must complete the following steps:
Prerequisites — Log in to your Akamai and fetch the required credentials, such as the network list ID and Akamai policy ID, to configure the integration. For more information, see Before you begin.
Integration — After obtaining the credentials from the previous steps, navigate to the Traceable platform and configure the integration. For more information, see Set up the Integration.
Threat Management — After setting up the integration, you can establish rules to allow, block, or monitor IP addresses according to your specific requirements. Traceable’s integration with Akamai supports the following three types of rules:
Threat Actors — Any status change of the threat actor on the Traceable Platform is propagated to Akamai. For example, if Traceable detects a threat actor and changes it to a deny state, then the requests from this threat actor can be blocked using Akamai. Moreover, if you make any changes, such as adding a threat actor to the denylist or resolving the status, these changes are reflected in Akamai within a few minutes. Traceable allows creating allowlists using allowed and snoozed states, and supports blocking using deny and suspended states under threat actors. For more information, see Threat Actors.
Malicious Source Rules (IP Range only) — If you configure any malicious source rules under Protection → Policies → Custom Policies → Malicious Sources tab to enforce blocking for IP ranges to be executed through Akamai.
Custom Signature Rules — You can set up Custom Signature rules under Protection → Policies → Custom Policies → Custom Signatures tab to block incoming requests from a specific URL by matching the corresponding endpoints. For more information, see Custom Policy. To see the support matrix for Custom Signature Akamai WAF, see Support Matrix for Custom Signature Rules.
Note
Each update to a custom signature rule results in the creation of a new Akamai policy version, which must be activated before enforcement begins. While activation is in progress (typically 7–8 minutes), the new rule is not active, although existing rules remain in effect.
During this activation window, no additional custom signature rules can be pushed. Akamai does not allow cloning or modifying a policy version that is in the middle of an activation cycle. Attempting to do so may result in integration failure or silent rejection. Subsequent custom rules must wait until the previous version has completed activation before being processed.
The following is a high-level integration diagram:
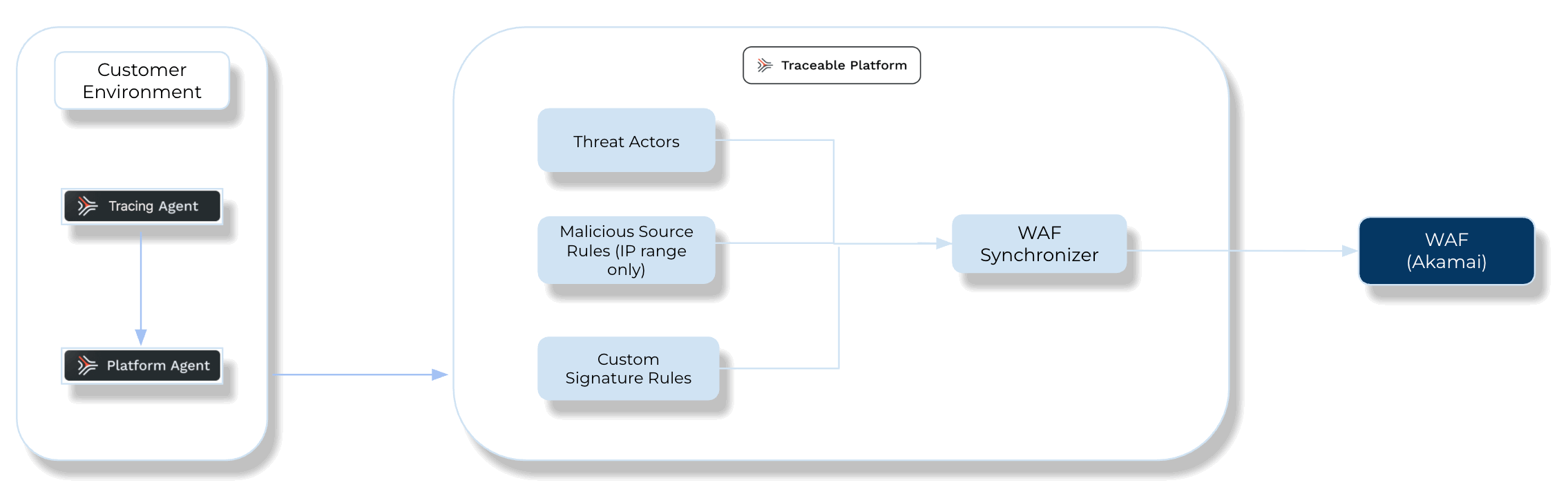
Traceable Akamai Integration Diagram
Before you begin
Make a note of the following before you proceed with the integration:
Ensure you understand the Akamai network list, policy, and how to attach a network list to a policy.
