Traceable's Discovery provides a comprehensive understanding of your API ecosystem, offering both high-level and in-depth insights. It helps you discover and understand the APIs that pass through your API gateways, as well as Shadow and Zombie APIs. Such APIs could be a security risk to your organization. It identifies such unaccounted APIs, in addition to other APIs, within your organization’s infrastructure. It also helps your development and security teams stay up-to-date with changes in your APIs, while discovering new APIs side by side.
Using the Discovery, you can gain a clear view of both external and internal APIs, as well as authenticated and unauthenticated APIs. It also provides information about sensitive and non-sensitive data. In addition to displaying different kinds of information about your APIs, Traceable makes all this information actionable. For example, if you notice a specific API being accessed more frequently than expected, you can set rate limits on it. If you see an API being attacked or misused, you can block the user.
Using Traceable's Discovery, the security teams can view the OpenAPI specification that Traceable generates. You can also download and use the OpenAPI Spec for APIs in your other applications.
Traceable’s Discovery is a centralized inventory that provides high-level and deep knowledge of your API ecosystem. It helps you discover and understand APIs that pass through your API gateways, as well as Shadow and Zombie APIs. By automatically discovering and categorizing APIs across different services and environments, Traceable ensures that no API — whether internal, external, authenticated, unauthenticated, or third-party goes untracked.
How does this help?
Gain insights into request volumes, top API endpoints, and traffic volumes across the globe.
Gain details of each API, such as datatypes, number of calls, associated service, domain, auth type, etc.
Identify issues (security gaps) across API endpoints and address them according to your requirements.
Analyze security events across your APIs.
By consolidating API-related information into the Discovery module, Traceable helps you improve your API management while reducing the risks associated with misconfigured, unauthorized, and unmanaged APIs.
API Discovery
Traceable discovers edge APIs as well as internal APIs or services in your infrastructure. The API endpoint discovery is a multistep process in which Traceable builds a learning model by observing URLs, headers, requests, and response bodies in the span. Traceable initiates the API endpoint discovery process, identifying malicious or junk traffic, and automatically skips API creation. This helps by reducing the number of invalid APIs being created.
Note
Traceable discovers APIs only upon receiving successful response codes (between 2xx and 3xx).
API discovery is a multi-stage process. When Traceable completes the discovery process, it identifies an API as a combination of a method and a valid path. For example, GET /products/catalog is a different API from POST /products/catalog. The following are high-level stages of the discovery process:
A non-error code API response is detected. The API discovery process starts.
Traceable starts learning about the API and names it based on the method and URLs that it detects. You can later rename the APIs. For more information, see API Discovery.
APIs are categorized based on the types of users and the user requests.
Traceable continues to learn about the newly discovered APIs and starts detecting attacks and anomalies on them. During this period of learning, Traceable calculates and sets the thresholds for attack and anomaly detection.
The information gathered based on API Discovery includes:
All Assets
API Endpoints
Domains
Services
Backends
Repositories
.gif)
API Endpoints
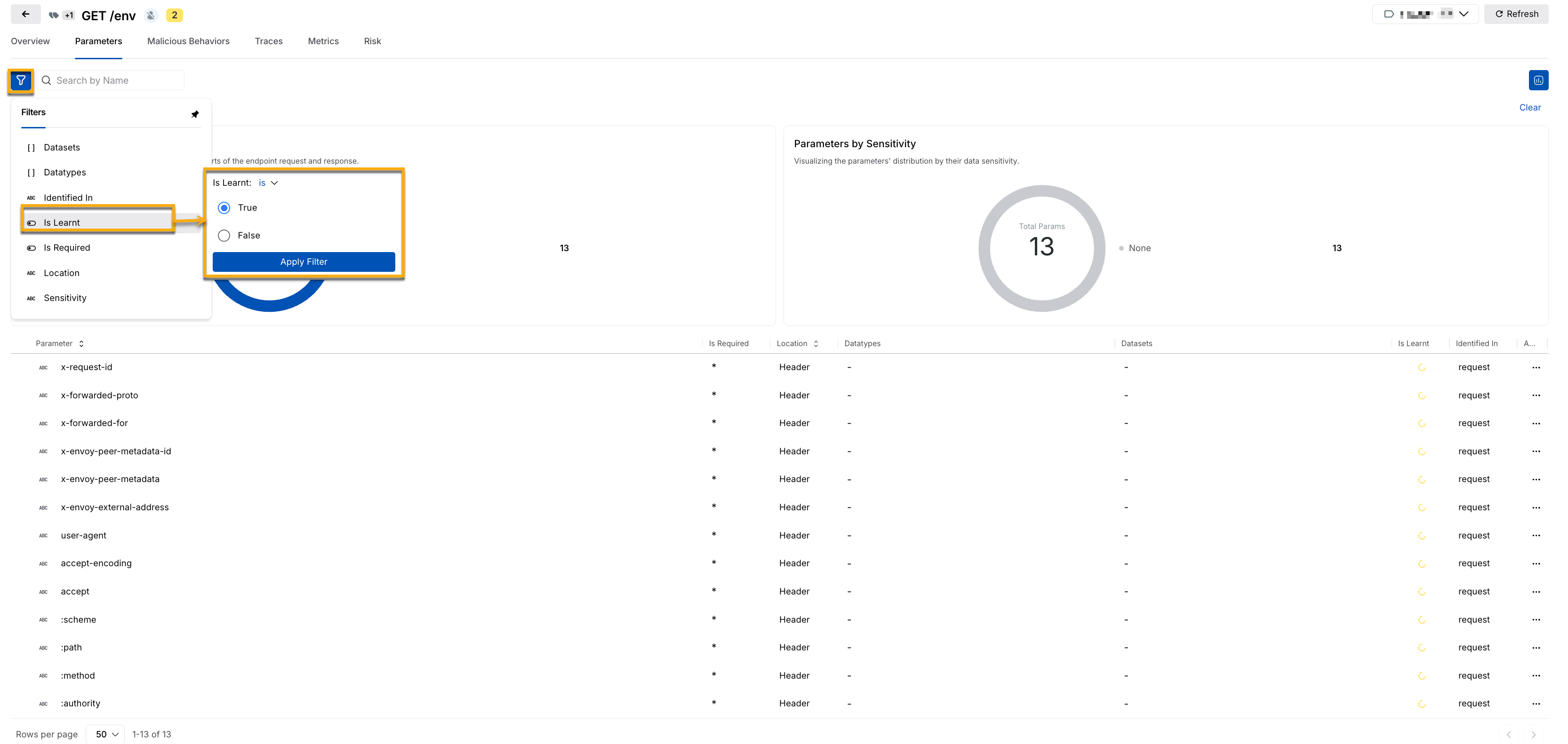
Traceable displays whether the various parameters of an API or the API DNA are learned or under learning by using the following icons:
.png) - Learning
- Learning.png) - Learnt
- Learnt
The Is Learnt filter is applied by default. You can set the value to True to view the Learnt, and False to view the Learning, as shown below.
API Risk
Discovery also provides insights into API Risk. Knowledge about various issues detected by Traceable, as well as Sensitive Data flowing through your APIs, helps in understanding the risk factors of your APIs. Traceable helps you by providing:
New Data Types
Sensitive Data Types
API Endpoints with sensitive data types
Issues are security gaps in your API definition that the threat actors may exploit to attack your API infrastructure. Traceable provides you with detailed information about issues and suggests mitigation options to address those gaps in APIs.