Traceable AI combines the power of end-to-end distributed tracing, cloud-native integrations, and advanced ML-powered behavioral analytics to deliver API and application security from user to code. As businesses migrate their applications to cloud-native architectures and adopt agile and DevOps practices, they are being attacked by sophisticated hackers using the latest emerging tactics. APIs expose business logic to hackers, and complex micro-service environments make it easy for security vulnerabilities to sneak through the cracks. To combat these new threats, Traceable delivers a strong and adaptive security foundation that protects your business. Traceable's platform works in the background even as application architectures change, development methodologies evolve, and new attack vectors and threats emerge.
Traceable supports REST, SOAP, gRPC, and GraphQL APIs. At a high level, the following points summarize the value add that Traceable provides:
Reverse engineers the schema using the traffic. Show the GraphQL operation instead of the URL.
Identify the sensitive data flowing in APIs across services and third-party APIs.
Conformance analysis with OpenAPI specification generation
Protection from malicious actors or threat actors for legacy and business logic attacks.
Identify vulnerabilities (Legacy/API specific/Business Logic) in APIs.
Identify any data exfiltration of sensitive data.
Deep forensic analysis tools
Identify gaps in your APIs before they reach production using Traceable's API Security Testing (AST).
Traceable brings your security and development teams together to monitor and protect your most important assets – your customers, applications, and data. Traceable also provides rich dashboards, reports, and many other features to monitor and protect applications and application users by using modern observability and machine-learning algorithms.
API Catalog