The network list must be explicitly attached to the Akamai policy you plan to use with the Traceable integration. The integration will fail validation if the network list is not attached to the selected policy version. There are two supported approaches depending on your scenario:
Suppose you are creating a new policy specifically for this integration. In that case, it is recommended that the policy be created, the network list be attached during configuration, and the policy ID and network list ID be activated before retrieving the policy ID and Network List ID.
If you want to use an existing policy that is already active, note that Akamai does not allow modifying active versions. In this case, you must:
Clone the existing policy to create a new version.
Attach the network list to this unactivated version.
Activate the new version.
Once the policy version and network list are active and associated, use their IDs in the Traceable integration. This combination is validated during setup. If the list is not found to be attached to the activated policy, the integration will fail validation.
A network list is created in the Web Security section of the Akamai Control Center.
The network list is attached to a policy version that has not yet been activated.
The updated policy version is then activated. Akamai does not allow editing of an already activated policy version.
The Policy ID and Network List ID used in the integration must reference active and associated configurations.
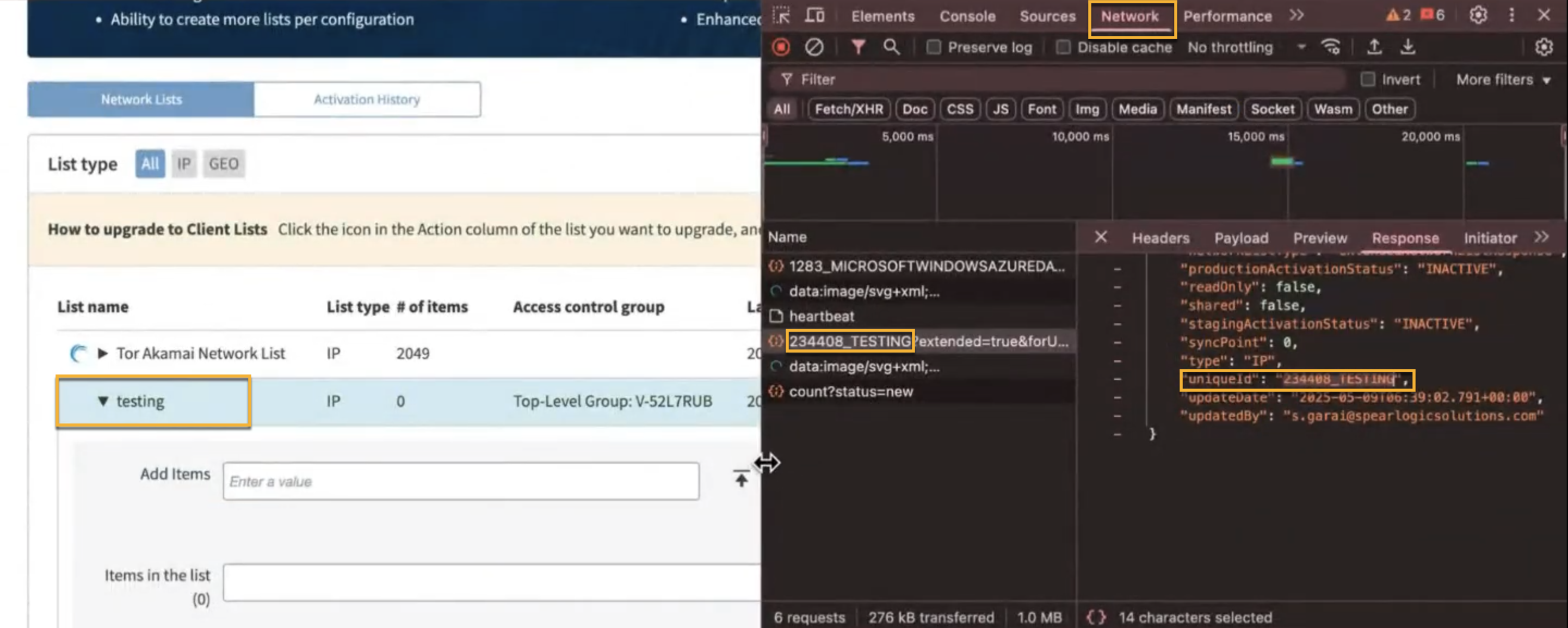
The Network List ID field references an existing network list configured in the Akamai Control Center. This list is required for IP-based blocking and enforcement of threat actor rules. All IP addresses sent through the Traceable integration are appended to the specified network list, which must be associated with an activated Akamai policy. To obtain the Network List ID, complete the following steps:
Log in to the Akamai Control Center.
