Updates (January 2025 to March 2025)
The topic has been created to explain how you can effectively regulate team members' access by assigning out-of-the-box or custom roles. While out-of-the-box roles provide permissions ranging from administration to read-only privileges, custom roles provide flexibility into user and role management. The topic explains the permissions, and access levels, and also highlights the steps to create custom roles and assign them to team members while inviting them.
RBAC stands for Role-Based Access Control and Traceable’s RBAC framework defines and allows you to enforce access policies that specify which users are authorized to perform which actions, such as accessing or modifying data, executing specific applications, or managing system configurations. This ensures efficient and authorized access to platform resources.
Out-of-the-box Roles
Traceable provides a few out-of-the-box roles, such as Account Owner, Security Admin, etc., for you to enforce RBAC. These roles, by default, are assigned specific levels of access within the platform, with the Account Owner being the super-user. You can also edit these roles (except Account Owner) to modify the privileges you wish to grant to a user. To ensure flexibility, Traceable also supports custom roles to tailor permissions and access settings according to your business requirements. This combination ensures precise access control while promoting secure collaboration between teams. For more information, see Roles.
Definitions
The following are a few terms used in the document:
Module-level Access — Permission to access platform functionalities, such as API Catalog, Protection, etc.
Administrative-level Access — Permission to access application settings, such as notifications, team, etc.
Base Permissions — Minimum set of privileges you wish to assign at either of the above levels.
Scope — The areas or extent to which the privileges should apply, for example, specific environments, endpoints, etc.
Permissions in RBAC are categorized into module and administrative-level access, providing a differentiation between functional and system-level controls. For example, you may want a user to access the API Catalog and Notifications on the Module and Administrative levels, respectively, but not other areas. This categorization enhances data security while preventing unauthorized access.
Traceable also allows Account Owners and users with the necessary privileges to invite team members and assign them out-of-the-box and/or custom roles. Assigning the correct role promotes the separation of duties, ensuring users have appropriate access for carrying out their responsibilities. Further, while inviting users, RBAC provides granular control through role scoping, allowing you to assign roles for specific environments, endpoints, and/or services. This allows the same user to hold different roles with distinct scopes while ensuring that users can only access the resources they need to carry out their responsibilities. For more information on inviting team members, see Inviting Team Members and Assigning Roles.
Note
Availability of scoping may vary for each role.
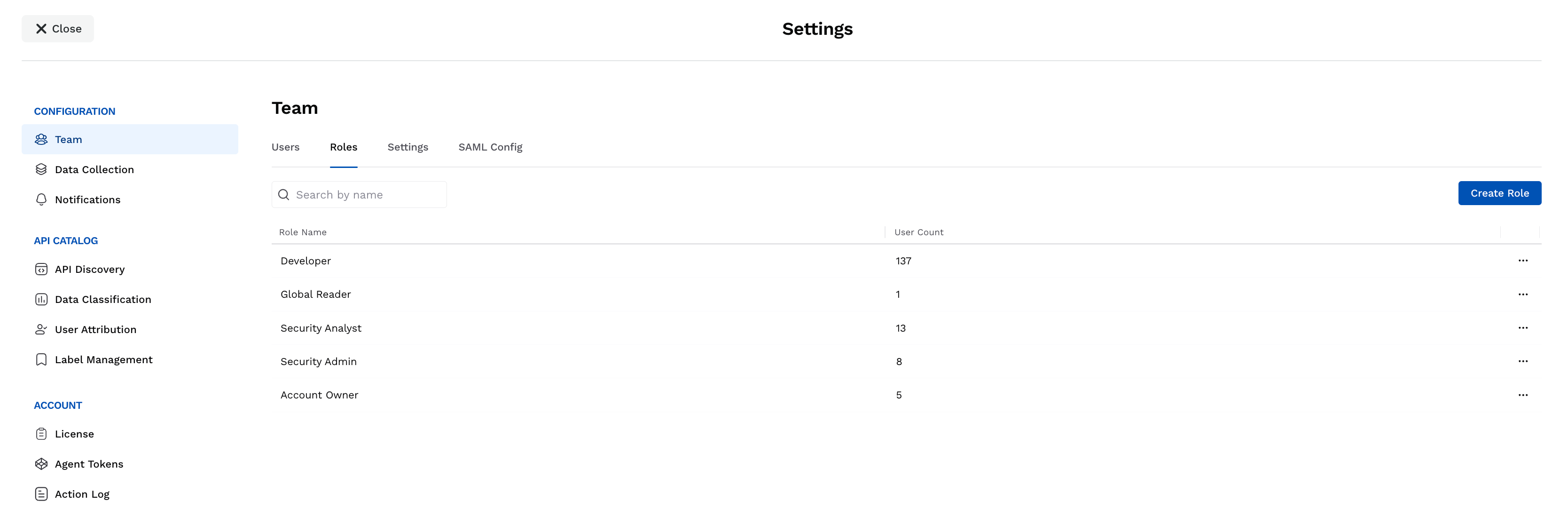
Roles
Traceable’s out-of-the-box roles provide a quick way to assign standard access levels for common use cases, ensuring immediate functionality. Custom roles, on the other hand, provide the flexibility to define unique permissions and scopes tailored to your business requirements.
