Updates (April 2025 to June 2025)
May 2025 — Updated the page to add information about configuring scopes as part of user attribution.
Older Updates
March 2025 —
Updated the page to highlight the revamped user interface and steps for configuring user attribution and generating previews.
The topic now has demos, examples for each authentication scheme, and a section on how Traceable processes rules.
User Attribution is the process of identifying a user ID, role, and other custom attributes. Once Traceable identifies these attributes, it is easier to associate them with the user action. This feature is also required to attribute the user requests across multiple user sessions.
Why is User Attribution Necessary?
User attribution is necessary as IP addresses can be shared, spoofed, or frequently changed. Correctly configured user attribution helps Traceable visualize user activity across devices and identify the user even in a shared network environment.
How does User Attribution Help?
Correctly configured user attribution helps identify threat activities and prevent fraud. In the absence of user attribution:
To understand a user’s activity, you would have to search through many sessions and IP addresses and stitch the data together.
Only the IP address, not the user ID, will be visible in the UI.
Types of User Attribution Schemes
You can configure user attribution using either of the following authentication schemes:
Authentication Scheme | Description |
|---|---|
Basic | Configuration for detecting the user ID from the basic authentication schema using the authorization header. |
Token-based | Configuration for detecting the user ID, role, scope, auth type, and custom attributes from the JWT authentication schema using either the header or Cookie. |
Custom | Configuration for detecting user ID, role, scope, auth type, and custom attributes from a custom authentication schema using headers, tokens, or credentials. |
Previewing User Attribution Configuration
While configuring user attribution, you can also see a preview of the rule based on the attributes you selected. Using this preview, you can verify that the transformations work as expected and the attributes are being extracted according to your requirements. The preview can be generated in either of the following ways:
Matching Spans (default) — Traceable automatically checks for any available spans according to the attributes and configurations you specify. If the spans are available, Traceable extracts the attribute values and displays the final result. At this time, you can also view the values extracted at each step of the configuration.
Note
This method is available only when spans are non-obfuscated and non-redacted.
File Upload — If the spans are unavailable due to obfuscated or redacted data, Traceable allows you to upload a
.harfile and generate a preview based on that file. Traceable, according to the file, extracts the attribute values and displays the result. Similar to the matching spans method, you can view the values extracted at each step of the configuration.
For more information on configuring user attribution and generating previews, see the section below.
Configuring User Attribution
To configure user attribution, navigate to Settings (![]() ) → User Attribution → User Attribution tab, click + Add User Attribution, and based on the authentication scheme you select, complete the steps in the following tabs.
) → User Attribution → User Attribution tab, click + Add User Attribution, and based on the authentication scheme you select, complete the steps in the following tabs.
The basic authentication method uses the authorization header for transmitting user credentials, such as the user ID and password. These credentials are encoded using the Base64 encoding. This encoded string is used in the authorization header of an API request, allowing Traceable to identify the user using the credentials. When you select this method, Traceable uses the authorization header in this API request by default and attributes the user ID.
To configure basic authentication, complete the following steps:
Step 1 — Define the authentication scope
Specify the Name.
(Optional) Specify a Description for the configuration.
Select the Environment in which you wish to apply the configuration.
Select the Services on which Traceable should apply the configuration. You can select all or specific services from the drop-down according to your requirements.
(Optional) Specify the URL Regex if you wish to provide a granular scope for user attribution.
Click Next.
Note
Traceable shows a preview upon rule configuration in the next step.
Step 2 — Define the authentication attributes
(Optional) Select the check box if you wish to Obfuscate the user ID value post-attribution, within the platform.
(Optional) Click + Add Condition, and select and specify the location, key, operator, and value based on which you want Traceable to check the spans for a match. If a span satisfies the condition, Traceable further evaluates the remaining configurations.
Select the Location and specify the key where Traceable can find the user ID. While Traceable specifies this configuration by default based on the commonly used values, you can modify it according to your requirements.
(Optional) Click + Add Value Transformation to add either of the following custom transformations:
Regex Capture Group — This transformation enables you to extract specific parts of a string or value that match the pattern you define.
Base64 Decoder — This transformation enables you to convert encoded Base64 data back to its decoded or original format.
While Traceable pre-adds some default transformations, you can add custom transformations. Traceable evaluates these transformations in order, from top to bottom.
Note
While you can modify the values, if any, in the pre-added transformations, you cannot reorder them. You can only reorder custom transformations according to your requirements.
Click Reload in the Preview Attributes section on the right. Post-reload, click Generate Preview to view the User ID extracted by Traceable. You can also click View Details to see the values returned corresponding to each attribute you configured above.
Click Submit.