Navigate to Web Security → Network Lists.
Open the browser’s developer tools and go to the Network tab.
Click the desired network list entry. The request URL or response payload will display the Network List ID.
Copy the portion of the ID that appears before the query parameters.
Note
Only network lists that are attached to active policy versions can be used in the integration.
The Notification Emails field accepts one or more email addresses that will receive alerts regarding the status of their activation. Notifications are sent when configurations are updated, IPs are added or removed, or policy changes are activated. The notification mechanism uses a push-based model. A default internal address may be used for system-level logging if no email addresses are provided.
The Akamai Auth Credentials comprise the Access token, Client token, and Client Secret. For more information, see Akamai Documentation.
Set up the Integration
To configure a new Akamai integration, navigate to Integrations → WAF, and do one of the following:
Search for Akamai in the search bar.
Navigate to WAF → Akamai.
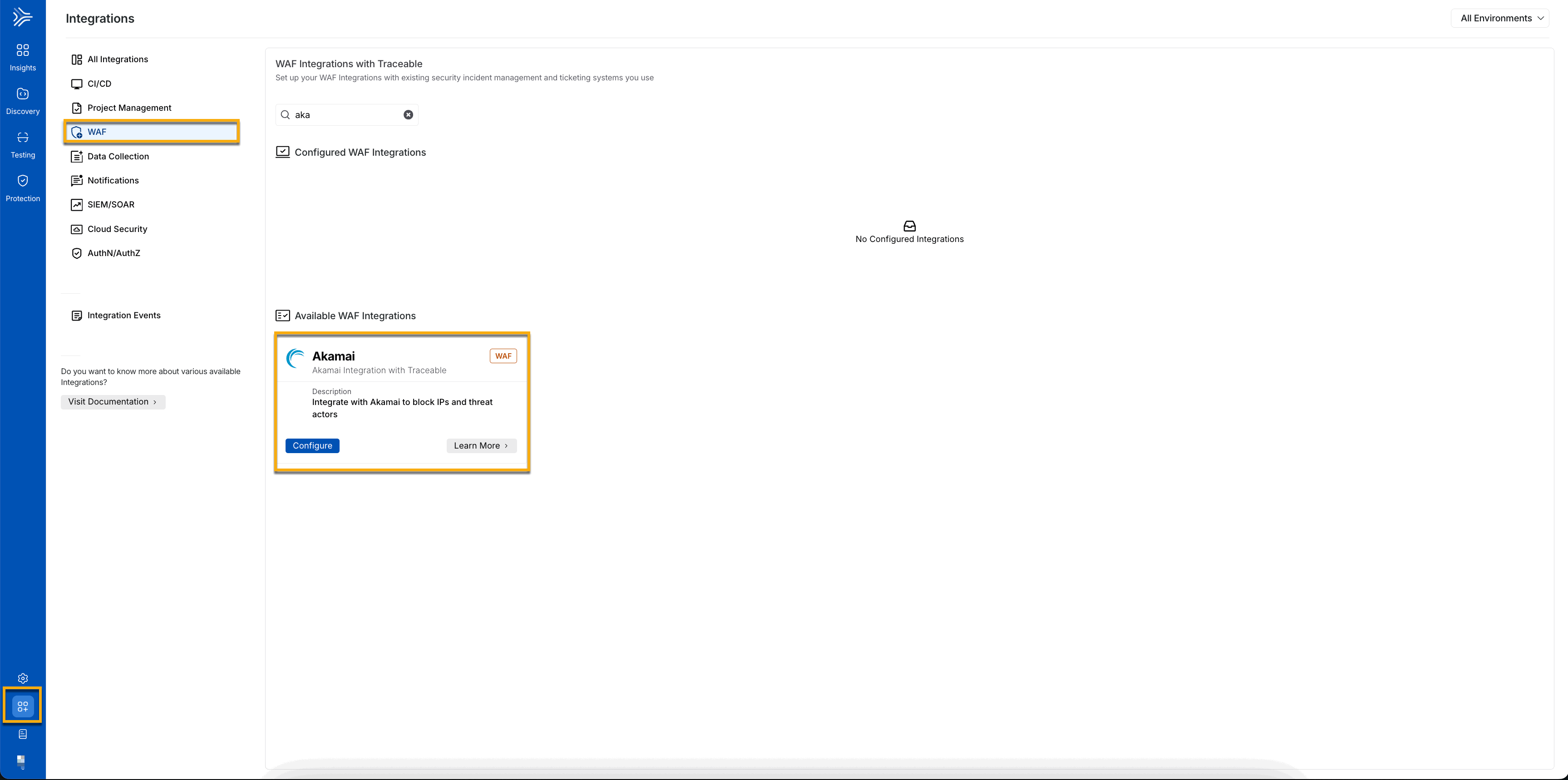
Akamai Integration Navigation
In the Akamai widget, click Configure, and in the Add New Akamai Integration window, complete the following steps:
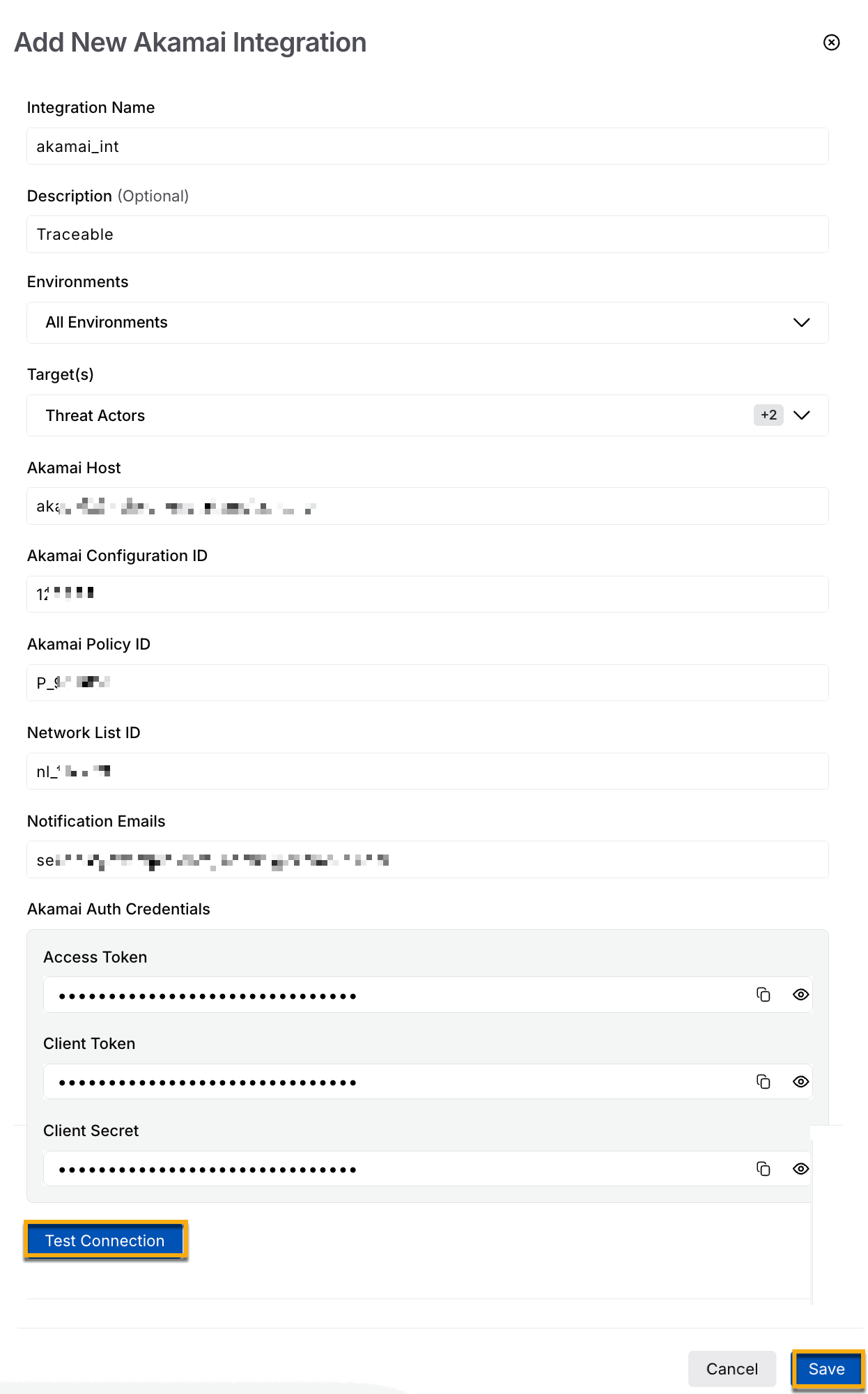
Add New Akamai integration
Specify the Integration Name, for example, Akamai_int.
