Updates (January 2026 to March 2026)
January 2026 — Updated the topic to add information about AI-related and other latest features in Traceable.
If you build or run modern applications, APIs sit at the center of everything you deliver. Over time, they spread across teams, services, cloud environments, and third-party integrations. As this ecosystem grows, visibility often falls behind. You may not know how many APIs you have, where they run, who is calling them, what data they expose, or which ones introduce risk. Traceable helps you regain that visibility and control. By continuously observing API traffic across your environment, Traceable automatically discovers and analyzes every API as it is actually used in production. You no longer need to depend on outdated documentation or manual tracking. As traffic flows, Traceable identifies internal and external APIs, undocumented shadow APIs, and APIs that should have been retired but remain active.
Runtime Visibility That Goes Beyond Inventory
Traceable automatically discovers all APIs from live traffic and maintains a continuously updated inventory that captures their endpoints, specifications, ownership, and runtime behavior in one unified view. Discovery in Traceable goes beyond inventory. For each API, Traceable shows how it behaves in the real world. You can view which methods and endpoints are in use, how frequently they are called, the authentication applied, and how each API connects to services, domains, and environments.
Traceable also gives you visibility into the data flowing through your APIs. By analyzing live requests and responses, it identifies sensitive data such as personal, financial, or regulated information and maps it to specific parameters. This helps you understand exposure, reduce compliance risk, and focus protection where it matters most. From a security perspective, Traceable continuously evaluates APIs for risk and abuse. It highlights unauthenticated or overly exposed endpoints, detects abnormal behavior and attack attempts, and maps observed activity to common API threat patterns. Each finding includes clear, actionable context, enabling you to prioritize genuine risks rather than responding to noise. For more information, see Discovery.
Unified API Visibility
Traceable connects security, development, and operations through a shared and accurate view of APIs, enabling seamless collaboration across teams. It automatically generates API documentation, including OpenAPI and GraphQL specifications, directly from live traffic. Existing specifications can be validated against production behavior to identify gaps and drift. This alignment clarifies ownership, enhances collaboration, and keeps documentation grounded in reality. Security is most effective when it fits naturally into existing workflows. Traceable integrates with CI/CD pipelines, cloud platforms, and collaboration tools, enabling governance, automated testing, and policy enforcement without slowing delivery. Continuous monitoring ensures APIs remain protected as they evolve, while scheduled or on-demand testing helps detect issues early across all environments. For more information, see API Risk.
AI-Assisted Clarity and Decision-Making
To further simplify investigation and response, Traceable provides AI-driven insights across discovery and protection workflows. AI explains why issues occur, assesses severity, and recommends remediation in clear, developer-friendly language. An AI-powered chatbot lets you ask natural-language questions about APIs, sensitive data exposure, or active threats, and receive concise, actionable answers. This enables faster understanding, better prioritization, and more confident decision-making without replacing human judgement. For more information, see AI Features.
Discovery guides you through Traceable’s analysis of your API landscape, highlights potential exposures, and helps you maintain confidence in your security posture.
Discovery
As your applications grow, APIs quietly multiply across teams, services, and environments. What starts as a manageable set of endpoints quickly becomes challenging to track, making it hard to answer basic but essential questions. Which APIs are active today? Who is calling them? What data do they expose? And which of them could introduce risk? Traceable addresses this challenge through API Discovery. API Discovery provides a clear and continuously updated view of every API running across your entire environment. As applications evolve and new services are introduced, Traceable automatically discovers APIs, observes how they are utilized, and identifies where sensitive data is processed. This helps you understand what is exposed, what is changing, and where potential security risks may exist, without relying on manual documentation or incomplete inventories.
API Endpoints
APIs power every modern application, but they also expand quickly and often without complete visibility. Before you can secure your APIs, you need to understand what exists, how each API is used, and where the real risk lies. Traceable automatically discovers every API endpoint across your environment and continuously observes live traffic to keep this understanding accurate and up to date. Traceable identifies all API types, including REST, SOAP, gRPC, GraphQL, and WebSocket, across both internal and external services. Each endpoint is analyzed for the data it handles, the authentication method used, and whether its behavior aligns with expectations. This eliminates manual tracking, ensuring you always have a reliable view of your API surface, even as it evolves with new releases and services.
Security becomes clearer when APIs are not treated equally. Traceable evaluates every endpoint based on real usage patterns, authentication strength, exposure to sensitive data, and abnormal behavior. APIs that pose higher risks, such as weak authentication, unexpected traffic spikes, or access to sensitive data, are clearly identified. In contrast, stable and well-protected APIs are categorized as low risk. This allows you to focus their time and effort where it matters most, rather than wasting time on distractions.
As your API ecosystem grows, organization and control become just as important as visibility. Traceable lets you filter, group, and label APIs by environment, ownership, authentication method, and security posture. Roles and scopes help enforce proper authorization, ensuring the right users and services have the right level of access. These controls enable you to manage APIs confidently at scale. By continuously inspecting headers, tokens, and credentials, Traceable detects authentication gaps and emerging threats as they happen. Risk levels update automatically as traffic changes, keeping security aligned with real-world behavior. By combining discovery, monitoring, and risk analysis, Traceable transforms API visibility into actionable security, enabling teams to protect applications, data, and users without slowing down development. For more information, see API Endpoints.
The Inventory page, shown below, highlights the APIs at risk, Unauthenticated APIs, and all APIs discovered by Traceable. It also displays the number of internal and external APIs. You can narrow the discovered APIs using various filters, such as sensitive data APIs or only external APIs.