Demo and Example
The following demo shows how to configure basic authentication for extracting the user ID. For example, if you consider the header as Authorization: Basic am9obi5kb2VAZ21haWwuY29tOmpvaG4uZG9lLnNlY3JldA==, then upon evaluation, Traceable returns john.doe@gmail.com as the user ID.
Note
The above header is for reference purposes only.
The token-based authentication method uses a token to transmit the user ID, role, scope, and other information. When setting up this method, you must specify conditions for Traceable to extract and transform the JWT token and define attributes according to your requirements. This authentication method is secure and scalable for setting up user attribution as it embeds the user's ID, role, and scope within the token, which the server can easily verify.
To configure token-based authentication, complete the following steps:
Step 1 — Define the authentication scope
Specify the Name.
(Optional) Specify a Description for the configuration.
Select the Environment in which you wish to apply the configuration.
Select the Services on which Traceable should apply the configuration. You can either select all or specific services from the drop-down according to your requirements.
(Optional) Specify the URL Regex if you wish to provide a granular scope for user attribution.
Click Next.
Step 2 — Define the conditions to extract and transform the JWT token
(Optional) Click + Add Condition, and select and specify the location, key, operator, and value based on which you want Traceable to check the spans for a match. If a span satisfies the condition, Traceable further evaluates the remaining configurations.
Select the Location and specify the key where Traceable can find the JWT token. While Traceable specifies this configuration by default based on the commonly used values, you can modify it according to your requirements.
(Optional) Click + Add Value Transformation to add either of the following custom transformations:
Regex Capture Group — This transformation enables you to extract specific parts of a string or value that match the pattern you define.
Base64 Decoder — This transformation enables you to convert encoded Base64 data back to its decoded or original format.
JSON Path — This transformation enables you to navigate and select a specific key within a nested JSON structure.
While Traceable pre-adds some default transformations, you can add custom transformations. Traceable evaluates these transformations in order, from top to bottom.
Note
You can modify the values, if any, in the pre-added transformations and reorder them according to your requirements.
Do one of the following according to your requirements:
If you use the default values Traceable defines, click Generate Preview in the Preview Attributes section on the right. This shows the payload and details Traceable extracts from the JWT token. You can also click View Details to see the values returned corresponding to each step above.
If you modified the values above, click Reload in the Preview Attributes section on the right. Post-reload, click Generate Preview to view the JWT Token extracted by Traceable. You can also click View Details to see the values returned corresponding to each attribute you configured above.
Click Next.
Step 3 — Define the authentication attributes
From the list of available attributes, select the one(s) you wish to add. Depending on the attribute you select, complete the following steps:
User ID/User Role/User Scope/Custom:
(Optional) Select the check box if you wish to Obfuscate the value post-attribution, within the platform.
(For Custom only) Specify the Key (Attribute Key) you wish to use as part of the authentication process.
(Optional) Click + Add Condition, and select and specify the location, key, operator, and value based on which you want Traceable to check the spans for a match.
Specify the Claim Location in Token (JSON Path) where Traceable can find the attribute.
(Optional) Click + Add Value Transformation to add either of the following custom transformations:
Regex Capture Group — This transformation enables you to extract specific parts of a string or value that match the pattern you define.
Base64 Decoder — This transformation enables you to convert encoded Base64 data back to its decoded or original format.
JSON Path — This transformation enables you to navigate and select a specific key within a nested JSON structure.
You can also reorder the transformations according to your requirements. Traceable evaluates them in order, from top to bottom.
Repeat the above steps to add one or more attributes, or complete the steps below to add the Auth Type attribute, according to your requirements.
Auth Type: Select the authentication type from the drop-down list according to your requirements. You can also create a new one according to your requirements.
Generate the preview of the attribute value(s) by doing one of the following:
If you use the default values Traceable defines, click Generate Preview in the Preview Attributes section on the right. This shows the details generated in Step 2 above, and the value(s) extracted for the attributes. You can also click View Details to see the values returned corresponding to each attribute above.
If you modified the values above, click Reload in the Preview Attributes section on the right. Post-reload, click Generate Preview to view the details generated in Step 2 above, and the value(s) extracted for the attributes. You can also click View Details to see the values returned corresponding to each attribute you configured above.
Click Submit.
Demo and Examples
Example 1 — When a JWT token is sent in the Request Header of an API
In this scenario, you must add Transformations to extract the JWT token from the header and decode it. Then, you can select the attributes you wish to identify. For example, if you consider the following JWT token and its corresponding payload for the demo, and the email claim in the payload contains the user ID. To extract it, you must add a Regex Capture Group transformation as shown in the below demo. Then, upon execution, Traceable extracts random as the user ID.
