Updates (January 2026 to March 2026)
February 2026 — Updated the topic to add environment-scoped enablement for auto-blocking. For more information, see Auto-blocking.
Traceable enables you to quantify API risk using threat scoring, thereby prioritizing investigations and automating defensive responses. Using threat scoring, you can assign customizable scores to anomalous behavior and security events, helping identify entities exhibiting suspicious or malicious activity. Based on the accumulated threat score, Traceable categorizes threat actors and can automatically enforce security actions.
What will you learn in this topic?
By the end of this topic, you will be able to understand:
How threat scoring quantifies API risk using anomalies and security events.
How to configure scoring values, severity levels, and threat score thresholds.
How severity adjustments based on response codes affect scoring.
How auto-blocking works and how it is enforced across environments.
How exclusions and IP allowlisting impact enforcement while preserving detection.
Understanding Threat Scoring
Anomalies are deviations from normal behavior. By analyzing these behavioral deviations along with known Common Vulnerabilities and Exposures (CVE) patterns, Traceable identifies potential security events early in the attack lifecycle. When a user begins exhibiting anomalous activity, Traceable classifies them as a monitored user. At this stage, the user is observed, but no confirmed malicious action has occurred. If the user later attempts an attack, Traceable reclassifies them as a threat actor.
To evaluate this progression from anomaly detection to confirmed malicious intent, Traceable uses a threat scoring framework. Threat scoring continuously assesses user behavior, anomalies, and attack signals to determine risk levels and trigger appropriate security actions. The following flow chart provides a high-level overview of the threat scoring process:
.png)
Threat Scoring Flowchart
Threat Scoring Flow
Threat scoring calculates risk by combining:
Anomaly scores
Security event scores
The cumulative score determines the threat actor's severity classification and drives automated enforcement decisions.
Anomaly score
You can configure a score for an anomaly. This score is the same across all detected anomaly types. The default value is 1. You can set a value between 1 and 10. Every time a user generates an anomaly, its score increases by the configured value. For example, if you put the anomaly score to 2 per anomaly and the user generates 5 anomalies, the total score would be 2*5 = 10.
Security event score
Security events are categorized into four different levels: critical, high, medium, and low. You can customize the score for each event category to a value between 1 and 10. The default values are:
Critical - 10
High - 3
Medium - 2
Low - 1
The security event score is added to the threat actor's threat score. A threat actor may create security events on different APIs. APIs can be high, medium, or low risk. You can view the different API categories and their risk scores on the API Endpoints page. You can choose which types of security events to include in a threat actor's threat score. You can choose from the following:
All events — Add the security event score of all the security events that the threat actor creates, irrespective of the API (critical, high, medium, or low risk).
Events affecting high-risk APIs — You can select the security events that affect only the high-risk APIs. This enables you to focus on threats to high-risk APIs.
Severity Adjustment Based on Response Codes
There may be cases where Traceable detects an attack attempt, but the backend service rejects the request and returns an error response code. In such scenarios, the backend service may already be resilient enough to handle the malicious input. You may not want the threat score to increase when the backend service has successfully mitigated the attempt.
One way to identify such cases is by evaluating the response status code. You can configure an error status code regex in Traceable. When the response status code matches the configured regex, you can choose to:
Ignore that request for scoring.
Downgrade the severity by one step.
Downgrade the severity by two steps.
For example, if the current severity is Critical and you downgrade by one step, the new severity will be High. In such a case, the most recent high-severity score will apply. You must click Save for the changes to apply.