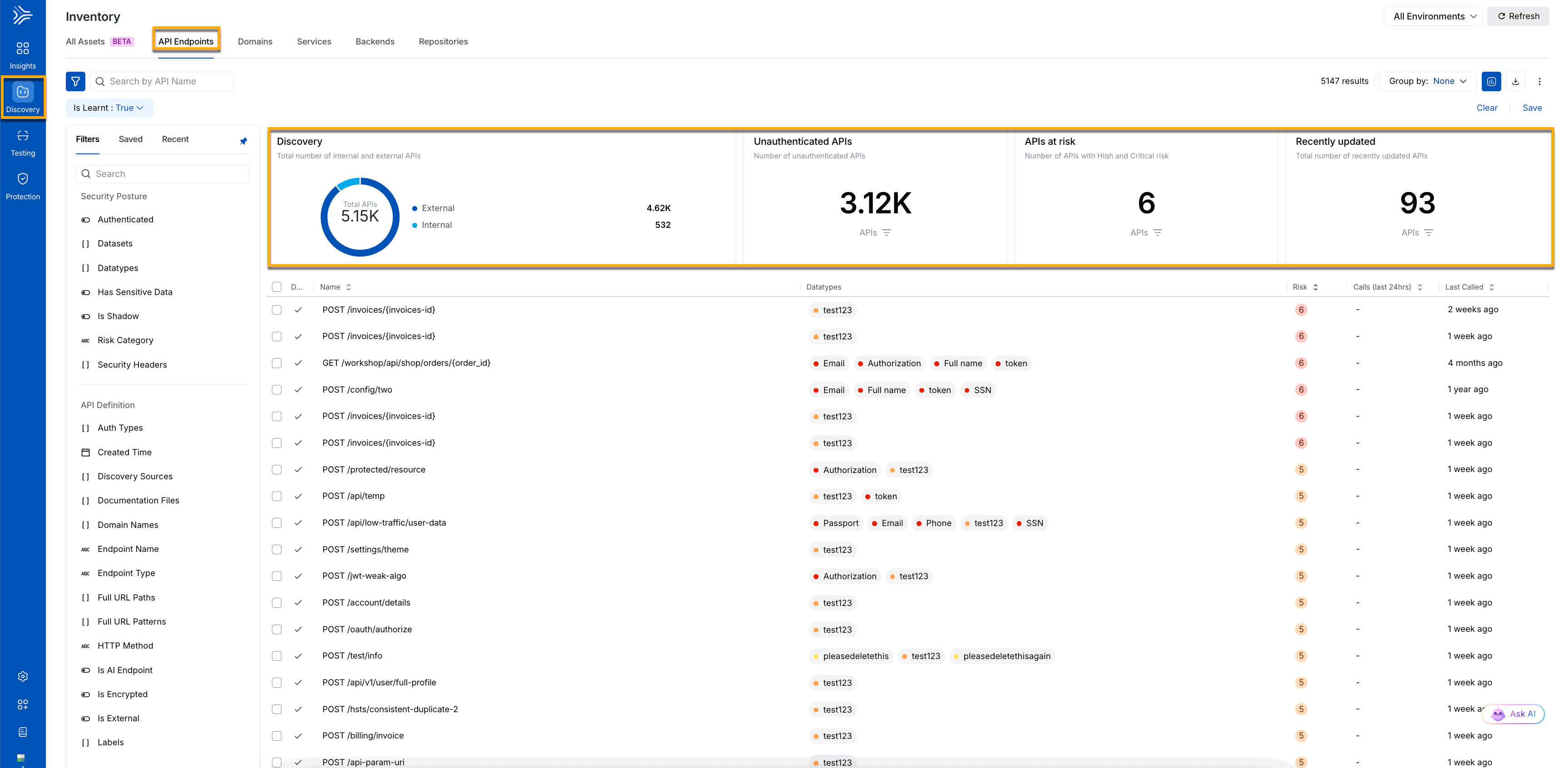
API Discovery
What is API Discovery?
By continuously observing real production traffic, Traceable automatically discovers APIs as they are actually used, not just as they were designed or documented. This gives you an accurate, continuously updated view of all APIs in your environment, including internal services, external and third-party integrations, and Shadow, Zombie, or Orphan APIs that often go unnoticed. Discovery does more than list APIs. For every endpoint, Traceable helps you understand real behavior in production. You can see which methods and paths are used, how frequently they are called, what authentication is applied, and how each API connects to services, domains, and environments. This context allows you to move from assumptions to evidence when reasoning about your APIs. Understanding behavior is only part of the picture. Traceable also analyzes runtime requests and responses to identify sensitive data flowing through APIs. Personal, financial, and regulated data is mapped to specific parameters, helping you understand exposure, assess compliance impact, and focus security efforts where they matter most.
API Discovery also forms the foundation for security visibility. Traceable continuously evaluates APIs for risk, highlighting unauthenticated or overly exposed endpoints and detecting abnormal or malicious activity. Mapping observed behavior to common API threat patterns helps teams identify meaningful risks without being overwhelmed by noise. To support development, governance, and collaboration, Traceable generates API specifications, such as OpenAPI and GraphQL, directly from live traffic. You can also upload existing specifications to validate behavior and run automated inspections that surface security and design issues. Each discovered API is linked to its broader system context, making ownership and dependencies easier to understand.
API Risk
Traceable continuously observes real API traffic to discover every API in your environment, including internal, external, third-party, shadow, and zombie APIs. You can see how each endpoint behaves in production, including how often it is applied, which authentication method it uses, and which services or domains it connects to, providing a real-time map of your API ecosystem. To make sense of this activity, Traceable links API calls to users and sessions, extracting identities from headers, tokens, or cookies, and stitching requests into continuous sessions. You can categorize APIs, services, and backends with custom or automated labels, enabling you to filter, prioritize, and organize your API landscape for enhanced security, compliance, and operational oversight. Together, these capabilities provide you with complete visibility and context, transforming raw API traffic into actionable insights.
Detecting issues is only the first step, but acting on them is critical. Traceable tracks each issue’s severity, frequency, and impact, helping you focus on high-risk problems first. By prioritizing essential topics such as authentication flaws and exposed sensitive data, you can prevent attacks, reduce business risk, and maintain compliance with internal and regulatory standards. Continuous monitoring ensures that previously resolved issues are verified and monitored for you if they recur. This proactive approach enables you to seamlessly integrate API protection into your everyday workflows, thereby avoiding last-minute surprises and costly remediation efforts.
The following screenshot gives you a complete view of all discovered application assets, their activity, and associated risk. It provides a centralized view of all assets discovered across your application. It includes APIs, MCP tools and servers, services, and other components, along with their total count, recent updates, and sensitive data exposure. The table below allows you to review individual assets, including their risk score, data types, usage, and last activity. For more information, see Discovery.