Out-of-the-Box Roles
Traceable provides the following roles out of the box:
Role | Description |
|---|---|
Account Owner | An account owner manages the Traceable account, including managing users, assigning privileges, creating roles, licensing, etc.
|
Security Admin | A security admin configures and manages security policies, investigates attack information, monitors security events, etc. |
Security Analyst | A security analyst looks for security events and application threats. They are usually a part of the Security Operations Center (SOC) or product security teams. They must be aware of any security events as soon as they occur in your application. Security analysts can manage events and vulnerabilities, configure notifications, etc. |
Global Reader | A global reader is responsible for understanding the API risk and posture, threat activity, and incidents from runtime protection and understands how API testing maps to the vulnerabilities discovered in the pre-production environment. This is a read-only role that allows users to view and access the product to minimize inadvertent actions. They will then be able to prioritize vulnerabilities that need to be addressed based on overall exposure. Users or executives interested in viewing the product features and data, and do not want to get into the operational tasks can also leverage this role. |
Developer | A developer looks for risks or threats associated with the APIs that they have developed. |
While you can edit the above roles (except Account Owner) to modify the privileges according to your requirements, you can also create custom roles. The following section discusses the access levels in each of these roles.
Access Levels
Traceable provides role-based access control on the following levels:
RBAC Levels
Module-level Access — This refers to permissions for accessing specific functional areas within the Traceable platform. Each module is considered an independent unit, and you can grant or restrict access to the members while creating the role.
Purpose of module-level access — Focuses on providing access to particular features or components of an application, such as API Catalog and API Protection.
Example — An "Analyst" role may have access to the "Analytics" module but not the "API Testing" or "Sonar" modules.
Administration — Administration-level access refers to permissions for accessing specific user management or application settings. This level oversees the modules like integrations, user management, and data collection.
Purpose of administration-level access — Focuses on managing the system's operations, settings, and user activities.
Example: An "Administrator" role may have full access to all administrative functions, including creating users, assigning roles, managing integrations, and viewing system-wide notifications.
