The Threat Actors page in Traceable enables you to identify, investigate, and respond to threats that affect your APIs and applications. It provides a comprehensive view of users (both authenticated and anonymous), highlighting suspicious or malicious behavior.
The page provides the following details for every threat:
Who is behind the threat activity, in the form of the identified user or IP address.
What is the above threat actor doing in the form of specific threat behaviors and rule violations.
Where is the threat actor performing the above behaviors, in the form of endpoints or services targeted.
Using the details displayed on the page, you can make well-analyzed decisions on how to prioritize and respond to threats.
.png)
Threat Actors
What will you learn in this topic?
By the end of this topic, you will understand:
The way Traceable detects threats and classifies actors.
The details displayed on the Threat Actors page and the methods for leveraging them.
The details displayed for each threat actor and the methods of investigating it.
The statuses associated with a threat actor and the methods of modifying them.
The process of investigating and mitigating a malicious threat actor, using an example.
Understanding Threat Detection and Actors Classification
Traceable continuously monitors your application and API traffic to learn normal behavior patterns. Based on this learning, it creates a baseline for your application. If and when the behavior deviates from the baseline, Traceable flags such interactions as anomalies. As the number of anomalies raised by a specific source increases, Traceable labels the source as a Threat Actor. This classification is done for the following sources:
Anonymous sources, identified through IP addresses.
Authenticated users, identified through a user ID.
Each threat actor is assigned a threat score based on its severity and frequency of anomalies.
Understanding the Threat Actors’ View
The Threat Actors page lists entities that Traceable has identified as potentially malicious or suspicious. The page displays a high-level visibility, enabling you to identify and triage threats efficiently.
The following are some key insights displayed on the page:
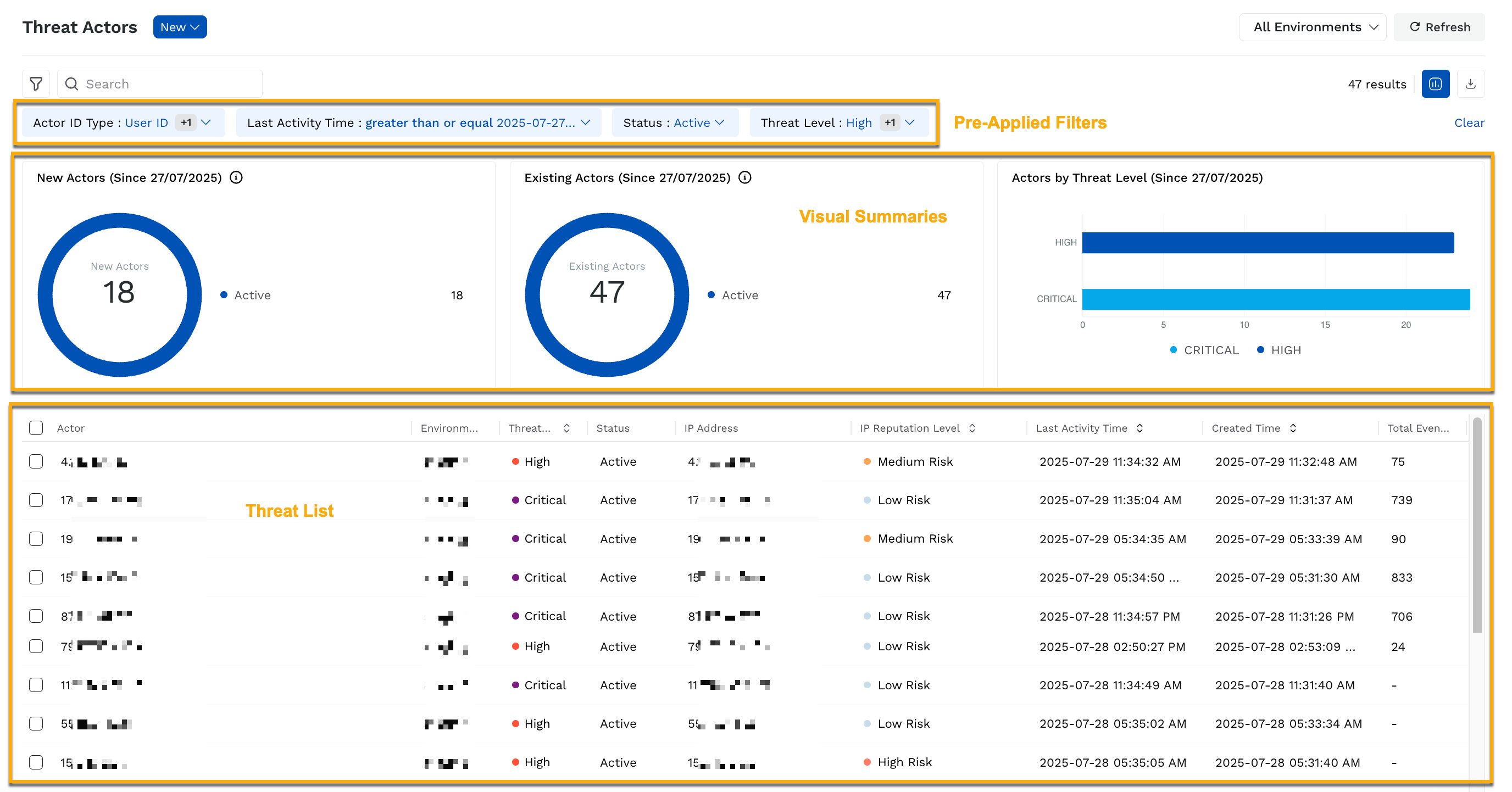
Key Insights
Pre-Applied filters that narrow down the list of actors based on their last activity, status, and threat level. This enables you to focus on the most recent and relevant threats.
Visual Summaries that highlight new and existing actors based on the last activity time, along with their distribution by threat level.