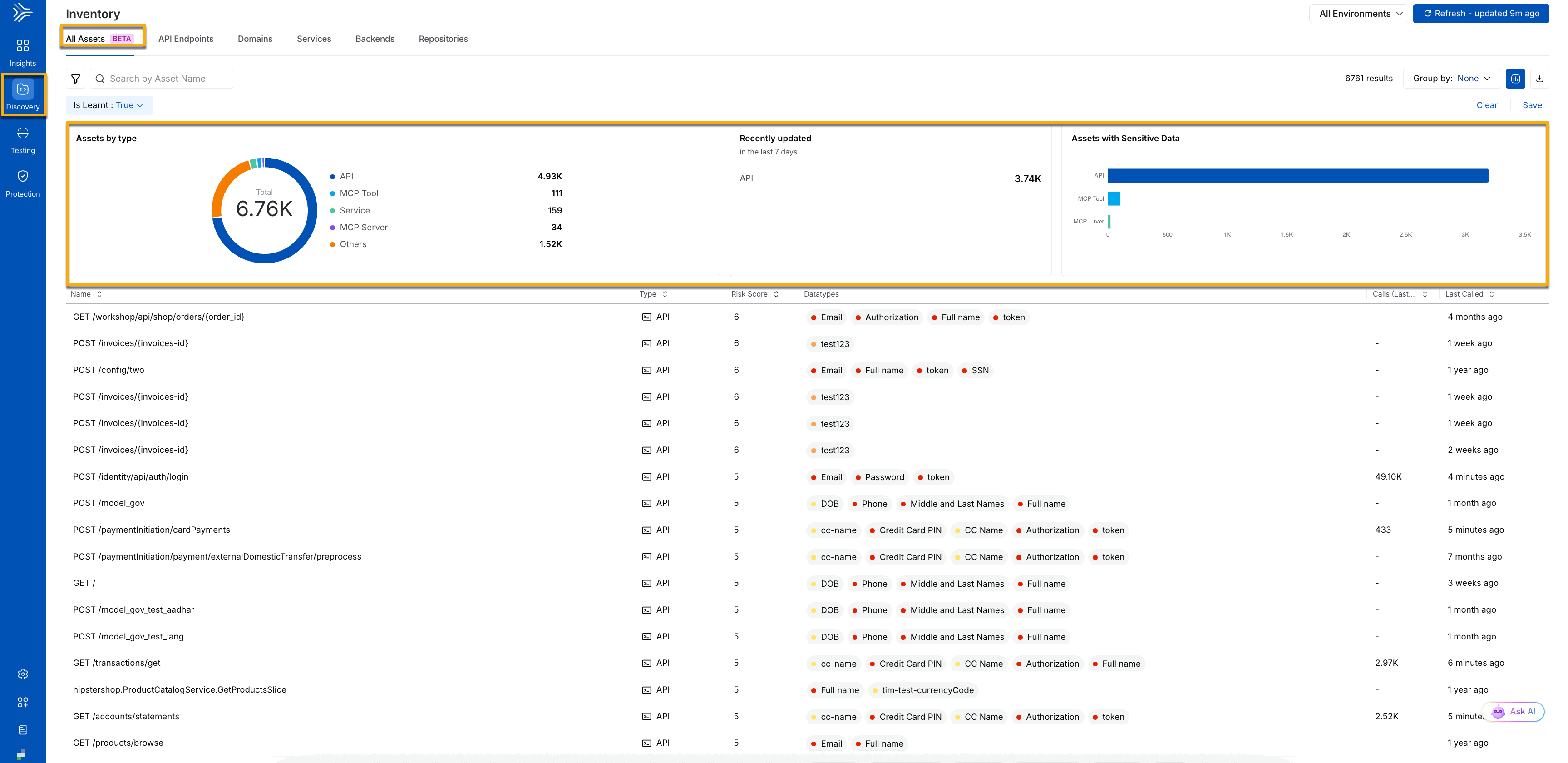
All Assets
With threats identified, the following sections highlight how Traceable supports response, conformance, and ongoing protection.
Issues Workflow
Every issue in Traceable follows a structured lifecycle that ensures continuous visibility and consistent handling. Traceable discovers APIs and endpoints through live traffic, integrations, and test scans, and evaluates them against defined security policies and plugins. Each issue is enriched with context, including severity, category, and affected endpoints, helping teams understand the impact and scope. Once identified, you can respond based on business and security priorities. Traceable supports multiple remediation paths, allowing you to fix issues directly, mark them for review, accept known risks, or dismiss findings that do not apply. Issues are categorized from critical to informational, enabling teams to focus first on high-impact risks while planning long-term improvements.
All findings are consolidated on the Issues page, which provides trend analysis, grouping, and filtering to support prioritization and tracking. After remediation, Traceable continues to monitor affected APIs and endpoints. If an issue reoccurs, it is automatically reopened, ensuring that issue status always reflects production reality and preventing resolved risks from silently returning.
Conformance Analysis
Conformance analysis focuses on whether APIs behave as intended. Unlike issue detection, which identifies security risks, conformance analysis evaluates alignment between API specifications, such as OpenAPI definitions, and real-world traffic. Traceable continuously compares specifications with live production behavior to uncover API drift. It identifies shadow endpoints that appear in traffic but are not documented, orphan endpoints that are no longer in use, and mismatches in parameters, headers, or payloads for documented endpoints. Teams can run conformance analysis on demand or schedule it to run regularly, with each finding providing detailed context for investigation. By surfacing gaps between design and behavior, conformance analysis helps teams maintain accurate documentation, control change, and reduce unintended exposure as APIs evolve.
Remediation and Continuous Protection
Conformance findings and issues can be reviewed in detail and linked to existing workflows or ticketing systems, allowing you to operationalize remediation as part of normal development and governance processes. This ensures that fixes, documentation updates, and design changes remain aligned over time. Traceable continuously monitors APIs even after issues are resolved or conformance gaps are addressed. This ongoing protection ensures that new risks, regressions, or deviations are detected as they emerge. By integrating issue workflows and conformance analysis into daily operations, you move from reactive security response to proactive, continuous API protection. For more information, see Issues Overview.
Dashboards and Insights
Traceable dashboards provide a unified view of activity across your APIs, combining traffic patterns, performance signals, security risks, and AI-related threats in one place. The Home, AI Security, and Custom Dashboards are designed to be flexible, allowing you to tailor views to what matters most to you. Dashboards adapt to your workflow, making it easy to add, edit, duplicate, resize, rearrange, or remove widgets based on your priorities, whether you are monitoring risky APIs, tracking threat activity, or watching for sensitive data exposure. Custom dashboards support team- or use case–specific views, while the Home and AI Security dashboards offer built-in insights to help you get started quickly. As needs change, dashboards can be updated, reset, or removed, keeping views clear and relevant. Together, dashboards turn security data into actionable insights without adding complexity.