Increase scoring for IP addresses
Traceable tracks the reputation of individual IP addresses. You can view the IP reputation indicator by navigating to API Protection → Threat Actors. Corresponding to the threat actor, you can view the IP reputation of that threat actor, as shown in the screenshot below:
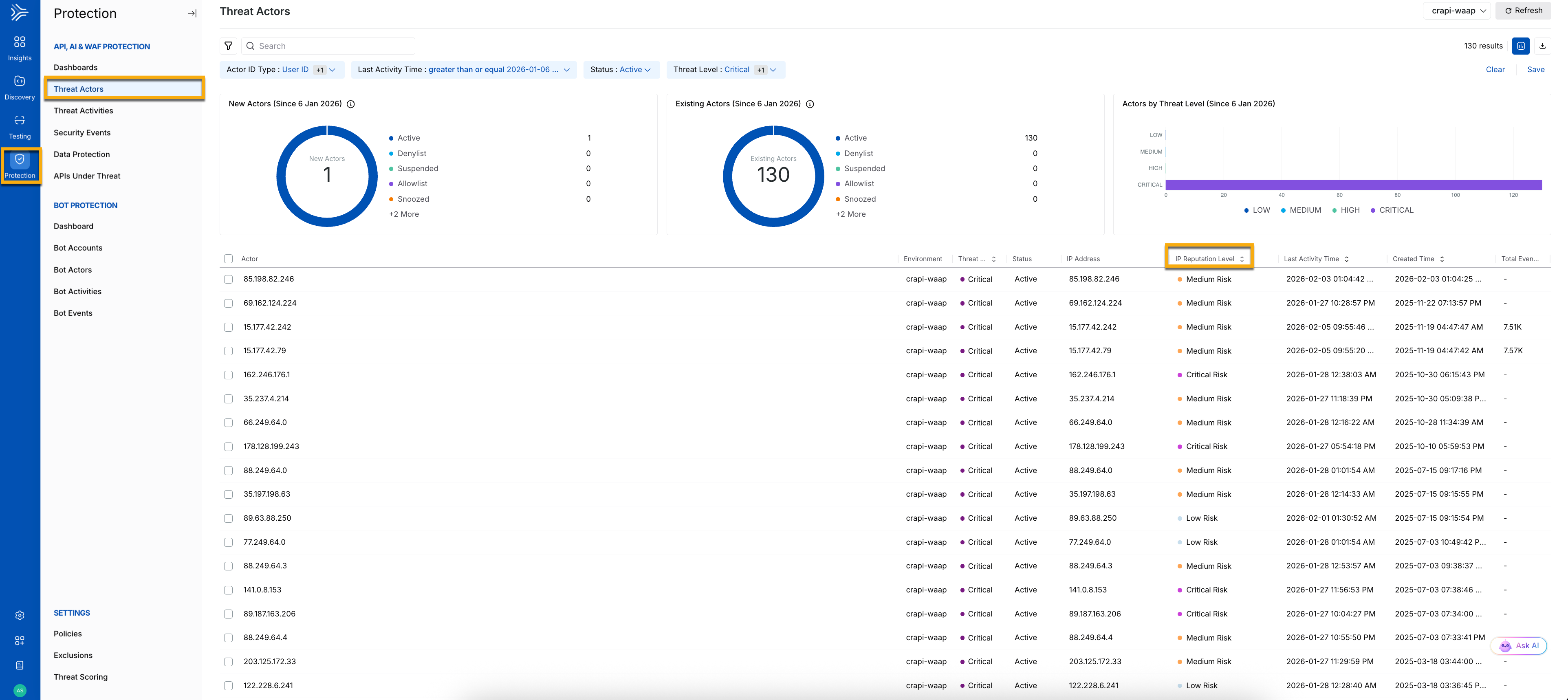
Threat score threshold
The addition of anomaly and security event scores gives the threat actor score. The threat actor score graph shows the active threat actors over the last seven days. You can configure the threshold for categorizing the threat actors in the following four categories:
Low — Default threat score between 0 and 10.
Medium — Default threat score between 11 and 20.
High — Default threat score between 21 and 75.
Critical — Default threat score between 76 and 100.
You can move the slider in the Threat Actor Score graph to adjust the scores according to your requirements. For example, if you want the threat actor category to start at medium, move the first slider (on the left-hand side) to 0. This categorizes threat actors into only medium, high, and critical categories.