JWT Token | Payload |
|---|---|
| |
Example 2 — When a JWT token is sent in the Request Body of an API
In this scenario, you must add Transformations to extract the JWT token from the body and decode it. Then, you can select the attributes you wish to identify. For example, if you consider the following JWT token and its corresponding payload, then upon execution, Traceable extracts johndoe.com and Administrator as the user ID and role, respectively. Further, Traceable obfuscates these values on the platform.
JWT Token | Payload |
|---|---|
| |
Example 3 — When a JWT token is sent in the Request Cookie of an API
In this scenario, you must remove existing Transformations to extract the JWT token from the cookie and attribute it. Then, you can select the attributes you wish to identify. For example, if you consider the following JWT token and its corresponding payload, then upon execution, Traceable extracts john.doe as the user ID. Further, Traceable obfuscates these values on the platform.
JWT Token | Payload |
|---|---|
| |
The custom authentication method is useful when your application system uses a custom authentication scheme and you wish to define a custom logic and method for attributing users. This method is useful when basic and token-based authentication schemes do not satisfy your business requirements.
To configure custom authentication, complete the following steps:
Step 1 — Define the authentication scope
Specify the Name.
(Optional) Specify a Description for the configuration.
Select the Environment in which you wish to apply the configuration.
Select the Services on which Traceable should apply the configuration. Depending on your requirements, you can select all or specific services from the drop-down menu.
(Optional) Specify the URL Regex if you wish to provide a granular scope for user attribution.
Click Next.
Step 2 — Define the authentication attributes
From the list of available attributes, select the one(s) you wish to add. Depending on the attribute you select, complete the following steps:
Note
You can add one attribute each for User ID, User Role, and Auth Type, along with multiple Custom attributes.
User ID/User Role/User Scope/Custom:
(Optional) Select the check box if you wish to Obfuscate the value post-attribution, within the platform.
(For Custom attributes only) Specify the Key (Attribute Key) you wish to attribute as part of the authentication.
(Optional) Click + Add Condition, and select and specify the location, key, operator, and value based on which you want Traceable to check the spans for a match.
Select the Location and specify the key where Traceable can find the attribute.
(Optional) Click + Add Value Transformation to add either of the following custom transformations:
Regex Capture Group — This transformation enables you to extract specific parts of a string or value that match the pattern you define.
Base64 Decoder — This transformation enables you to convert encoded Base64 data back to its decoded or original format.
JSON Path — This transformation enables you to navigate and select a specific key within a nested JSON structure.
JWT Payload Claim — This transformation enables you to extract the attribute present in the JWT payload.
You can also reorder the transformations according to your requirements. Traceable evaluates them in order, from top to bottom.
Repeat the above steps to add one or more attributes, or complete the steps below to add the Auth Type attribute, according to your requirements.
Auth Type:
Select the authentication type from the drop-down list according to your requirements. You can also create a new one according to your requirements.
Generate the preview of the attribute value(s) by doing one of the following:
Click Generate Preview in the Preview Attributes section on the right. This shows the details and value(s) extracted for the attributes. You can also click View Details to see the values returned corresponding to the step above.
Click Reload in the Preview Attributes section on the right. Post-reload, click Generate Preview to view the details and the value(s) extracted for the attributes. You can also click View Details to see the values returned corresponding to each attribute you configured above.
Click Submit.
Demo and Example
The following demo shows how to configure custom authentication when an API key is sent in the Request Header. In such scenarios, this API key acts as the user ID. For example, if you consider the API key as x-api-key: 12345-abcde-67890-fghij, then upon execution, Traceable shows this API key as the user ID on the platform.
Note
The above API key is for reference purposes only.
User Attribution View
Once you have configured the rules, Traceable shows them on the User Attribution page.