The following section explains the permissions in each of these levels.
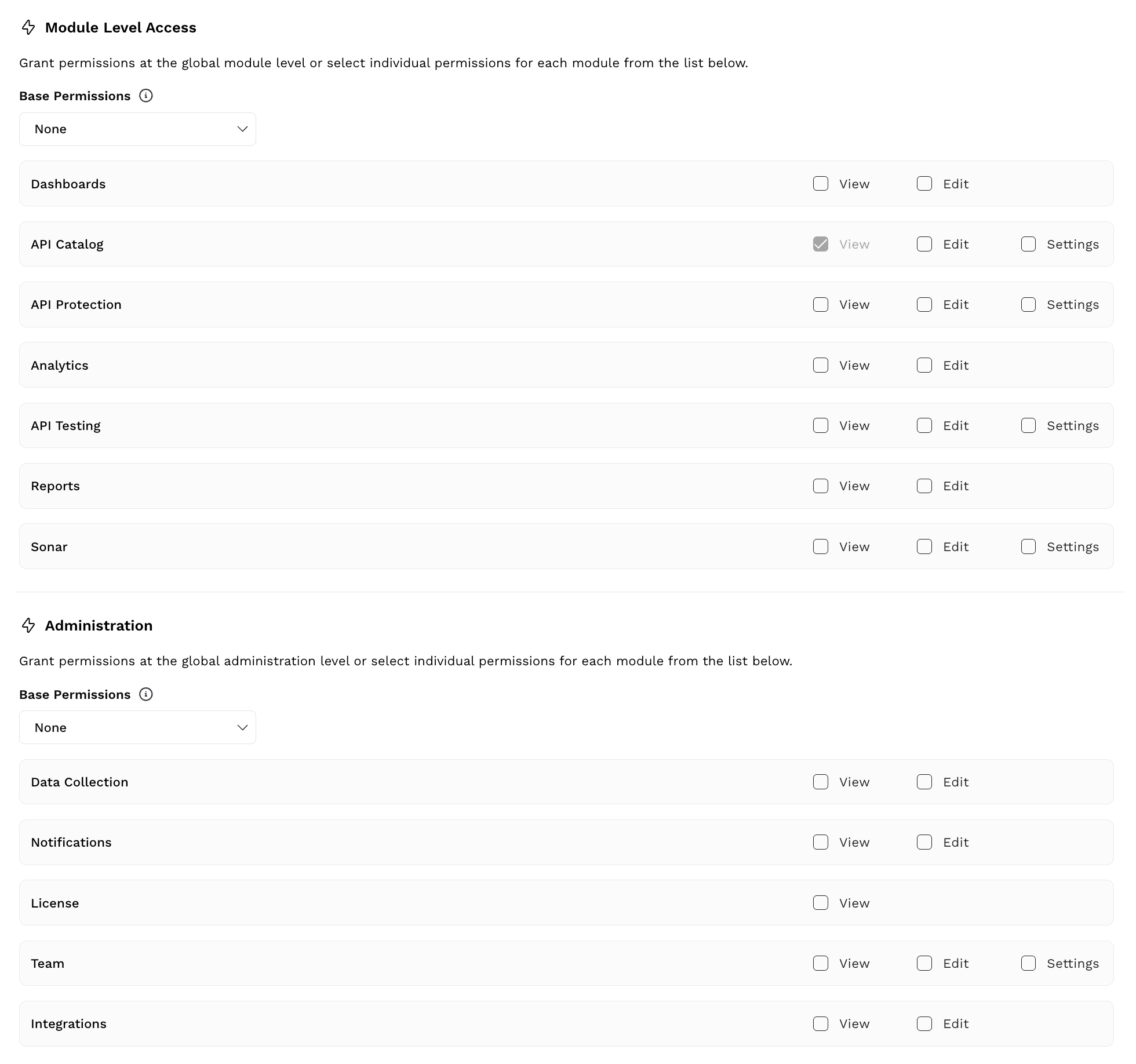
Permissions
In each of the above levels, you must define the Base Permissions as shown in the above screenshot.
What are Base Permissions?
Base permissions are a set of privileges that you can assign to a role. These privileges apply to all modules within a level. For example, when you select the View permission under Module-level Access, users assigned this role can only view all functional areas within the platform, such as Sonar and API Testing.
The Base Permission drop-down has the following values. You can select either of them according to your requirements:
None — Does not assign any privilege to users.
View — This option allows users to view the information in all sections except Settings in the modules. For example, under API Catalog, you can view the API Discovery and API Risk sections but not Settings.
View & Edit — This option allows users to view and edit the information in all sections except Settings in the modules.
View, Edit & Settings — This option allows users to view and edit the information in all sections (including Settings) of the modules.
Note
The privileges you select as part of the Base Permissions are inherited automatically for all pages or modules added to the Traceable platform in the future.
Additional Permissions
After selecting the base permissions for each level, you can also select additional permissions corresponding to a module according to your requirements. The following table explains these permissions:
Permission | Description |
|---|---|
View | Allows users to access and view the information shown in the modules without making changes. For example, users assigned this permission can view the API Catalog and Data Collection modules. This privilege applies to the modules you select in either of the levels mentioned above.
|
Edit (View & Edit) | Allows users to access, view, and modify the information shown in the modules. For example, users assigned this permission can mark a threat as internal under Protection or schedule a conformance analysis under Catalog. This privilege applies to the modules you select in either of the levels mentioned above.
|
Settings | Allows users to access, view, and modify the information shown in the Settings, along with other sections in the modules. For example, users assigned this role can create policies under Protection or modify risk-scoring configurations under Catalog. This privilege applies to the modules you select in either of the levels mentioned above. |
Note
The availability of the above permissions depends on whether or not the module contains the Edit or Settings option. For example, Dashboard does not contain the Settings option.