Threat List that highlights the actor’s details, including user ID or IP address, threat level, associated environment, reputation, and activity time.
Note
While the page displays details for All Environments by default, you can use the Environments drop-down in the page’s top right corner and view the information according to your requirements.
Leveraging the Threat Actors’ View
You can use the details displayed on this page to:
Identify threat patterns based on the visual summaries.
Prioritize remediation based on the threat or IP reputation level.
Apply filters to drill down into specific data according to your requirements.
Sort the details shown in a column according to your requirements.
Export actor data for analysis.
You can also investigate the threat actor further to gather more details, according to your requirements. For more information, see the section below.
Investigating a Threat Actor
After you have filtered or sorted threat actors according to your requirements, you can drill down into a specific threat actor for a detailed view (who, what, where) of its behavior. Based on this, you can determine the remediation method of the actor.
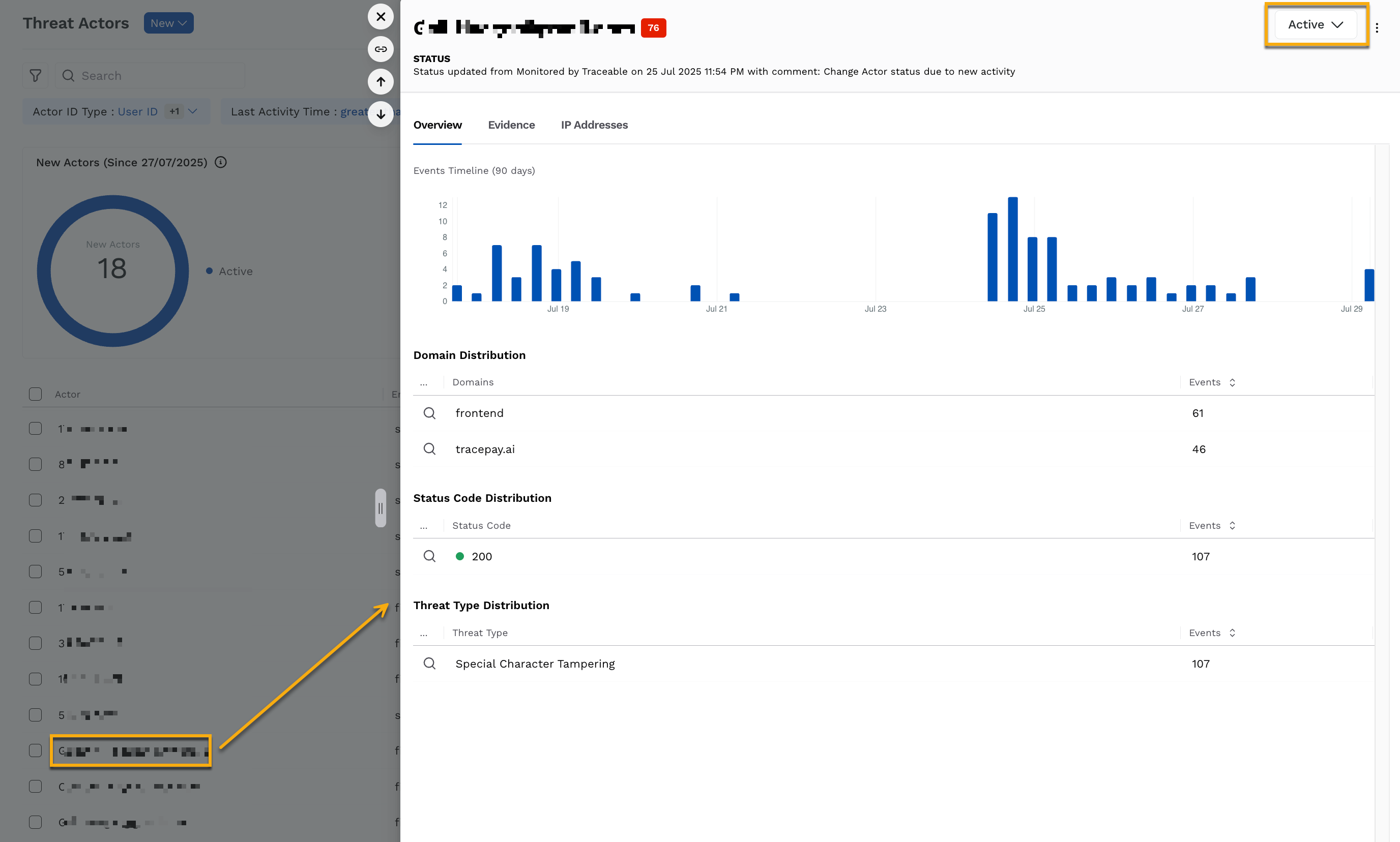