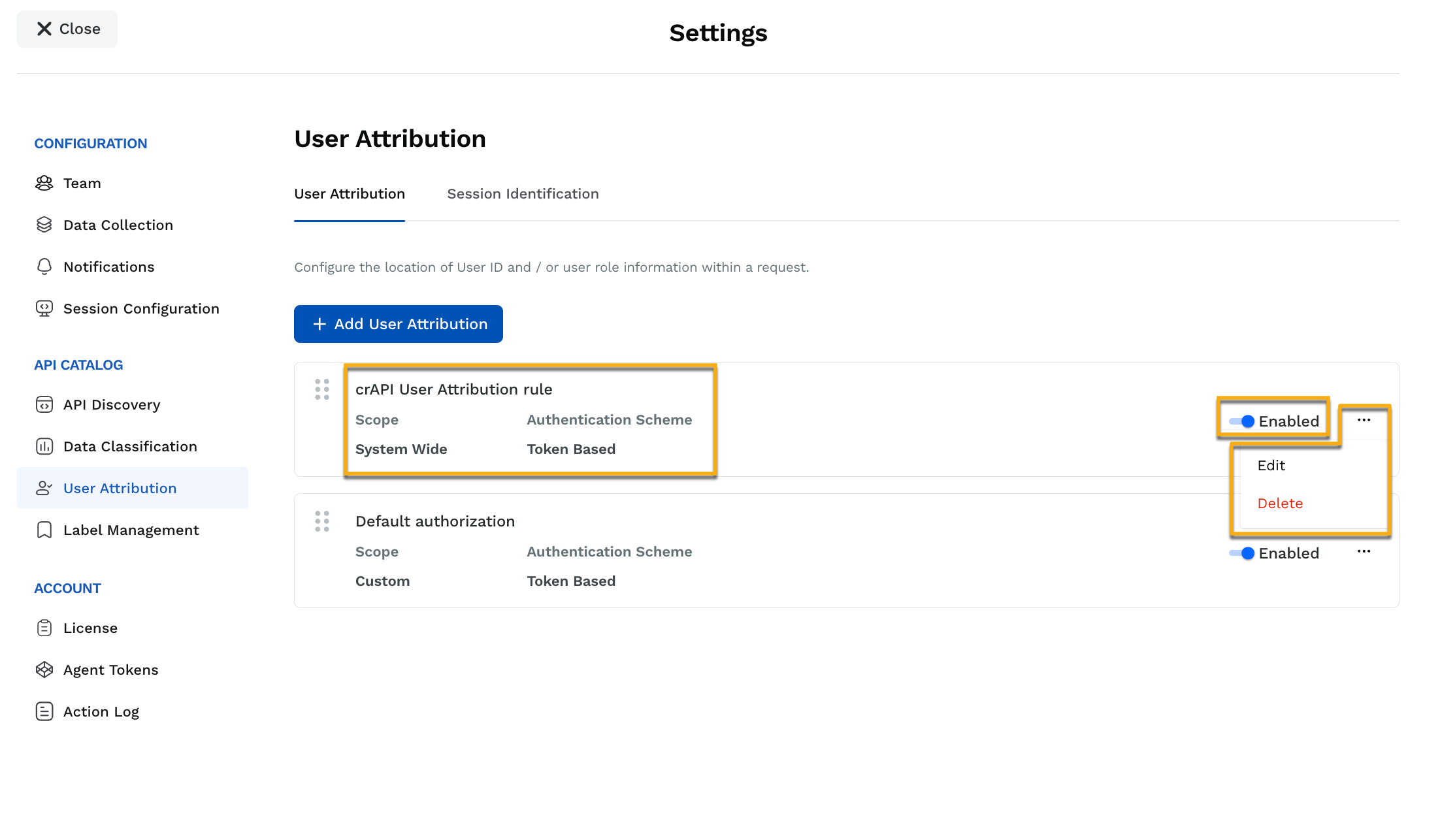
User Attribution Actions
The following details are shown for each rule:
Rule Information | Description |
|---|---|
Name | The name you specified while creating the rule. |
Scope | The scope you defined in the rule. This can have either of the following values:
|
Authentication Scheme | The authentication type (Basic, Token-based, or Custom) you selected before creating the rule. |
You can also enable or disable the rules using the toggle corresponding to it. Traceable also allows you to reorder the rules by dragging them. Based on the rule order, Traceable executes them from top to bottom. For more information on how rule ordering plays an important role in their execution, see Rule Processing.
Apart from the above, Traceable enables you to perform the following actions on a rule:
Actions | Description |
|---|---|
Edit | To update a rule, do either of the following:
|
Delete | To delete a rule, click the Ellipse (
|
Rule Processing
Traceable processes user attribution rules by breaking them down into individual components based on the attributes. This means that a rule appears as a single entity on the User Attribution page; however, Traceable deconstructs it into separate rules based on each attribute type (User ID, User Role, User Scope, Auth Type, and Custom) before evaluating them internally. Traceable evaluates these rules based on their sequence in the user interface, meaning the topmost rule is evaluated first, followed by the ones below.
Traceable follows an all-match and first-match approach for processing rules according to the attribute type:
Attribute Type | Processing Details |
|---|---|
User ID/User Role/User Scope/Custom | All rules for the relevant attribute are collectively sent to the backend and evaluated on a first-match basis, depending on their sequence. Traceable evaluates each rule in the sequence, as mentioned above, and stops at the first matching rule, disregarding any subsequent rules for that attribute. This makes rule ordering important, as the highest one in the sequence takes effect. |
Auth Type | All rules for this attribute are sent to the backend and executed on an all-match basis depending on their sequence. Instead of stopping at the first match, Traceable collects all relevant matches into an array and shows them on the platform. |
This sequential rule-based processing ensures accurate and flexible user attribution, especially for complex configurations. You can customize the priority and application of each rule by arranging them on the User Attribution page according to your business requirements.