The following section discusses creating custom roles using the above access levels and permissions.
Creating Custom Roles
To create a custom role, navigate to Settings (![]() ) → Team → Roles tab, click Create Role, and complete the following steps:
) → Team → Roles tab, click Create Role, and complete the following steps:
Specify the role Name.
Specify the role Description.
Select the checkboxes for the following according to your business requirements:
Access to Call Detail Data — Traceable monitors and analyzes the API activity in your application system. Based on that analysis, traces and spans are shown for APIs. This unfiltered and unprocessed (raw) data is shown across various modules in the platform. Exposing this data to all users may lead to unauthorized access and hence, data misuse. You can select the View checkbox to show this raw data across the platform but to authorized individuals. For more information on the traces and spans, see Explorer.
Manage API Access — Traceable allows you to create API tokens to access its public APIs. Users can interact with these APIs to retrieve, send, and modify data and perform specific operations. This may lead to unauthorized access, misuse, and data leaks. You can select the Enabled checkbox to allow the generation of API tokens from the platform but to authorized individuals. For more information on API tokens, see Public APIs.
Manage Access to Issues — Traceable analyzes APIs in your application system and finds security issues (vulnerabilities) through live traffic, security testing, and compliance policies. Post-detection, these issues are shown across various modules in the platform. Exposing this data to all users may lead to information misuse or unauthorized debugging in the platform. You can select the View and/or Edit checkbox according to your requirements so that only authorized individuals can perform the necessary actions. For more information on these security issues, see Issues.
Select the permissions or checkboxes for the following modules according to your business requirements:
Base Permissions — The default set of privileges that you wish to assign to this role, as mentioned above. For more information, see Permissions.
Dashboards, API Catalog, API Protection, Analytics, API Testing, Reports, Sonar — The set of privileges you wish to assign to users over and above the base permissions, if any. For more information, see Additional Permissions.
Note
Traceable provides the View permission for API Catalog by default.
Select the permissions or checkboxes for the following administrative-level modules according to your business requirements:
Base Permissions — The default set of privileges that you wish to assign to this role, as mentioned above. For more information, see Permissions.
Data Collection, Notifications, License, Team, Integrations — The set of privileges you wish to assign to users over and above the base permissions, if any. For more information, see Additional Permissions.
Click Save.
Demo and Example
The following demo shows how to create a role that applies to the Testing team in your organization:
Traceable shows the saved roles in the Roles tab. For each role, Traceable also shows the count of users who have been assigned the role.
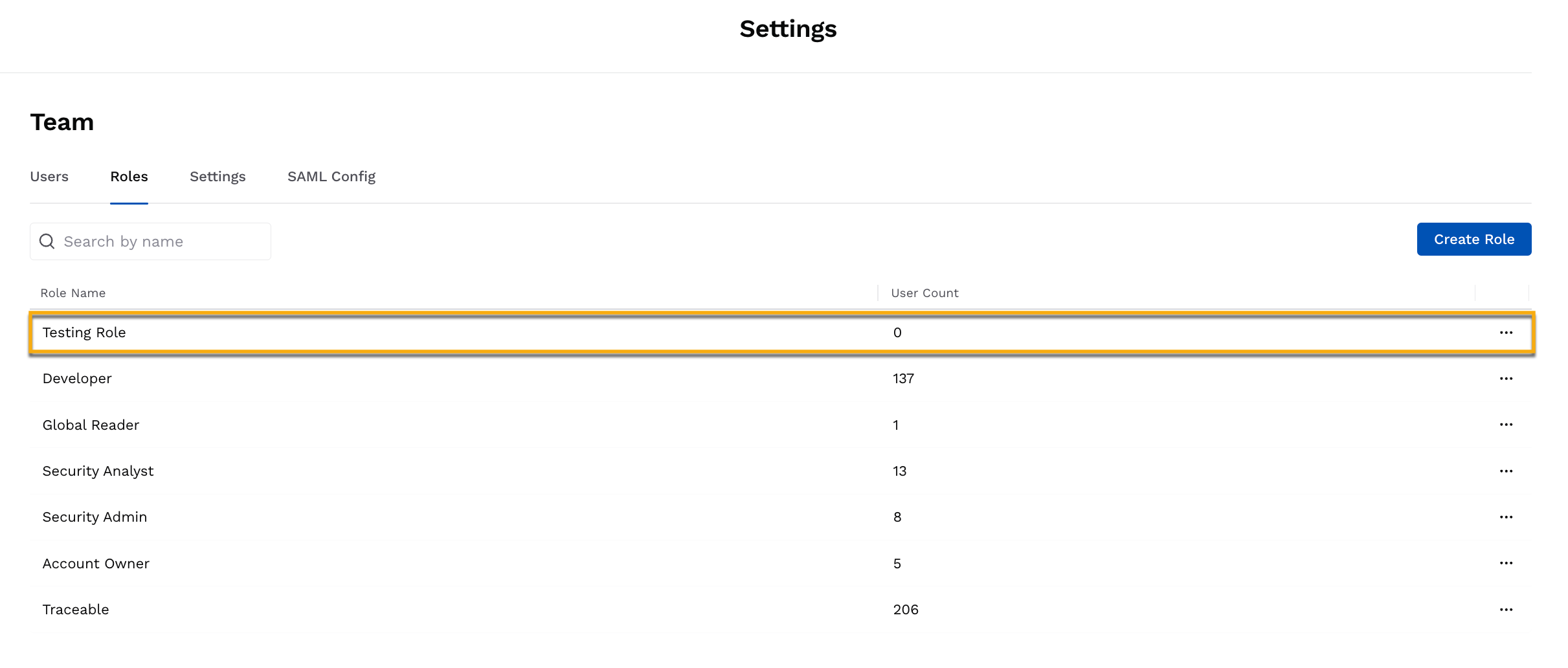
Saved Role
Additional Features
You can click the Ellipse (![]() ) icon corresponding to an out-of-the-box or custom role to perform the following actions:
) icon corresponding to an out-of-the-box or custom role to perform the following actions:
View — View the details of the role, such as the description and permissions.
Clone — Create a copy of the role with the same permissions and descriptions. This is useful when you wish to make minor modifications to the permissions in a role while creating a new one.
Edit — Modify the details of the role, such as description and permissions. See the above steps to do this.
Delete — Delete the role.
Note
You cannot delete a role if one or more users are assigned to that role.
The Account Owner role cannot be deleted.
A deleted role cannot be restored.
Inviting Team Members and Assigning Roles
Traceable allows you to invite any number of team members into your Traceable account. You can add a team member if you are the Account Owner or have the necessary Edit privileges on a Team level. While inviting a team member, you can choose the role you wish to assign and scope them to environments, endpoints, and/or services.
As a first step for inviting team members, Traceable recommends that you identify or create the role you wish to assign to the user. For more information on the roles and their associated permissions, see Roles. Once you have done this, navigate to Settings (![]() ) → Team → Users tab, click + Invite User, and complete the following steps:
) → Team → Users tab, click + Invite User, and complete the following steps:
Specify the Email of the user you wish to invite.
Select the Login Type through which you wish to invite the user.
Note
The user will be able to login to the platform only using the login type you select.
Select the Role you wish to assign to the user. The drop-down lists all the roles available under the Roles tab.
Select the Scope of the role. This limits the role to the specific areas you select. The following options are available for scoping:
All — Allows users to perform actions associated with the role across all environments, endpoints, and services.
Environments — Allows users to perform actions associated with the role only across the environment(s) you select.
Endpoints — Allows users to perform actions associated with the role only across the API endpoint(s) you select.
Services — Allows users to perform actions associated with the role only across the service(s) you select.
Note
The above options may vary for pre-defined and custom roles. For example, all of the above options are available for the Developer role, whereas only the All option is available for Custom roles.
Click Add Role to add multiple roles according to your requirements.
Note
Traceable performs an OR operation in case of multiple roles.
Click Invite User.
Demo and Example
The following demo shows how to invite a user who is assigned the Testing Role created above, along with the Security Analyst role for the default environment:
Upon invitation, the team member receives an email that they can use to sign up for the Traceable platform.
If you are the Account Owner or have the necessary Edit privileges on a team level, you can also perform the following actions for a user:
Edit — Modify the role or scope assigned to a user according to your business requirements.
Delete — Remove the user from the Traceable platform permanently.
To do so, click the Ellipse (![]() ) icon corresponding to a user, and select the necessary action.
) icon corresponding to a user, and select the necessary action.