API catalog provides automatic and continuous API discovery for comprehensive visibility of all APIs, sensitive data, and risk posture even as your environment changes. Traceable helps the security team understand their API exposure by proactively identifying vulnerable APIs and sensitive data flow. The DevOps can identify issues in your staging or pre-production environment. API catalog can also help your compliance teams by providing a comprehensive view of all the APIs and track and audit the data flow across your infrastructure.
You can start experiencing the immediate value that Traceable provides by viewing the Discovered APIs and their associated risk score on the API Endpoints page. The API Endpoints page displays the number of internal and external APIs, the number of APIs that have been recently updated, and the number of APIs at risk. You can narrow the discovered APIs using various filters, for example, APIs having sensitive data, or only external APIs, and so on.
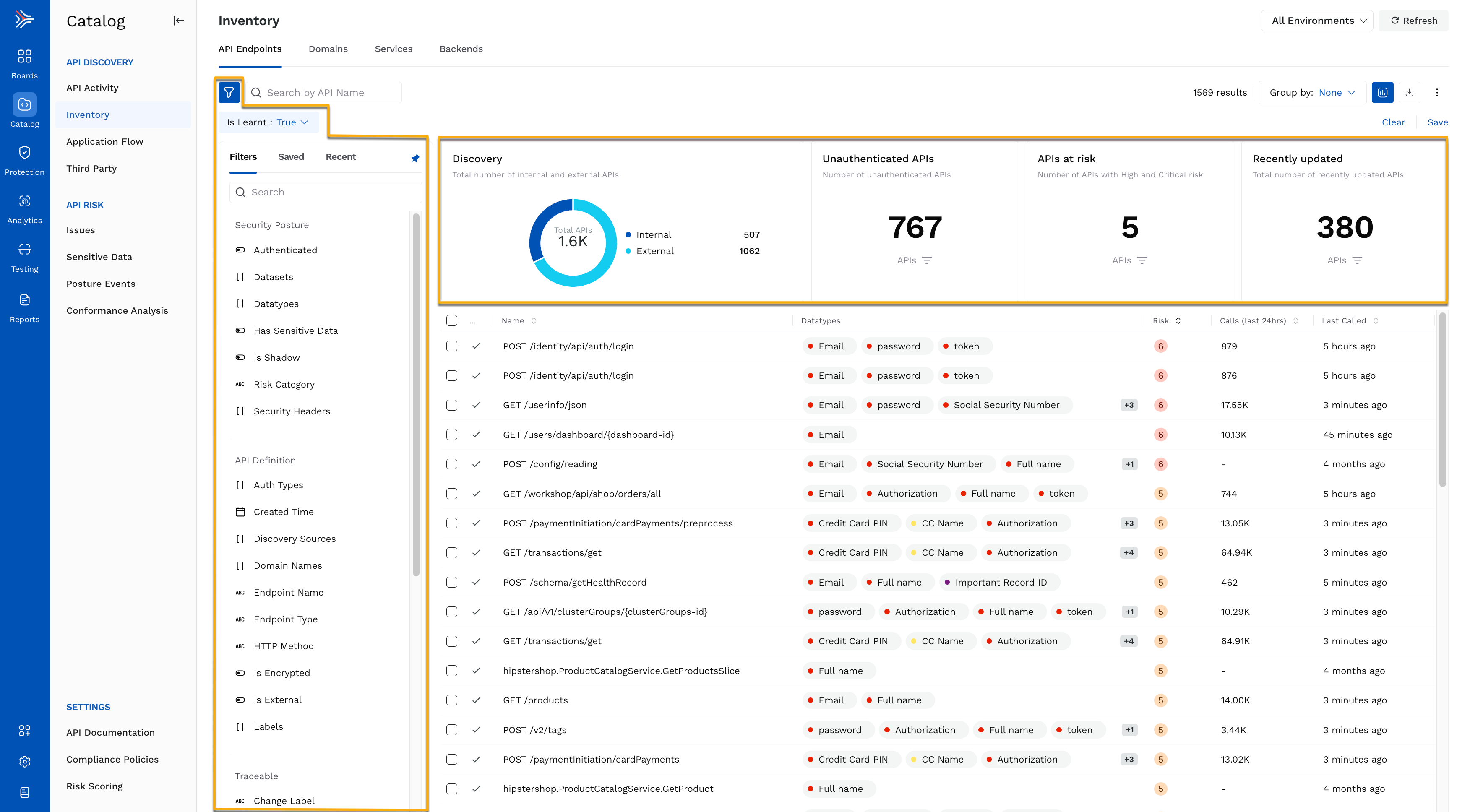
For more information on API Metrics, Events, Traces, and DNA, see Endpoint details. You can view more information on services and domains if you wish to dive deeper into the different options.
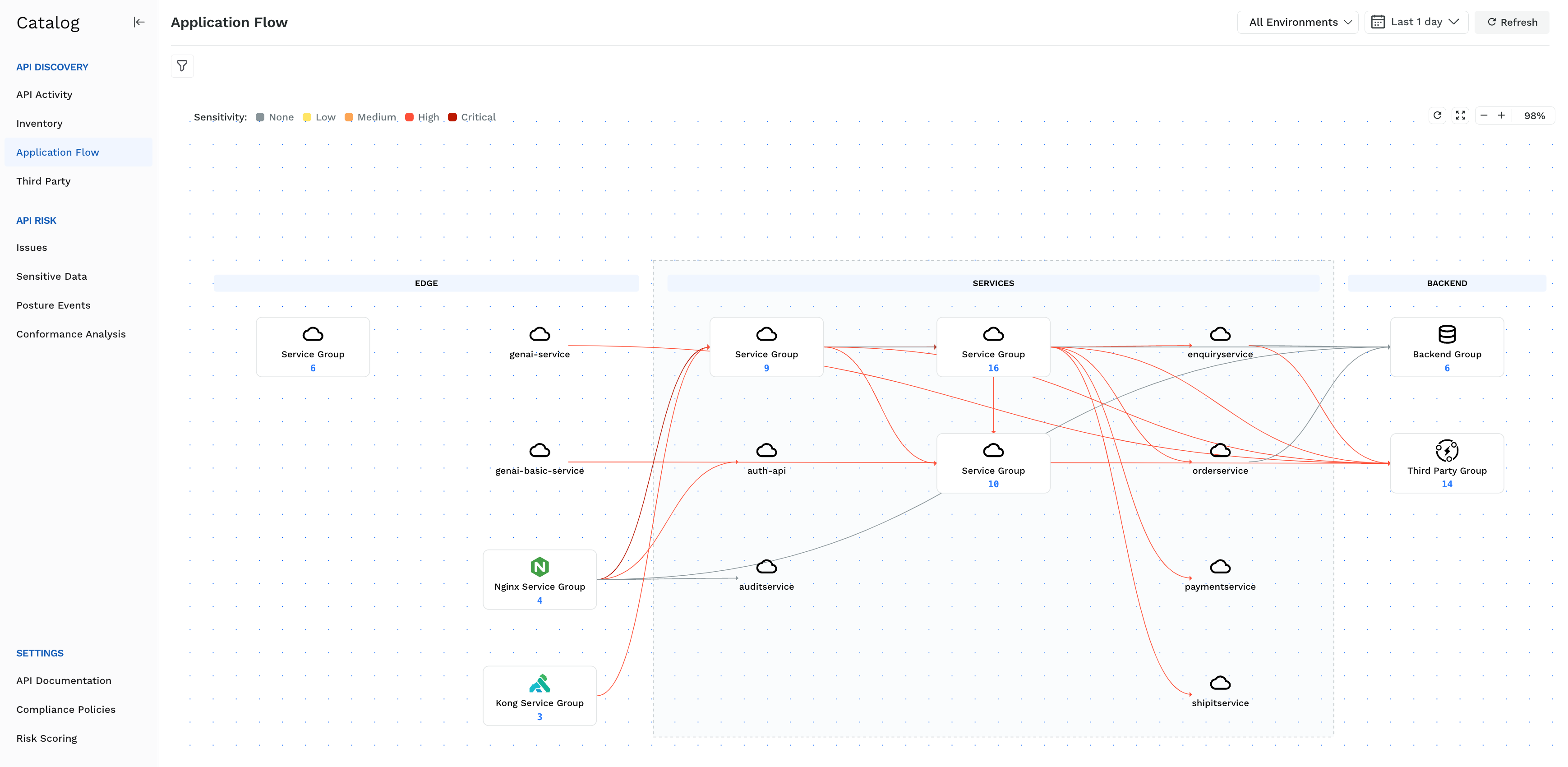
App Topology
The Application Flow shows the actual flow of traffic through multiple services. Real-time topology map shows API flows and interconnectivity between services (endpoints, internal, and 3rd-party). API Specifications offer more accurate specs than SWAGGER with real-time data from actual application usage.
Protect your APIs
There are different ways in which you can protect your APIs. Traceable automatically detects and blocks both known and unknown API attacks and identifies vulnerabilities. Built-in standards protect against OWASP Top 10 and OWASP API Top 10. You can also define your custom signature rules to block threat actors. These rules work in addition to the preconfigured rules. For more information, see Custom policy. You can choose to enable or disable rules individually. For more information, see Detection policies. You can also decide to exclude certain types of threats from being detected if you are confident they are not relevant to your environment.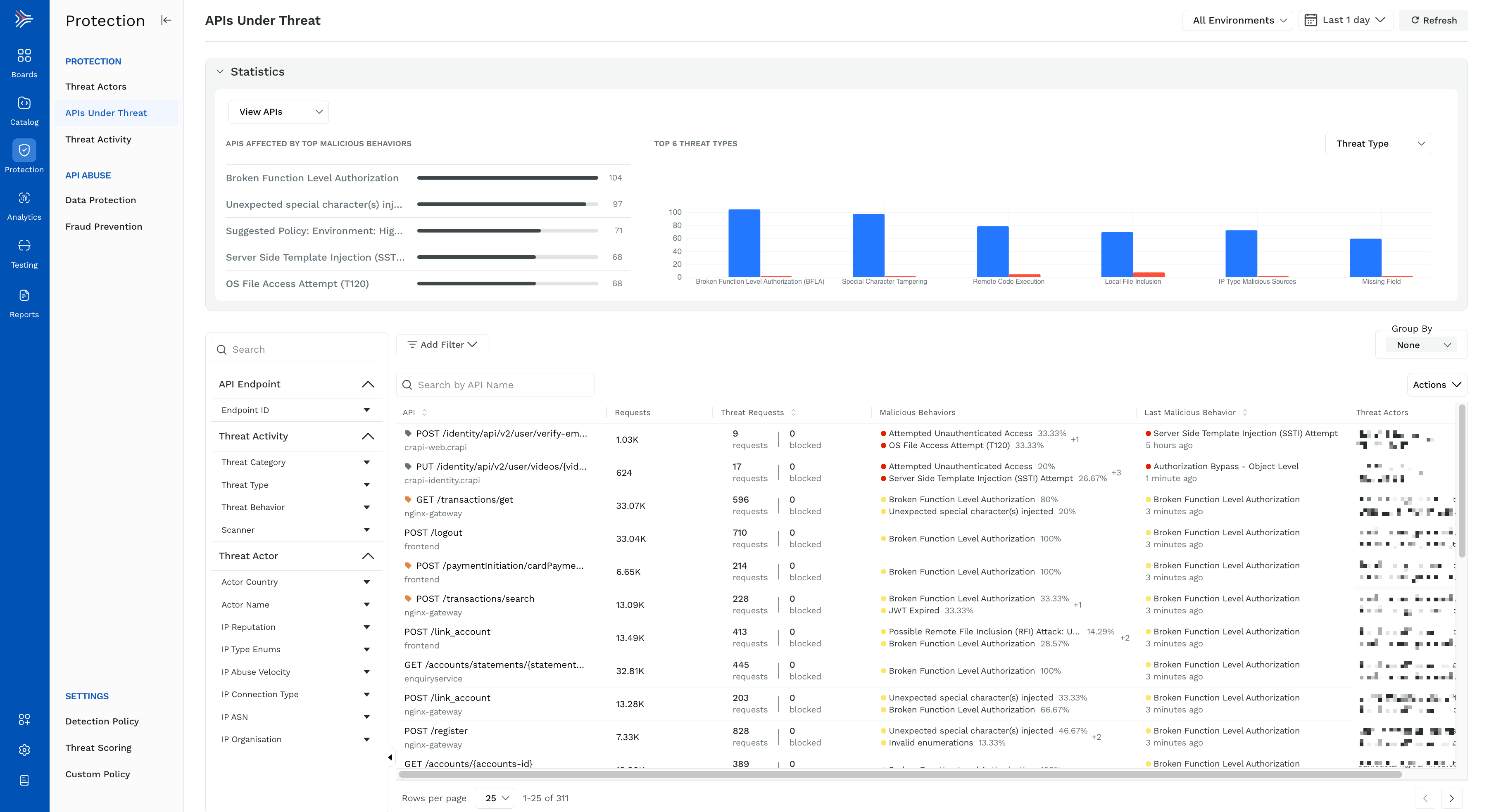