To drill down into a threat actor, you can click the corresponding row. Traceable displays the actor’s detailed view, highlighting their details, such as name, threat score, and status. Additionally, Traceable displays some key details about the threat actor in the following tabs:
The Overview tab provides a summary of the threat actor’s activity, using the following widgets. These widgets help you understand the threat actor’s focus.
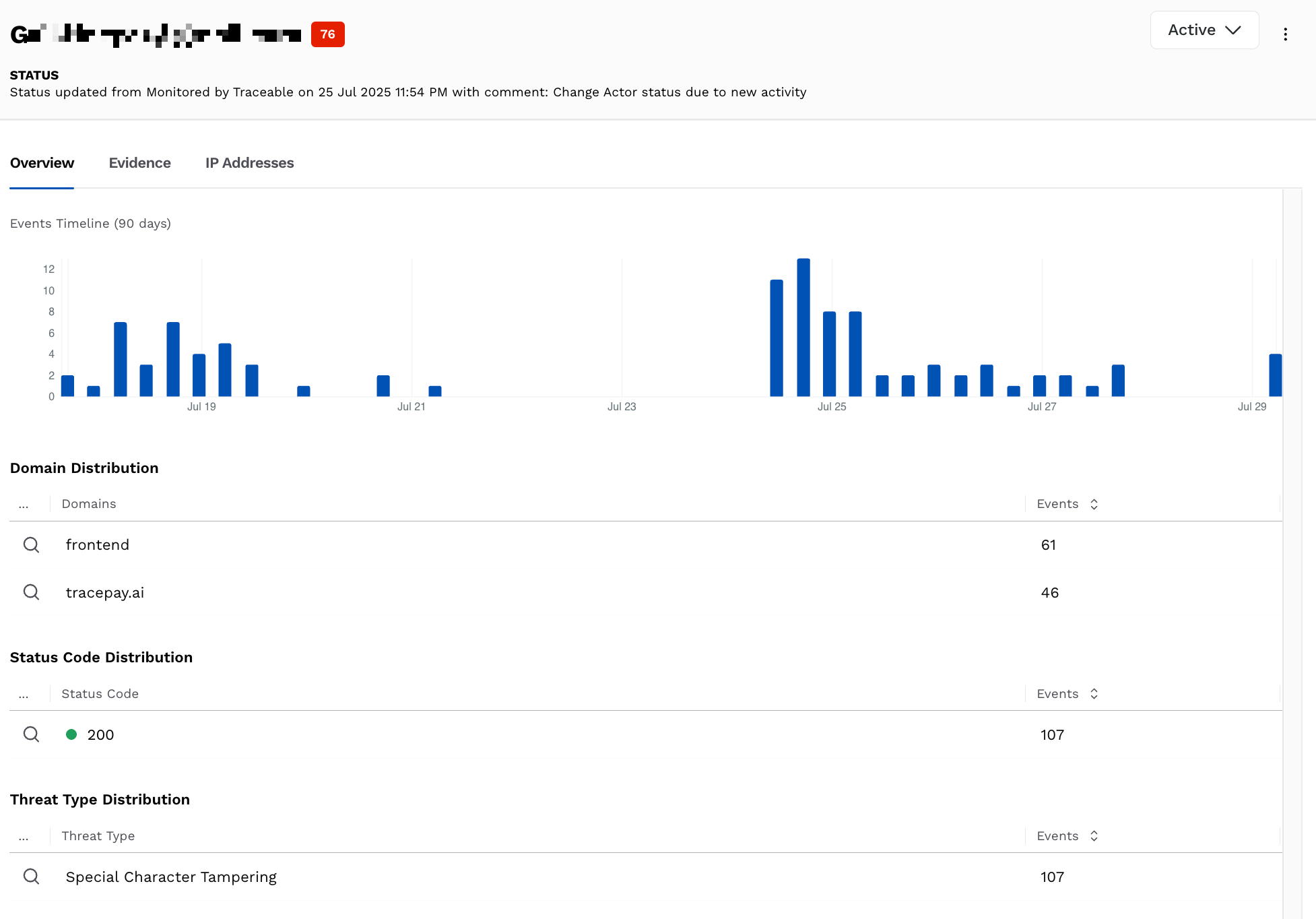
Overview
Events Timeline — This widget displays the number of Events generated by the threat actor over the past 90 days. You can use this widget to identify the actor’s relevance and patterns.
Domain Distribution — This widget displays the details based on the domains affected by the threat actor, along with the number of events for each.
Status Code Distribution — This widget displays the details based on the status code, along with the number of events for each.
Threat Type Distribution — This widget displays the details based on the threat type triggered by the threat actor, along with the number of events for each.
For each row in the above distributions, you can click the Search icon and view the evidence for it.
The Evidence tab provides granular details for every detection event, using the following widgets. These widgets help you understand the actor’s behavior and how and where it affected your application.