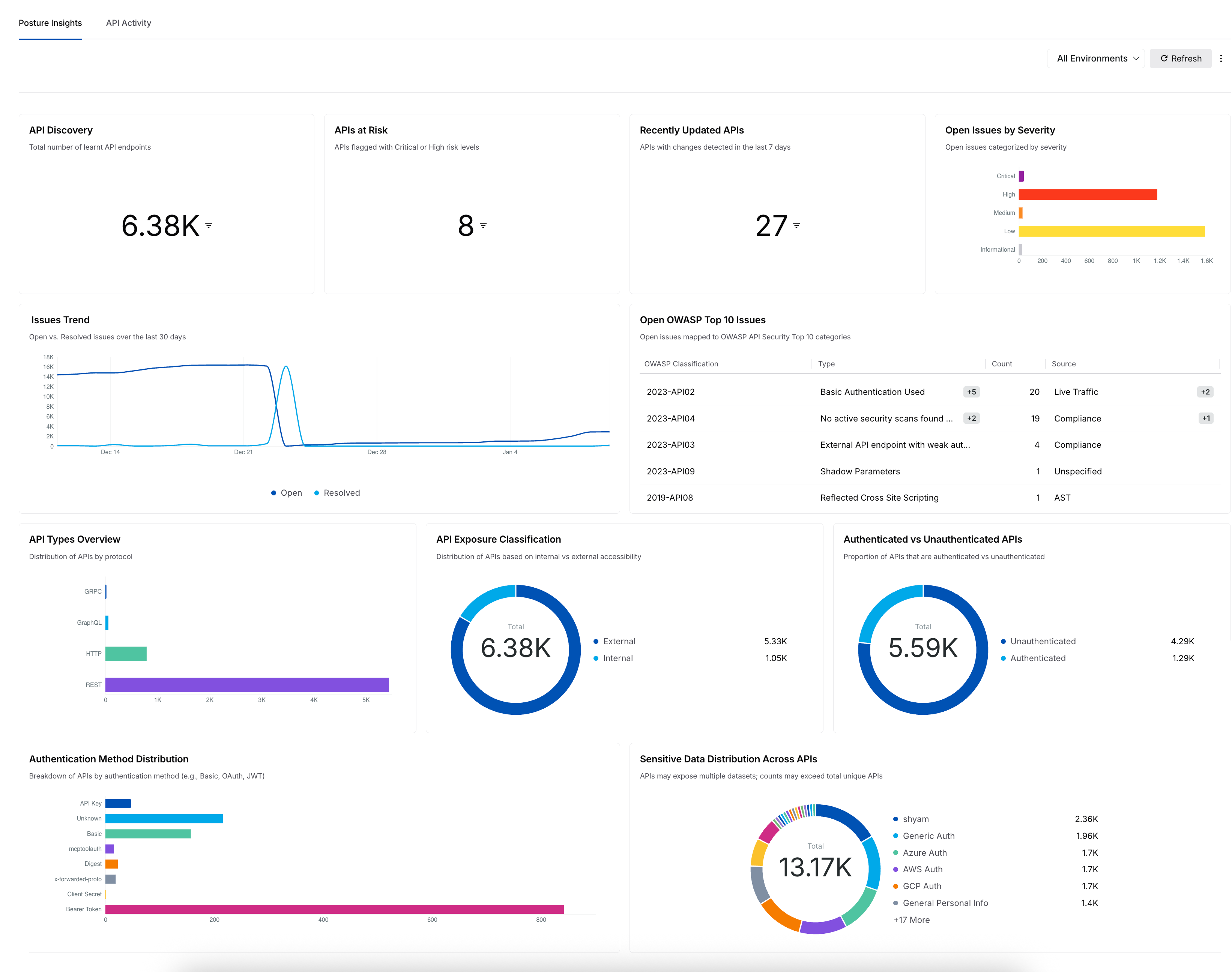
Dashboard Insights
App Topology
The Application Flow provides a clear view of how traffic flows through your application by mapping requests as they traverse services and APIs. The topology map helps you understand service dependencies and communication paths, making it easier to see how different components interact and where issues or risks could spread across the system. This visual representation provides valuable context for understanding the application's structure and operational behavior.
You can interact with the topology map to explore these relationships in detail. Selecting any service or component on the map opens a contextual details view that shows associated APIs, observed endpoints, request and response data types, and an overall risk indication, including any sensitive data involved. This makes it easier to investigate individual elements, assess their exposure, and analyze their role in the broader application flow without losing sight of the complete topology.
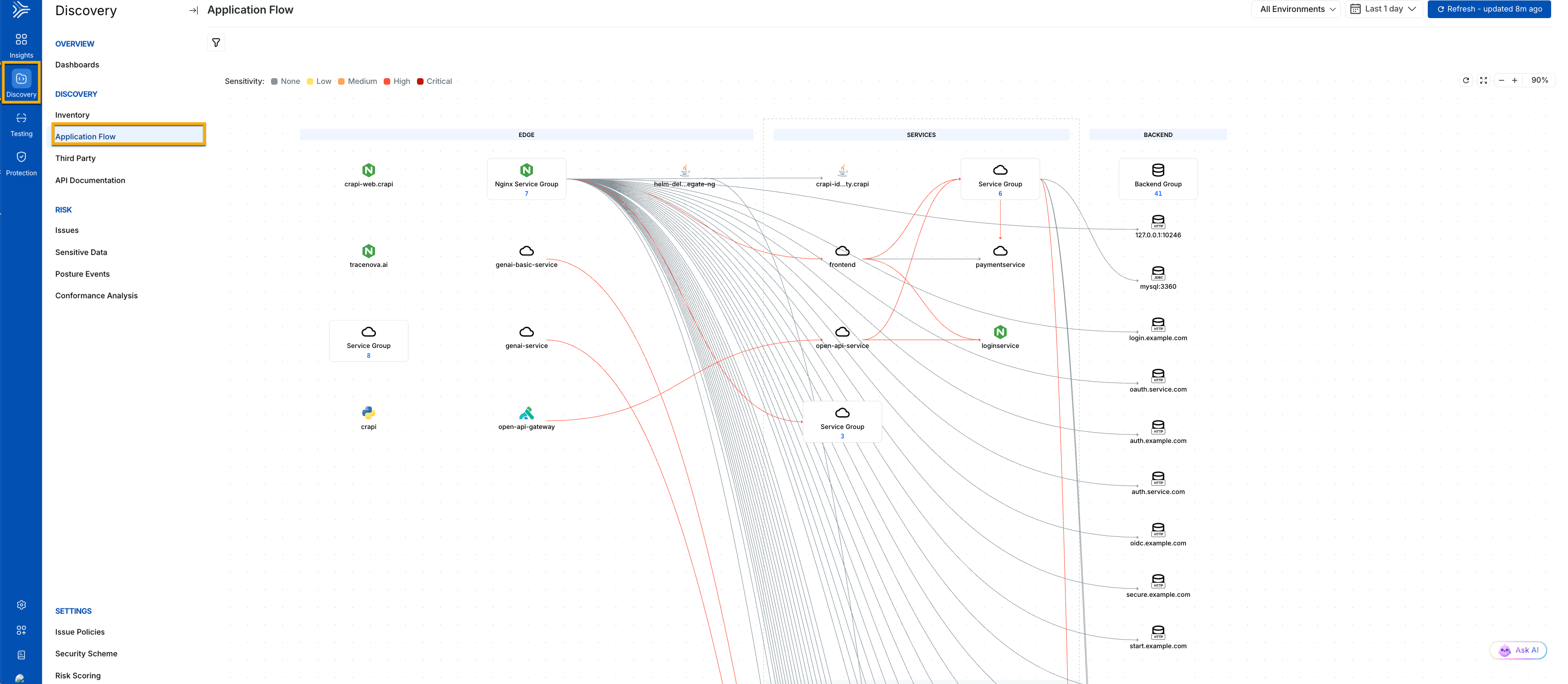
Application Flow
After you understand your API landscape, the next step is to protect it. The Protect your APIs section explains how Traceable identifies and blocks attacks, allowing you to keep your applications safe with confidence. The protection policies specify the security rules you can use to safeguard your application ecosystem against threats such as unauthorized access and malicious traffic. It allows you to manage your application’s security by applying both predefined and custom rules according to your configuration. For more information, see Understanding Policies.
