Updates (January 2026 to March 2026)
February 2026 — Updated the topic according to the latest Traceable user interface. For more information, see Viewing Dashboard.
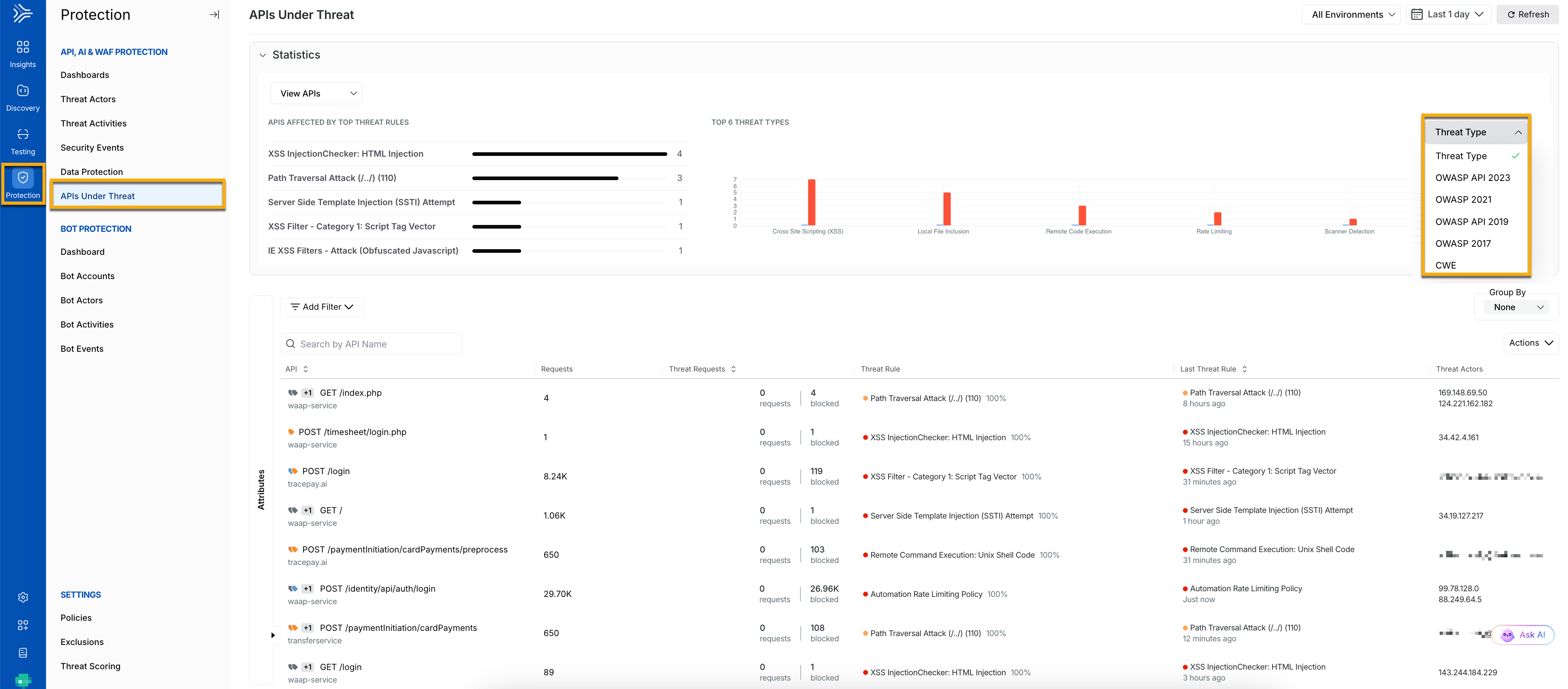
The APIs Under Threat page of API Protection provides information about the APIs under attack during your selected time period. It also provides details about the malicious behaviors and the corresponding threat actors.
APIs under Threat
What will you learn in this topic?
By the end of this topic, you will be able to understand:
The dashboard view of APIs under threat.
The overview and deep dive of the list of APIs under threat and their corresponding details.
Before you begin
Make a note of the following before proceeding:
Make sure the required protection policies are created. These policies enable Traceable to analyze API traffic and surface endpoints under threat.
To create a policy, navigate to Protection → Settings → Custom Policy, select the appropriate policy type, and click + Add Policy.
Viewing Dashboard
The Statistics section on this page displays the following information:
Top Threat Rules and the corresponding number of affected APIs.
Top 6 threat types.
The top threat types are further classified into different categories based on:
Traceable identified threat type
This categorization helps you identify threats based on OWASP's industry-standard definitions of API threats.