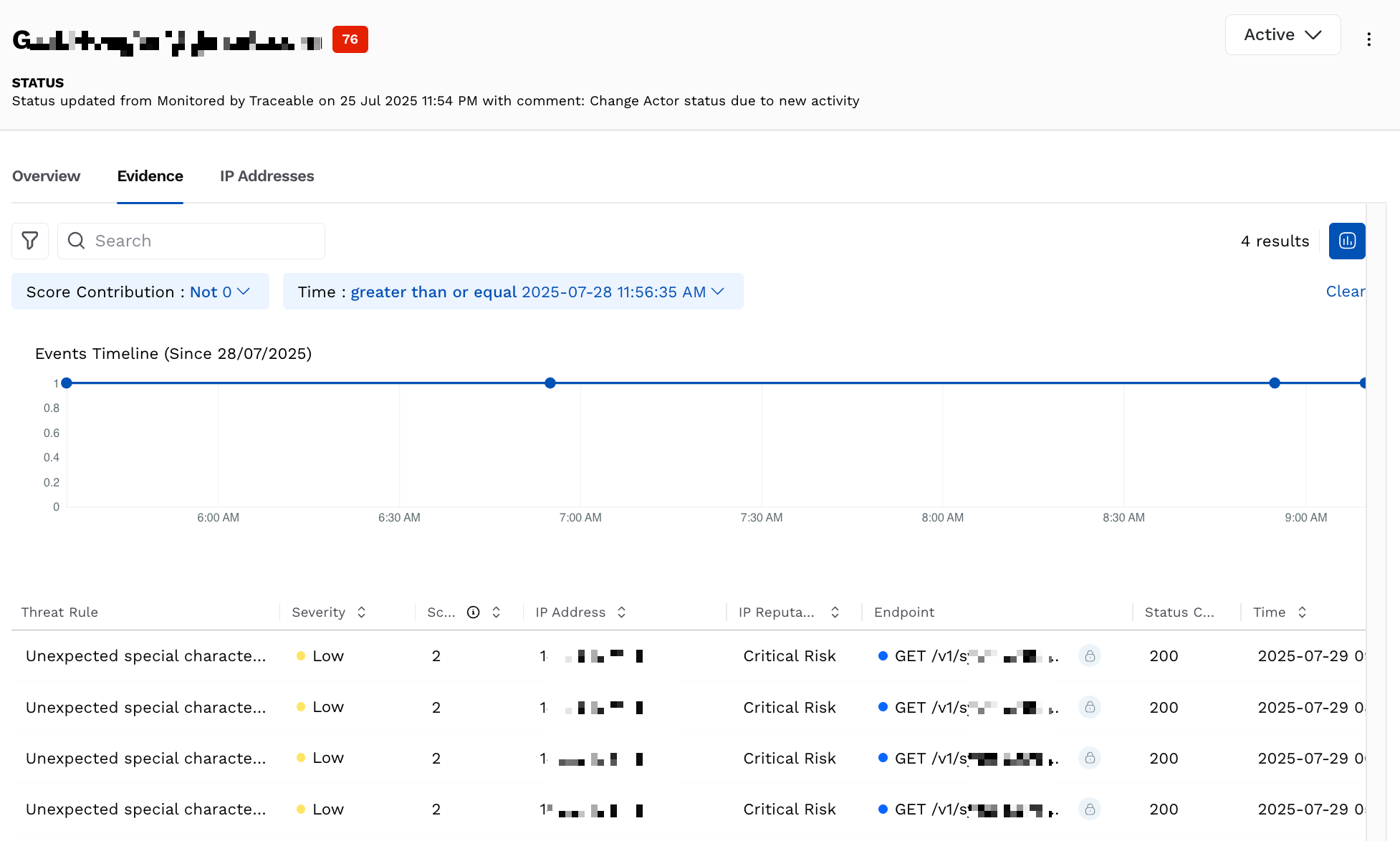
Evidence
Events Timeline — This widget displays the events generated by the actor in the last 24 hours. It helps you identify whether the activity followed a recurring pattern, such as a scheduled automation, or appeared randomly across the time range.
Event List — This widget displays the details of the threat actor’s events, such as the triggered threat rule, its severity, score contribution, and the IP address involved. You can click on an event in the list to view additional details, such as the request payload. It helps you understand whether the attacks are targeted or not.
The IP Addresses tab provides a list of all IPs used by the threat actor. Each row displays details, such as the reputation level, geographical information, and network details, such as the IP organization. You can use the information displayed in this tab to determine whether the actor is operating from a static IP in a high-risk infrastructure or a dynamic IP.
