Updates (July 2025 to September 2025)
July 2025 — Traceable has redesigned the Threat Actor page to provide you with a more intuitive experience and improved data exploration for analysis. For more information, see Threat Actors.
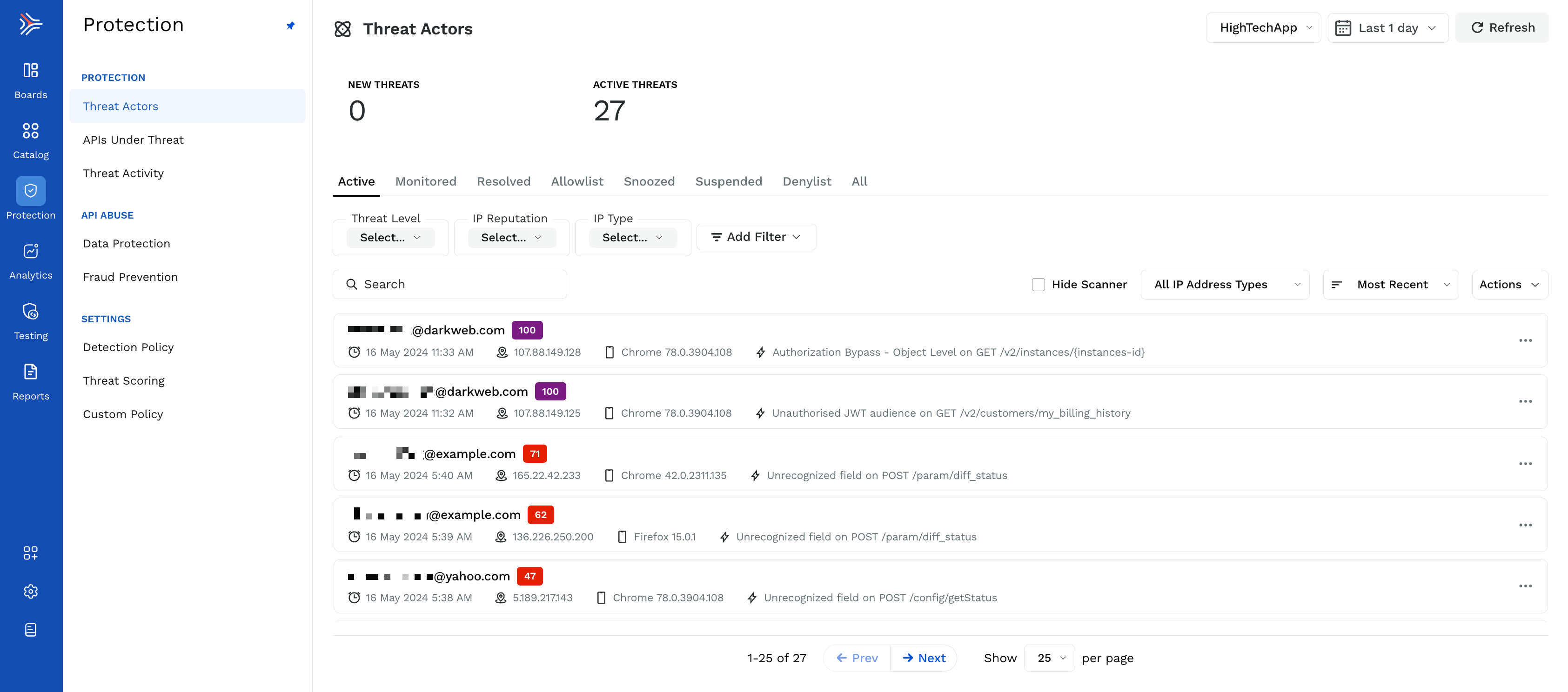
Threats are a prominent actionable category within Traceable. Threats typically mean an ongoing attack that needs attention and resolution. Traceable analyzes malicious activity by authenticated or anonymous users to identify threats. This threat activity information is combined with the previous activity report into an attack timeline.
Traceable identifies the threats by the threat actor. A user ID, such as an email ID, identifies a threat actor. If the user ID is unavailable, the threat actor's IP address is displayed. Threat actors are also associated with the reputation of the IP address they are using and the type of IP address. For example, the IP type could be anonymous VPN, public proxy, bot, etc. For more information about user ID, see User attribution.
Threat detection
Traceable starts security event detection by observing the traffic flow through the API endpoints to build the API Specification and insights for each parameter. These insights about the traffic flow are a combination of the baseline for a parameter type, value, and usage, such as patterns of request and response. Traceable, for example, observes the parameters within API endpoints, the traffic flow in authorized user sessions, the sequence of API calls, and so on.
To identify threats, Traceable establishes a baseline. Traceable then detects requests and responses where the parameters deviate from the established baseline. These deviations are identified as anomalies. These anomalies are further analyzed to identify if the anomalous activity is malicious. If it is an anomalous activity, a security event is raised. When Traceable detects anomalous behavior, it starts observing the user who triggered it. This user is now called a monitored user. Traceable closely monitors all further communication from this user.
Anomalies and security events have different severity levels based on multiple factors. Once the monitored user crosses a certain anomaly threshold level and displays some malicious behavior (security events are identified in their requests), they become a threat actor.
Navigate to the Protection → Threat Actor section to view all the identified threats. By default, the platform displays the active threats, with the threat actor having the highest threat score at the top. You can also sort the threat list based on the following:
IP address types by clicking on the All IP Address Types drop-down list.
Threat creation time or score by clicking on the Most Recent drop-down list.
Additionally, you can click on the Actions drop-down and download the threat list as a CSV file. While downloading, you can also select the number of rows you want to download from the list.
Threat actor mitigation
You can mitigate the threats by changing their state from the threat PROFILE page. The state that you select for the threat applies to it immediately. When you mitigate the threat by assigning it a specific status, the threat moves from the Active list or category to its new state. Based on Traceable's new inputs, you can re-categorize the threat to a different state. If the threat is put into a Suspend or Deny state, any further activity by these actors will be blocked once the blocking policy propagates into Traceable modules (~15 seconds).
The following table defines each state:
Threat Actor state | Description |
|---|---|
Active | The default state of the threat when Traceable reports it. |
Monitored | A user who has not attacked the system, however, is being monitored for suspicious activities. |
Resolve | Move the threat to this state if you are confident it is no longer a threat. This action resets Threat severity to 0. Traceable reports the threat actor again if it finds any malicious activity from it. In such a case, the threat is listed on the Active list. |
Allow | Move the threat to this state when you want to allow access to the system regardless of whether the actor's activities are malicious. |
Snooze | Move the threat to this state if you want to temporarily allow the threat actor. You can choose the snooze duration from a pre-defined time range, starting from one hour up to a week. |
Suspend | Move the threat to this state if you want to temporarily deny access to the threat actor. You can select the suspension duration from a pre-defined time range, starting from one hour up to a week. |
Deny | Move the threat to this state if you want to block access for a threat actor completely. |
If the users on the suspend or deny list use additional IP addresses, those IP addresses are also blocked. Traceable internally maintains a list of such IP addresses as ACL (access control list) policy. All such users are blocked from future access until their suspension is revoked or removed from the deny list.