Protect your APIs
APIs, applications, and AI services are exposed to various threats, including abuse, bots, and API-specific attacks. Traceable Protection helps secure these services by continuously analyzing traffic, behavior, and usage patterns. It uses built-in security policies to detect suspicious and malicious activity, giving you immediate visibility into potential threats without requiring any upfront configuration. These built-in policies cover common protection needs such as rate limiting, bot protection, IP-based rules, and attack detection. They allow you to monitor traffic, identify high-risk behavior, and understand how your APIs are being used and misused. You can begin in monitoring mode to observe threats and traffic patterns, and move to enforcement as you gain confidence, without affecting normal application behavior.
When built-in protections are not enough, you can create Custom Policies to tailor protection to your specific requirements. Custom Policies let you define rules based on traffic sources, request patterns, sensitive data, or request frequency, with actions such as allow, block, or monitor. This gives you precise control to reduce false positives and protect specific APIs or use cases while maintaining smooth application operations. There are several ways to protect your APIs, and Traceable’s Custom Policies give you direct control over how that protection works. They let you define specific security rules to block malicious behavior, manage traffic patterns, and minimize false positives, while still allowing legitimate requests to pass through. This approach helps you secure APIs without disrupting normal application behavior.
The table below highlights the pillars of Protection and explains how WAF, API protection, Bot protection, and Custom policies work together to secure your environment. For more information, see Protection.
Policy | Description | Purpose |
|---|---|---|
Enforces security rules consistently across applications and environments with support for environment-specific overrides. | Maintains a unified and adaptable security posture across deployments. | |
Applies predefined threat categories and rules to APIs with visibility into severity, classification, and overrides. | Simplifies API threat management while allowing fine-grained control. | |
Detects abnormal behavior and misuse across AI models, workflows, and endpoints. | Protects AI systems from data exposure, abuse, and compliance risks. | |
Detects and mitigates malicious bot activity across APIs and web applications, helping prevent fraud, account abuse, and business disruption. | Reduces operational risk caused by malicious or unwanted bots. | |
Defines rules based on traffic sources, request patterns, sensitive data access, or request frequency. | Enables precise control over how APIs respond to trusted and untrusted traffic. | |
Defines conditions where specific requests bypass monitoring or enforcement based on environment, source, threat type, or API attributes. | Reduces false positives, preserves trusted traffic, and keeps security controls focused on genuine threats. |
Threat Activities, Threat Actors, and Threat Scoring
Threat Actors — The Threat Actors page helps you quickly identify and investigate suspicious users or IP addresses targeting your APIs. Traceable continuously monitors behavior, flags anomalies, and provides visibility into who the actor is, what actions they are performing, and which endpoints they are affecting. You can drill into detailed evidence, review activity patterns, and update an actor’s status to monitor, allow, or block them as needed. This gives you a transparent and efficient way to understand threats and take appropriate action to protect your APIs. For more information, see Threat Actors.
Threat Activity — To stay ahead of attacks, you need visibility into how threats are evolving. The Threat Activity page provides a real-time view of all security events impacting your APIs, endpoints, and services. It helps you track threat sources, severity levels, and affected endpoints, enabling you to assess risk and prioritize responses quickly. You can explore detailed logs and timelines, investigate anomalies, update threat statuses, and manage tickets to ensure issues are tracked through resolution. This visibility enables faster response, effective mitigation, and ongoing protection against evolving threats. For more information, see Threat Activity.
Threat Scoring — Traceable assigns dynamic risk scores to users based on detected anomalies, security events, and attack behavior. It correlates deviations from regular traffic with known attack patterns to distinguish benign anomalies from real threats. Scores are configurable for anomaly frequency and security event severity, and can be weighted based on the risk level of affected APIs. As activity escalates, users progress from monitored users to threat actors, with cumulative scores reflecting both behavior patterns and attack impact. Threat actors are categorized into low, medium, high, and critical risk using adjustable thresholds. Based on these scores, teams can enable automated responses such as auto-blocking while using exclusions and allowlists to prevent trusted users or IPs from being impacted. This approach helps you prioritize high-risk activity and respond consistently at scale. For more information, see Threat Scoring.
The dashboard screenshot below highlights various protection policies and their corresponding data insights, including the Top OWASP, Top CWE, Top Threat Types by events and threat activities, and other relevant metrics.
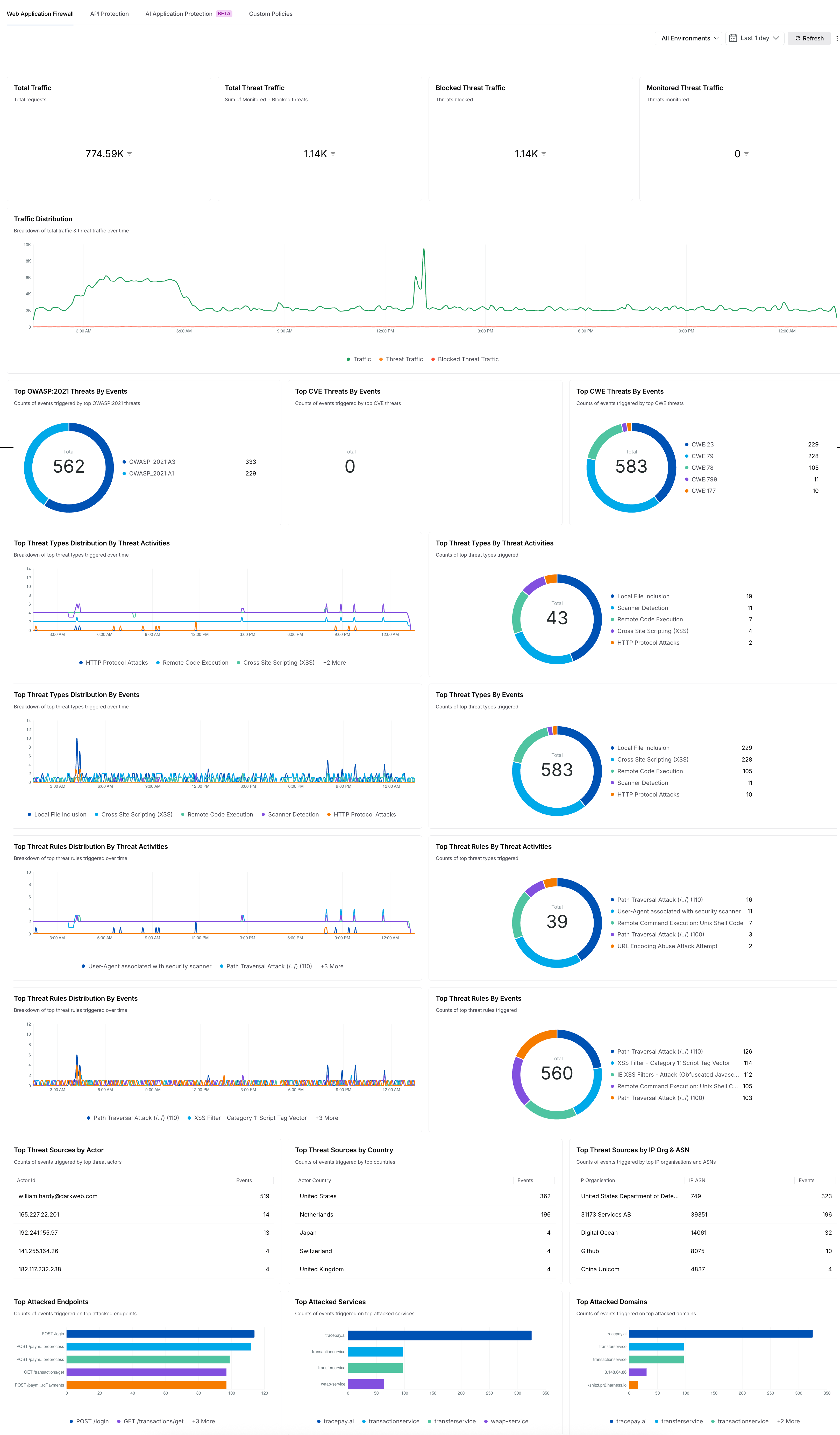
Protection Dashboard
Protection also plays a crucial role in ensuring APIs remain available and reliable. Rate limiting helps prevent abuse and sudden traffic spikes that could overwhelm services, while IP-based controls allow teams to block known bad actors early. These safeguards are especially valuable for publicly exposed APIs or high-traffic endpoints that power essential business workflows. Beyond individual rules, Traceable continuously evaluates activity across APIs to identify broader threat patterns. High-risk behavior surfaces quickly, helping you focus your attention where it matters most. With built-in visibility into active threats and their impact, you can respond decisively, while developers continue to ship without friction.