Traceable also provides an option to protect your API infrastructure from DDoS attacks by rate-limiting the number of requests. You can create rate-limiting rules from the Custom Policies section under Settings. For more information, see the Rate Limiting tab under Creating a Custom Policy. In addition to rate limiting, you can define rules to block an IP address range. For more information, see Custom Policy.
An important part of API security is to view and understand the different threat activities that threat actors generate. Traceable detects and displays different types of security events for anomalies and attacks. For more information, see Threat Activity.
Role-based Access Control (RBAC)
Traceable provides you with an option to create roles to provide access to different sections of Traceable. When you add your team members to Traceable, you can assign either of the roles to them. Defining the correct role for a user helps in the separation of duties. Traceable also provides role-based access control based on the environment. This provides you the flexibility to add the same user with different roles in different environments, allowing you granular control of their access. While Traceable provides the following roles out-of-the-box, you can define custom roles and select the permissions according to your requirements.
Account Owner — An account owner is a person who manages the Traceable account. For example, managing users, assigning privileges, licensing, and so on. There can be more than one account owner.
Security Admin — A security admin is typically a person who configures the security policies, investigates the attack information, monitors security events, and so on.
Security Analyst — A security analyst is typically a person who looks for security events and threats in the applications. They are typically part of the Security operations center (SOC) teams or part of product security teams and need to be aware of any security events as soon as they occur. Security analysts can, for example, work with events and vulnerabilities, configure notifications, and so on.