.png)
Threat Scoring
Auto-blocking
Auto-blocking is an automated enforcement mechanism that stops malicious users from continuing activity once their risk level reaches a critical threshold. Threat scoring continuously evaluates anomalies, behavioral deviations, and confirmed attack signals. As activity escalates and the accumulated score reaches the Critical threshold, the user is automatically blocked without requiring manual intervention. This capability becomes particularly valuable during an active attack. Every additional malicious request increases the potential for data exposure, service disruption, or abuse. Auto-blocking ensures that enforcement happens at the exact moment risk crosses the defined limit, reducing response time and limiting impact.
Auto-blocking is configured per environment scope. You must decide whether enforcement applies to a specific environment or across all environments in your organization. This flexibility allows you to control operational risk. For example, you may want to observe and tune scoring in non-production environments before enabling enforcement in production. Careful tuning of scoring rules, validation of detections, and review of user behavior help ensure that automated enforcement targets genuine threats while minimizing false positives. To configure auto-blocking, navigate to API Protection → Settings → Threat Scoring, define the appropriate score thresholds, and enable Auto-blocking for the desired environment.
Note
A change in the scoring applies to all future security events and anomalies.
Auto-blocking is triggered when a user’s threat score reaches the configured Critical threshold. Ensure that the Critical score in the Scoring tab is configured correctly to avoid unintended blocking or missed threats.
Environment scope
Auto-blocking is environment-scoped. You can enable auto-blocking for:
A specific environment — Auto-blocking is applied only to the selected environment. Traffic in other environments remains unaffected, maintaining strict isolation across environments, for example, staging, testing, and production. This approach is ideal for validating enforcement behavior in a controlled setup before broader rollout, as scoring thresholds, exclusions, and enforcement actions are limited to that environment. To prevent unintended impact, Traceable displays a confirmation alert when enabling this option.
All environments — Auto-blocking is applied across every environment, ensuring a consistent threat response and centralized risk management across the platform. This approach is ideal when you wish to enforce a uniform security posture globally. Since this option applies across the platform, Traceable prompts you to confirm your selection, as shown below.
.png)
Exclude Users
Auto-blocking automatically restricts a user once their threat score reaches the configured critical threshold. This is particularly useful during active attacks on your API infrastructure. You may also choose to take no automated action. Enforcement is triggered based on the critical score defined in the Scoring tab. In some environments, specific identities must continue operating even if their threat score becomes vital. The Exclude Users capability allows you to define one or more regular expressions that match particular user identities. When a user matches an exclusion rule:
Threat scoring continues.
Anomalies and events are still recorded.
The user may still be classified as Critical.
Auto-blocking is not applied.
For example, a regular expression can exclude all users from specific domains, such as traceable.ai, whose usernames follow a defined pattern. These users would not be blocked, regardless of their threat score. For more information, see Exclusions.
.png)
IP Address Allowlist
An IP address allowlist serves as a policy-level enforcement override in Traceable and is configured through Custom Policies. When you create a policy for an IP range, such as a Custom Signature or Malicious Source policy, and set the action to Allow, you explicitly instruct Traceable to permit traffic from that IP range at the enforcement layer.
In essence, this means that blocking controls defined in other custom policies do not apply to traffic originating from the allowlisted IP range. Requests from those IP addresses are not blocked at the policy layer. This behavior also extends to auto-blocking. Even if a user or threat actor associated with an allowlisted IP reaches the Critical threat score threshold, enforcement actions are not triggered for traffic from that IP range. It is essential to distinguish between enforcement and detection. Allowlisting suppresses blocking actions, but it does not disable monitoring. Threat scoring continues, anomalies may still be identified, and security events are still generated. You retain complete visibility into activity from the allowlisted IP range; only enforcement actions are overridden. Out-of-the-box detections configured under Protection → Settings → Policies remain active, and custom signature policies continue to evaluate requests. For more information, see Custom Policies.