Before attackers can exploit weaknesses, you need visibility into the security of your APIs. Application Security Testing helps you validate your APIs by actively testing them for vulnerabilities, misconfigurations, and risky behavior as your application evolves. This section walks through how Traceable enables you to test APIs early and continuously, understand the security impact of changes, and address issues before they reach production. By integrating testing into your workflow, you can reduce risk, shorten remediation cycles, and build stronger API security into every stage of development.
API Security Testing
Understanding AST components and workflow
Traceable’s API Security Testing (AST) is an automated solution for identifying security risks in APIs. It defines what to test, how tests are run, and which configurations are used. This allows teams to detect vulnerabilities early and secure APIs throughout their lifecycle.
The screenshot below displays the scan details and the create scan option.
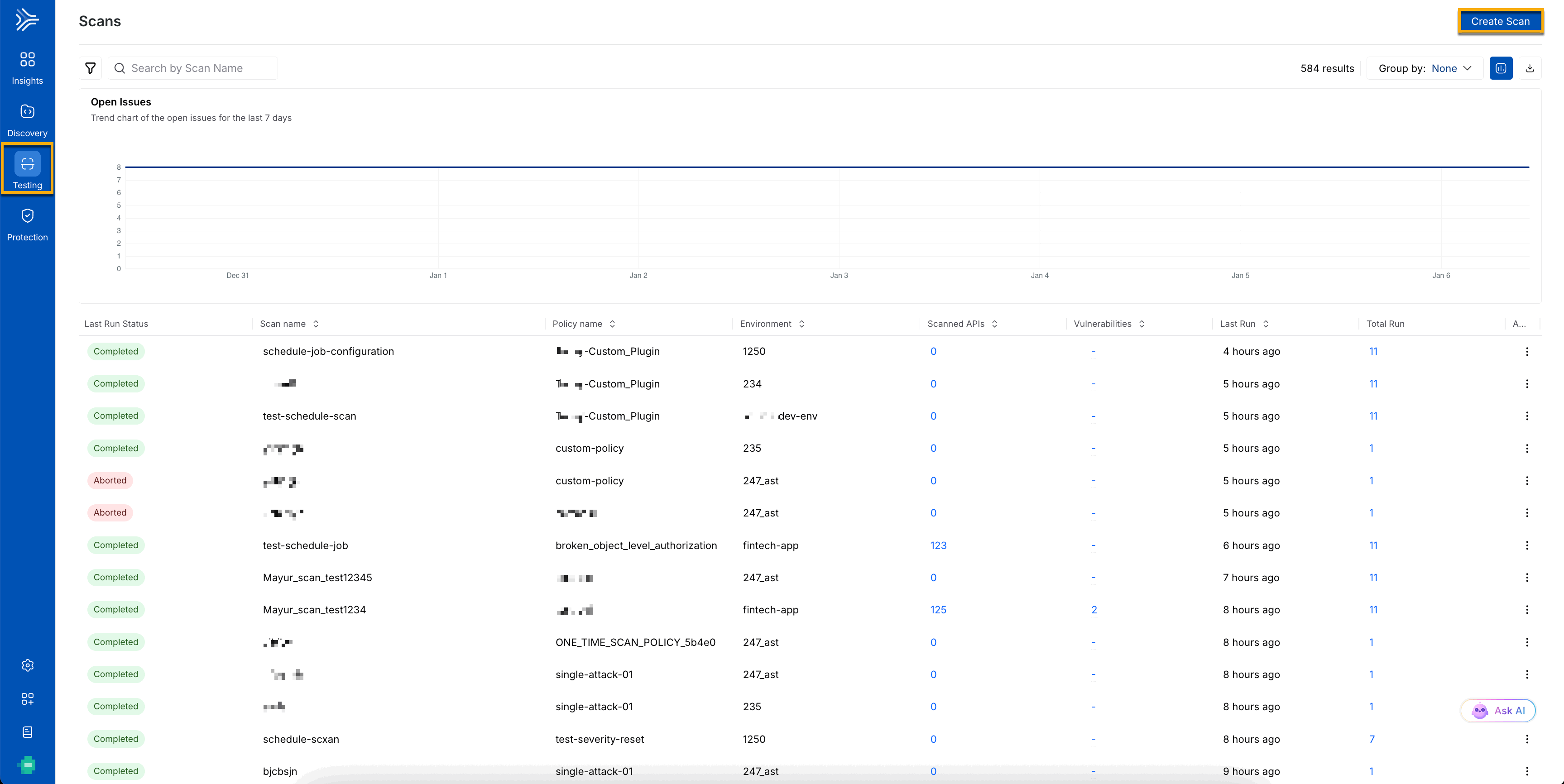
Create a Scan in AST
The three main W’s of AST
Understanding API Security Testing begins with understanding what it is, why it matters, and when to utilize it. The table below helps you know the three main W’s and stay ahead of threats while keeping your APIs safe and compliant.