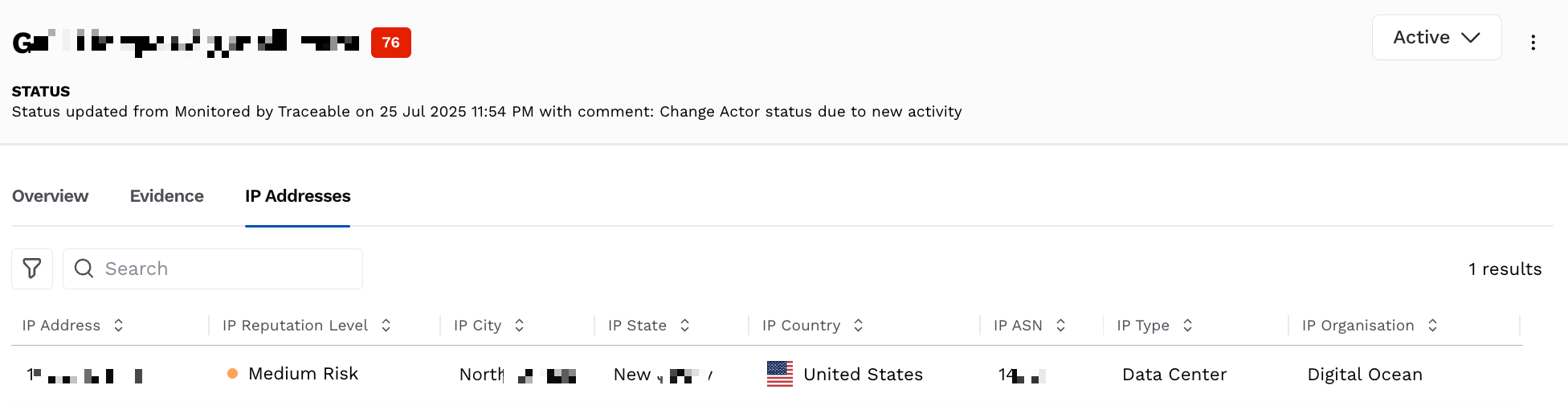
IP Addresses
The above tabs combined provide an investigative flow, from behavior patterns to evidence to infrastructure. This helps you qualify threats before working on their remediation.
Threat Actor Mitigation
While Traceable dynamically updates a threat actor’s status based on its activity, you can modify its status according to your requirements. The status you select applies to the threat immediately.
Available Statuses
Traceable provides the following statuses:
Threat Actor Status | Description |
|---|---|
Active | This is the default status assigned to a threat actor when Traceable identifies it. This means that the actor has been active recently. |
Monitored | This is the status assigned to an actor in either of the following scenarios:
|
Resolve | This is the status assigned to an actor when it is no longer a threat. Moving a threat actor to this state resets its severity to 0. Even after you update an actor to this state, Traceable continues to monitor traffic and reports the threat again if it detects any malicious activity associated with it. Additionally, Traceable moves it to the Active status. |
Allow | This is the status assigned to an actor when you want it to access your application ecosystem, even when it has malicious activities. |
Snooze | This is the status assigned to an actor when you wish to temporarily allow it to access your application. While selecting this status, you can select the duration (one hour to a week) for which you wish to allow the actor. |
Suspend | This is the status assigned to an actor when you wish to temporarily block it from accessing your application. While selecting this status, you can select the duration (one hour to a week) for which you wish to block the actor. |
Deny | This is the status assigned to an actor when you wish to permanently block it from accessing your application. |
Note
If an actor in the Suspend or Deny status uses additional IP addresses to access the application, Traceable blocks them as well. Further, Traceable maintains a list of such IP addresses and blocks its future access unless you move the actor to a different state.
Updating the Status
You can update the status of a threat actor using either of the following methods:
Individual Update — Update the status of each threat actor individually.
Bulk Update — Update the status of multiple actors at once.
The following tabs highlight the steps for the above methods:
To update the status of an actor, complete the following steps:
Individual Status Update
In the Threat Actors page, click the actor you wish to update the status for.
In the Actors Detailed View page’s top right corner, click the Status drop-down and update the status according to your requirements.