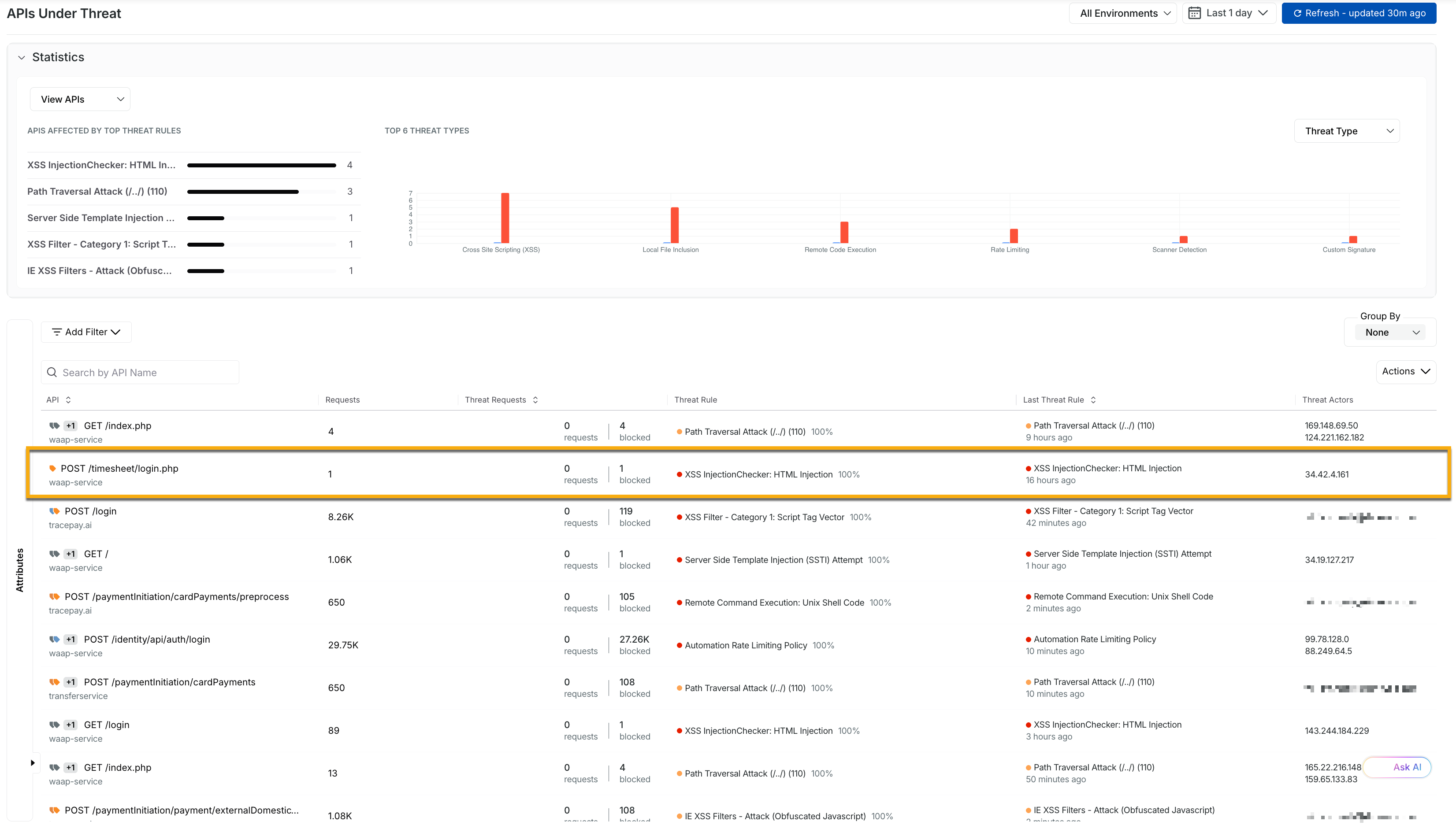
The following screenshot highlights the APIs under threat page, which comprises the list of APIs under attack, the Threat Rules, the total number of Threat Requests, and the Threat Actors involved.
List of APIs under threat
The page also displays the following for an API:
Total Request Count — The total number of API requests observed for the endpoint, covering all incoming traffic.
Threat Request Count — The number of requests identified as malicious, including both detected and actively blocked threat requests.
Threat Rule — The security rule that was triggered when a request matched a defined threat condition or policy.
Last Threat Rule — The most recent threat rule triggered for this endpoint, indicating the latest security event affecting it.