What | Why | When to Use |
|---|---|---|
AST (API Security Testing) is a structured framework for testing APIs for security risks. Each scan defines which endpoints to check, the type of traffic to simulate, and the security rules to apply. | AST empowers your team to detect issues early, protect APIs before threats exploit them, and maintain compliance effortlessly. Scheduling scans in advance saves time, reduces manual effort, and gives continuous visibility into risk. | Run scans at key moments, such as after deploying new APIs, updating existing ones, or monitoring sensitive endpoints. You can trigger them on demand or schedule daily, weekly, or monthly, keeping security proactive. |
The table below provides a structured view of key AST concepts, their purpose, and the value they deliver in real-world API security workflows:
Concept | Purpose | Results |
|---|---|---|
Scans | Define how API security tests are executed by combining APIs, environments, traffic sources, and security policies. | Consistent, repeatable security testing that adapts automatically as APIs evolve. |
Traffic Types | Enable testing across different API lifecycle stages using live, replayed, or specification-based traffic. | Accurate vulnerability detection with the flexibility to test in development, staging, or production. |
Creating a Scan | Allow teams to configure what to test, how to test it, and which risks to evaluate. | Targeted scans that focus on relevant APIs and meaningful security risks. |
Scan Execution | Run security tests on demand or on a schedule without manual intervention. | Continuous visibility into API security posture across environments. |
How to use AST?
You can use AST to create scans that define which APIs to test, how to test them, and which security policies to apply. You can run scans on demand or schedule them to run automatically, ensuring continuous coverage and consistent security across all your environments. You begin by providing the scan details, such as name, environment, and schedule (one-time, daily, weekly, or monthly). You can choose a traffic type from the following:
XAST Live — It tests using live traffic in real time.
XAST Replay — It uses historical traffic for replay-based testing.
DAST — It simulates black-box attacks using API specifications such as OpenAPI, Postman, or GraphQL. For more information, see Creating a Scan.
After you select the traffic type, you choose or create a policy or attack set to define which security tests to run. You can also configure advanced options such as runners, timeouts, request delays, and integrate tools like Snyk. Each scan generates detailed logs, API coverage metrics, and a list of detected issues, providing clear visibility and actionable insights to resolve issues quickly and efficiently. You can pause, resume, or run scans whenever needed. For more information, see Getting Started with AST.
Role-Based Access Control (RBAC)
Traceable uses Role-Based Access Control (RBAC) to efficiently and securely manage platform access. RBAC ensures that you and your team members can view and act only on the modules, APIs, or environments relevant to their responsibilities. By defining roles and permissions, you can invite new members to your organization, separate duties, and protect sensitive actions such as managing policies, API tokens, or security issues.
You can leverage predefined roles or create custom roles tailored to your team’s needs, controlling access at the module level, administrative settings, or specific scopes such as environments, endpoints, or services. RBAC helps your team stay productive while maintaining a secure platform.
The following section outlines the predefined roles and explains what each role is expected to do to match your team structure and operational requirements:
Role | Description |
|---|---|
Account Owner | You can manage the entire Traceable account, including users, roles, licensing, and platform settings. You have full super-user access. |
Security Admin | You can configure and manage security policies, investigate attack information, and monitor security events. |
Security Analyst | You can monitor events and threats, manage alerts, and track issues to respond effectively to potential risks. |
Global Reader | You have read-only access to view API risks, threat activities, and security posture, helping you prioritize without making changes. |
Developer | You can focus on the APIs and services you are responsible for, as well as on monitoring risks, threats, and application-specific issues. |
AI Features
Understanding your API landscape can be complex. Traceable uses AI to simplify this by helping you quickly explore, understand, and act on what is happening across your APIs. This section demonstrates how AI streamlines your investigations, provides prompt answers, and guides you with clarity. Traceable now provides an AI-powered chatbot across the Discovery and Protection modules, enabling you to query platform data using natural language. Instead of navigating multiple dashboards or filters, you can quickly explore APIs, services, domains, sensitive data, threat actors, and security events. The AI chatbot maintains read-only queries and conversational context across modules throughout a single session for follow-up questions, delivering concise, actionable results. You can use the AI-powered chatbot to identify risks and gain actionable insights across your APIs quickly. For more information, see Ask AI.
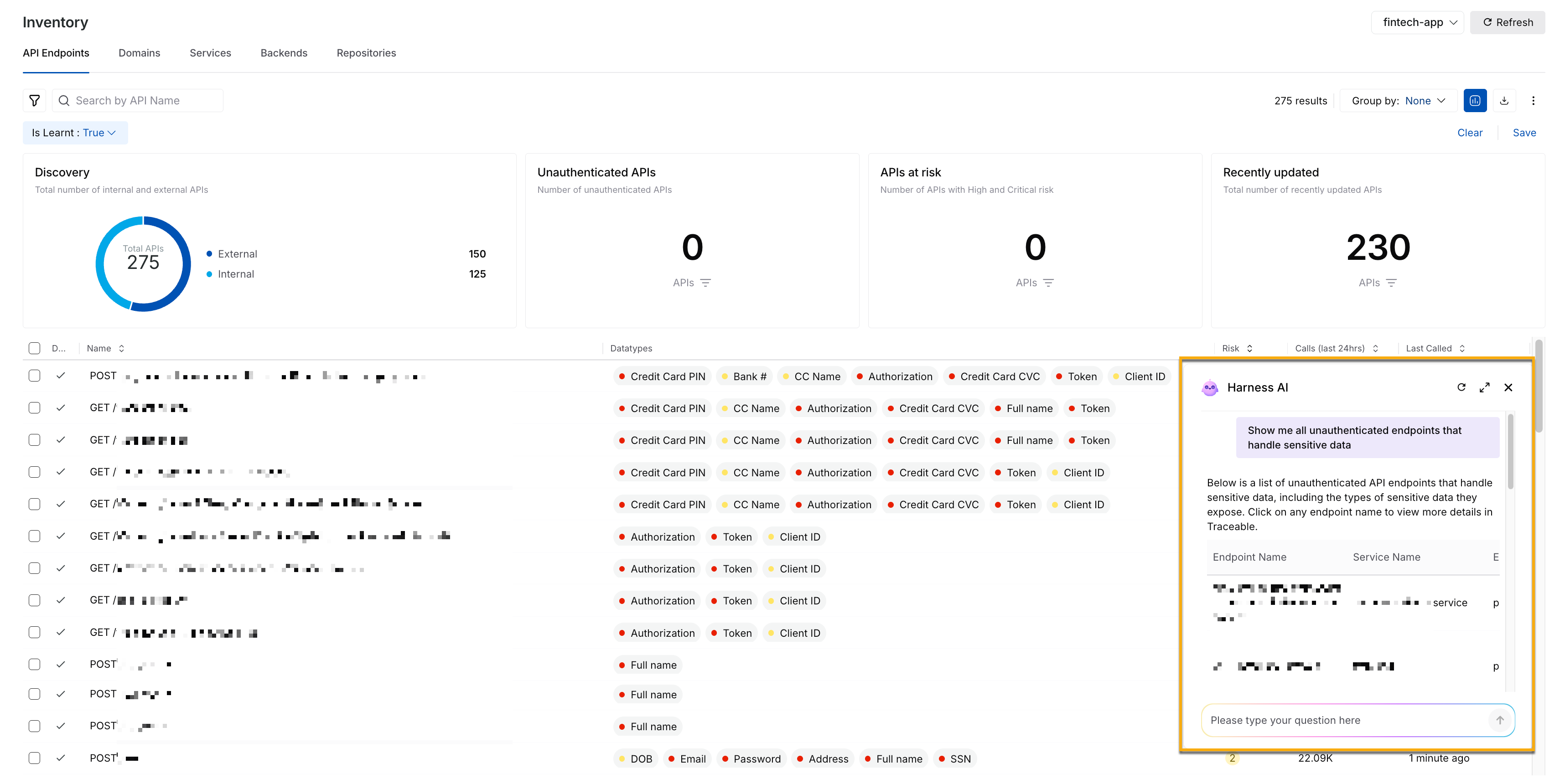
AI Chatbot
AI-Powered Security Insights
Traceable leverages Generative AI and enterprise LLMs to provide context-aware, actionable insights across your APIs. AI automatically analyzes issues and threat activity, explains how issues were detected, highlights affected endpoints, and suggests remediation in simple, developer-friendly language. With AI, you can prioritize high-risk issues, investigate anomalies, and generate authentication code or scripts directly from prompts, streamlining both security and operational workflows. Insights appear wherever relevant, such as on issue details or threat activity pages, guiding you to act faster and more confidently.