To update the status of one or more actors, complete the following steps:
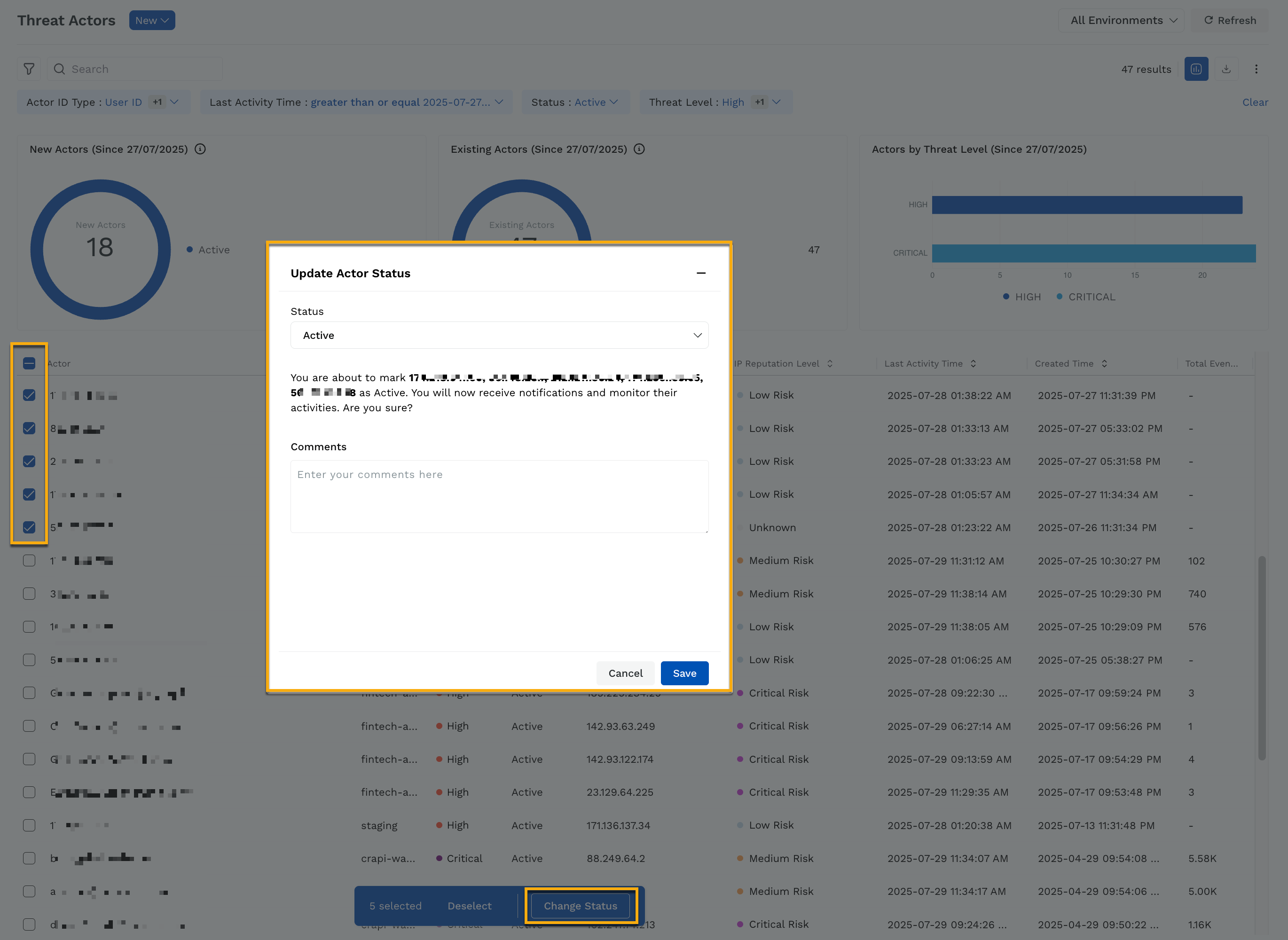
Bulk Update
In the Threat Actors page, select the checkboxes next to the issues that you wish to update the status for.
At the bottom of the page, click Change Status.
In the Update Actor Status pop-up window, select a status from the drop-down and add comments according to your requirements.
Click Save.
Example — Investigating and Denying a Threat Actor
Suppose you identify a spike in the number of Critical actors. Upon filtering the list of actors, you identify a new actor with a threat score of 100 that has triggered multiple Enumeration and Data Loss Prevention rules within the past 10 hours.
Upon clicking the actor:
In the Overview tab, you identify repeated interactions with authentication-related endpoints along with inconsistent status codes.
In the Evidence tab, you identify a pattern of failed login attempts followed by requests with large payloads.
In the IP Addresses tab, you identify that the actor is using a VPN-based infrastructure.
Upon analysis, you identify that the actor poses a threat to your application and modify its status to Deny, and leave a comment describing the activity to your team.
Now, Traceable blocks this actor and associated IP addresses from accessing your APIs, and logs it for future reference.