Developer — A person who wants to view the risks associated with the APIs that they have developed.
Global Reader — A global reader is a person who wants to see the data within the Traceable platform without performing any operational tasks.
Navigate to Settings (![]() ) > Team to create a custom role and add new team members to the Traceable platform. For more information, see Team and Roles - RBAC.
) > Team to create a custom role and add new team members to the Traceable platform. For more information, see Team and Roles - RBAC.
API Security Testing (AST)
Traceable's API Security Testing (AST) provides you with an option to test your APIs against various vulnerabilities and security gaps before they are deployed in a production environment. Application security testing gives your developers and product security engineers the right context about vulnerabilities so that they can prioritize the threats that may arise because of gaps in API specifications and implementation. Traceable’s AST is built on top of an API Catalog that provides the necessary context to run heavily contextualized tests, prioritize the mitigation of vulnerabilities, and build resilient systems.
The Application security testing suite performs specific tests on APIs. You can choose the types of tests you want to run. These tests intelligently leave those APIs from tests that have been inactive for a long time or have never been used. The following is a list of tests that you can currently run:
Server-Side Request Forgery (SSRF)
Security misconfiguration
JSON web token
Access control
Zed attack proxy (ZAP)
Insecure design
SQL injection
Authorization
Information disclosure
Remote code execution
Cross-site scripting
TLS
NoSQL injection
Business logic
Authentication
Get Notified
Traceable provides you with the capability to define rules for the types of events for which you would like to be notified. You can also decide the channel through which Traceable delivers event notifications to you. E-mail, Slack webhooks, or custom webhooks are currently supported. For more information, see the Notification section.