Threat Actors — The distinct malicious sources or entities identified during the API attack, representing the origin of threat activity.
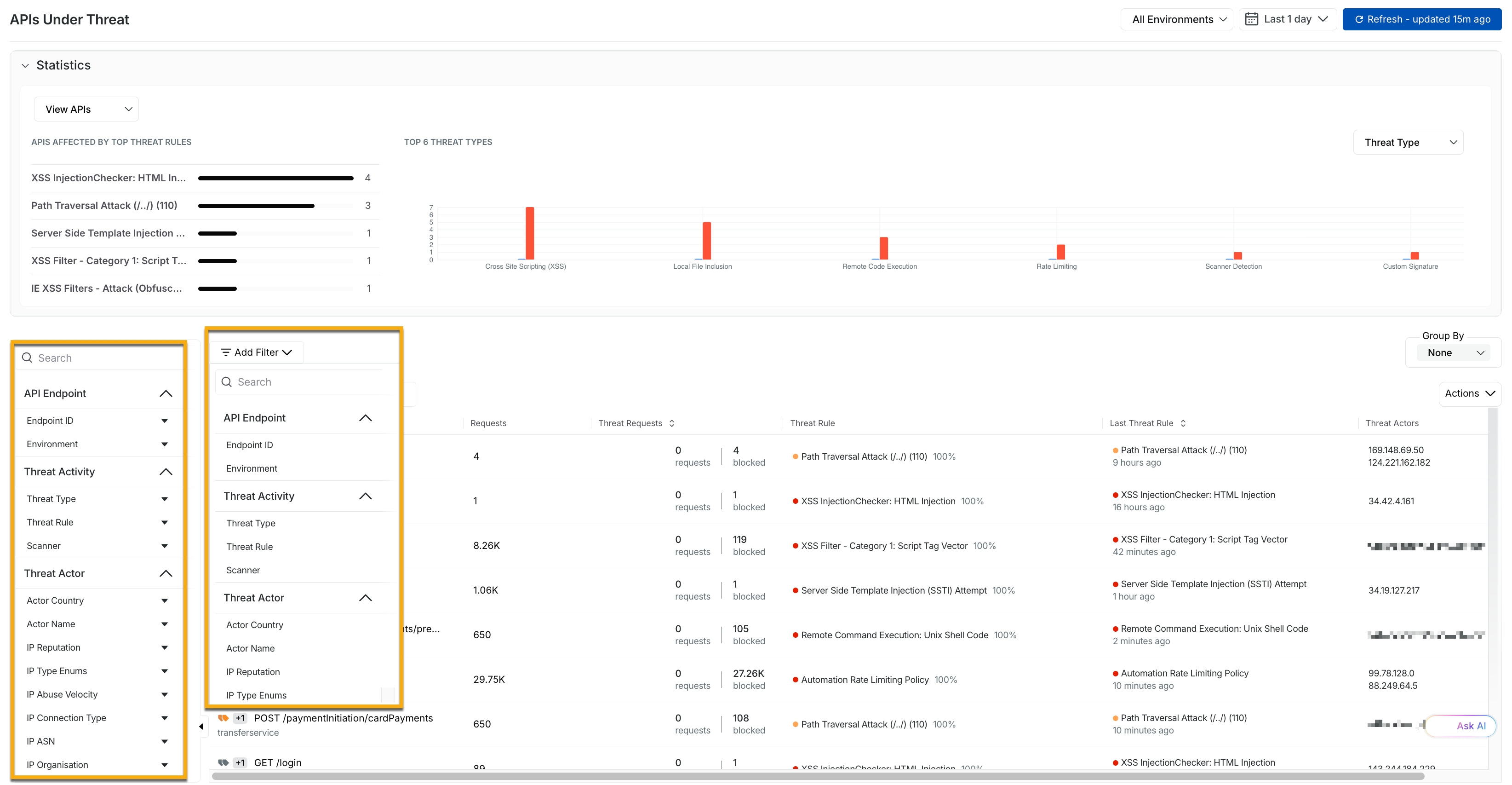
You can view more information about the API under attack by clicking the listed API Endpoint, for example, POST /cart. You can also click the Add Filter or choose from the Attributes on the left to fine-tune the displayed results according to your requirements. For example, Endpoint ID, Actor Country, and IP Organisation.
Attributes and Filters
Additionally, you can click the Actions drop-down and download the list of APIs under threat as a CSV file. While downloading, you can also select the number of rows you want to download from the list. If you wish to dive deep into each endpoint, you can click each endpoint and analyse different metrics. For more information, see API Endpoint Details.