You can enable the AI feature by navigating to Settings → AI Features and allowing the toggle to and immediately start leveraging intelligent, actionable insights across Traceable.
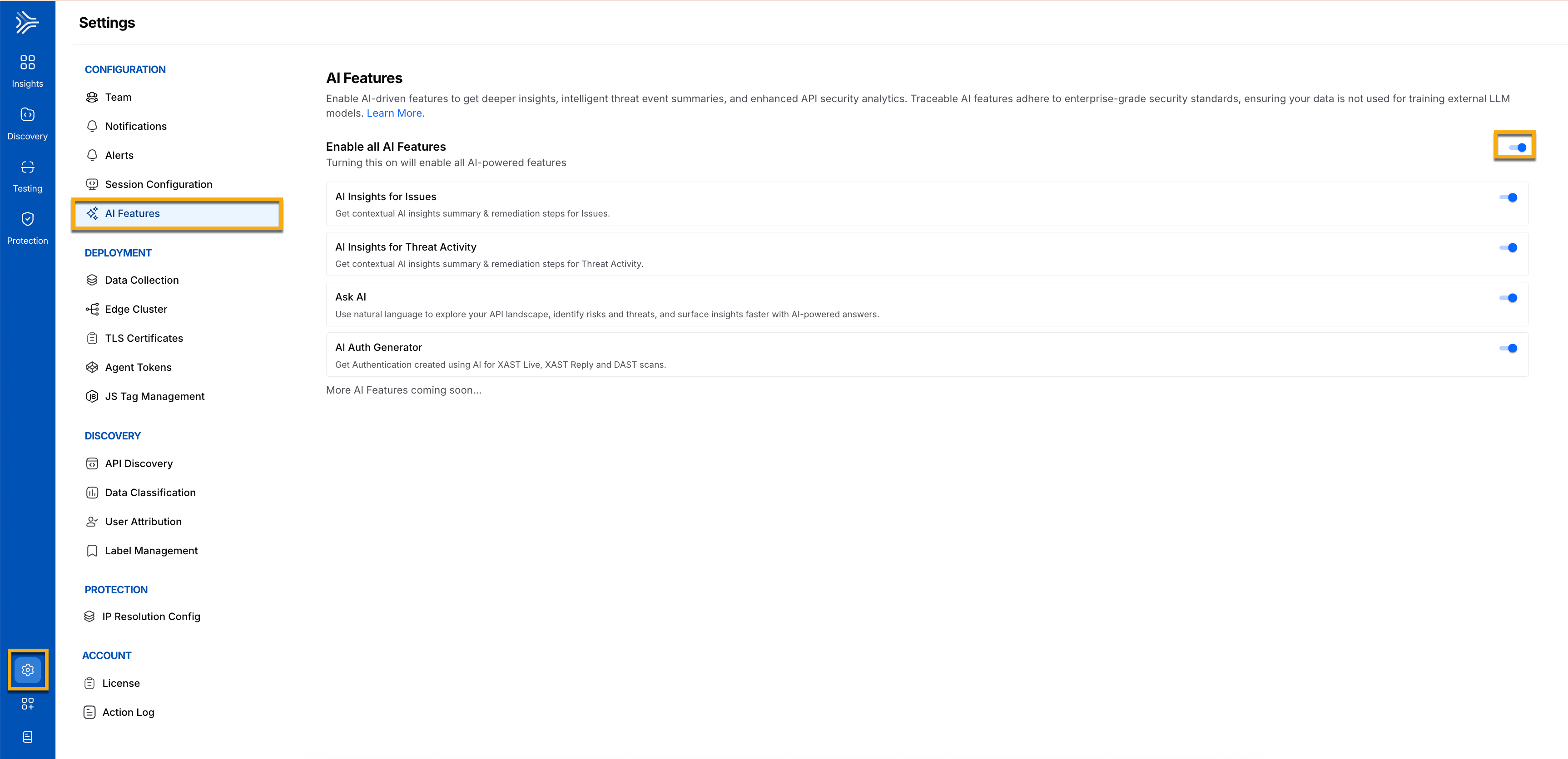
AI Feature Enablement
Integrations
Traceable integrates seamlessly with your security and DevOps ecosystem, allowing you to connect logs, SIEMs, WAFs, ticketing tools, cloud providers, and collaboration platforms to streamline alerting, analytics, response, and deliver unified API visibility and protection. The following table lists all the supported integrations:
Integration Type | Supported Integrations | Description |
|---|---|---|
CI/CD Integration | It automates your build, test, and deployment processes, helping you deliver software faster and include security checks at every stage. | |
SIEM/SOAR Integration | SIEM collects and analyzes security data from multiple sources to give you a complete view of threats. SOAR automates detection and response workflows, enabling you to act on threats more quickly. | |
WAF Integration | Traceable integrates with leading Web Application Firewalls to protect your web applications from common threats and attacks, providing centralized management and enhanced security. | |
Cloud Security Integration | Traceable provides visibility, monitoring, and protection across cloud workloads, networks, and services to help you secure your cloud environment. | |
Project Management | Traceable helps teams plan, track, and manage API security initiatives. It ensures vulnerabilities and threats are visible, assigned, and resolved efficiently within your project workflows. |
Get Notified
Traceable helps you stay informed by sending notifications across the product for essential activities and changes. In addition to event-based alerts, Traceable notifies you about security findings, policy violations, system status updates, and configuration changes that require attention. You can configure rules and delivery channels to ensure the right teams receive timely and relevant notifications, helping you respond quickly and maintain visibility across your API and Discovery. For more information, see Notification.