(Optional) Specify the Description.
Choose the environment for which you wish to integrate Akamai. You can also choose All Environments, which will integrate Akamai with all available environments.
Note
Each environment can have more than one Akamai integration.
Select the Target(s) field to specify one or more enforcement categories for which the integration will take action.
Depending on the scope of protection you want to configure through Akamai, you can select one, multiple, or all available options. To proceed with the integration, at least one target must be selected. If no target is selected, the integration setup will not be allowed.
Specify the Akamai Host. You can contact your Akamai administrator to fetch this value.
Specify the Akamai configuration ID. You can contact your Akamai administrator to fetch this value.
Specify the Akamai Policy ID of the policy that you wish to integrate with Traceable. Each integration can have only one Policy ID. If you wish to combine more than one policy, create separate integrations for each policy. Navigate to Web and Data Center Security → Security Configurations in your Akamai account. All the security policies are listed in the Security Configurations. Each policy has a Policy ID. Choose the Policy ID for which you wish to complete the integration.
Note
You can create only one integration with a unique policy ID in the same environment or across environments.
Specify the Network List ID. Each time a new IP address or threat actor is identified, it is automatically pushed to the same network list. This centralized list is continuously updated without requiring the creation of new custom rules or policy versions. Once the network list is configured and activated, Traceable handles subsequent additions through API calls without user intervention. For more information, see Before you begin.
Specify the Notification Emails. For more information, see Before you begin.
Under the Akamai Auth Credentials, specify the following:
Access Token — It is used to authenticate API requests and is generated in the Akamai Control Center.
Client Token — It is used to identify your API client and is included in the credentials file from Akamai.
Client Secret — It is used to sign requests securely and is generated during the initial creation of the API client. For more information, see Before you begin.
Click Test connection. The Save button is enabled only after the connection test is successful.
Integration behaviour and viewing WAF rules
When an IP address or threat actor is blocked through Traceable, the corresponding entry is added to the network list. Akamai then initiates an automatic activation cycle that takes approximately five to seven minutes to complete. During this time, previously active entries continue to function normally. If an IP address appears in multiple rule types (IP and threat actor), it is removed from the network list only after being deleted from all associated types. Deleting the Traceable integration removes all IPs added by Traceable from the network list; the list itself is retained.
The rules generated through this integration can be viewed directly in the Akamai Control Center. The appearance and location of these rules depend on the target type selected in the configuration.
For Custom Signature rules:
Navigate to Web and Data Center Security → Security Configurations → Custom Rules.
Locate the policy used in the integration to view active rules pushed by Traceable.
If the same rule exists across multiple policies, its behavior (for example, allow, deny) will vary by policy.
Rules cannot be deleted from Akamai if any active policy version uses them.
When Traceable deletes a rule, its status is updated to Not Used in Akamai.
Deleting the integration does not remove custom rules from Akamai, as active configurations may use them.
For Malicious Source (IP range only) and IP-based Threat Actors:
Navigate to Web Security → Network Lists.
Open the associated network list to view all IPs pushed by Traceable.
All IP updates occur within the same list. IPs remain active unless explicitly removed.
If the same IP is associated with multiple rule types, it is only removed after deletion from all associated sources.
Note
A maximum of 100 rules is allowed in Akamai. If rule creation fails due to Akamai’s 100-rule limit, users must manually delete rules via the Akamai console. Once the rule count drops below 100, successful creation events are generated for valid configurations.