The risk score of an API endpoint provides a high-level overview of what likelihood and impact mean in Traceable, as well as how the risk score is calculated. It helps you to prioritize your resources in securing the APIs. A risk score is a dynamic metric calculated from the likelihood and impact of a potential API endpoint exploit. The likelihood refers to the probability or chance that an API will be exploited. The impact refers to the effect that a breach of an API endpoint may have on your infrastructure and organization.
Traceable calculates a risk score for each discovered API endpoint. A high-risk score does not necessarily mean that the endpoint is under attack. A high-risk score provides you with insight to prioritize compensating controls and monitoring activities.
You can customize the risk score in Traceable by configuring the following:
Configure the contribution of each factor to the likelihood and impact scores from their respective tabs.
(Optional) From the Calculations tab, you can modify the Risk Lookup Table or configure how the quantitative risk score is translated into a risk level.
Configurable sections in the risk score
In the entire risk-scoring exercise, the following are the categories in which you can adjust the values:
Enable or disable factors for likelihood, along with the score for each sub-factor
Enable or disable factors for impact, along with the score for each sub-factor
Values in the lookup table
Parameters
Likelihood of exploit
You can independently set the likelihood component of risk. The likelihood, as explained earlier, is the probability of a vulnerability being exploited by a threat. Traceable provides the following factors and sub-factors of likelihood.
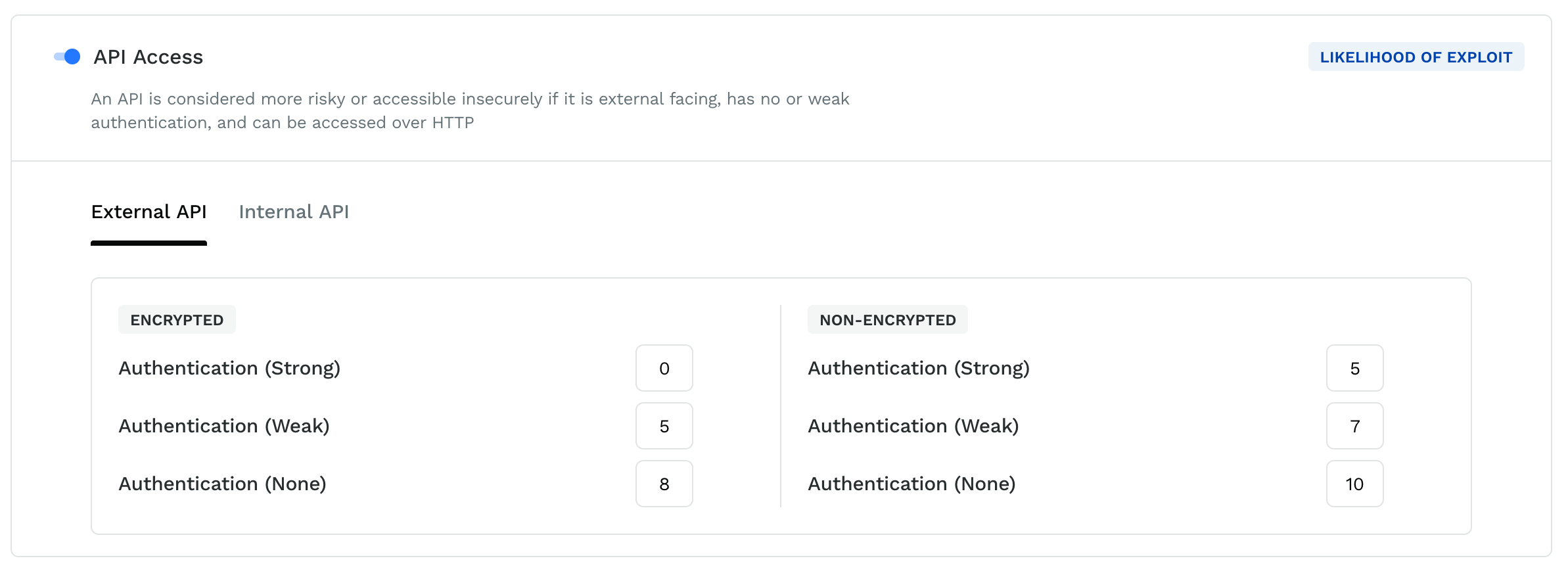
API Access
An API is considered more risky or insecure if it is external-facing, has no or weak authentication, and can be accessed over HTTP. The API access likelihood score is divided into two parts: external or internal APIs, and whether the APIs are encrypted or non-encrypted. Authentication can be weak, strong, or absent. You can provide a score that suits your API environment. For example, a 0 score for strong authentication for an external and encrypted API means that such an API would not contribute to the API access likelihood score.
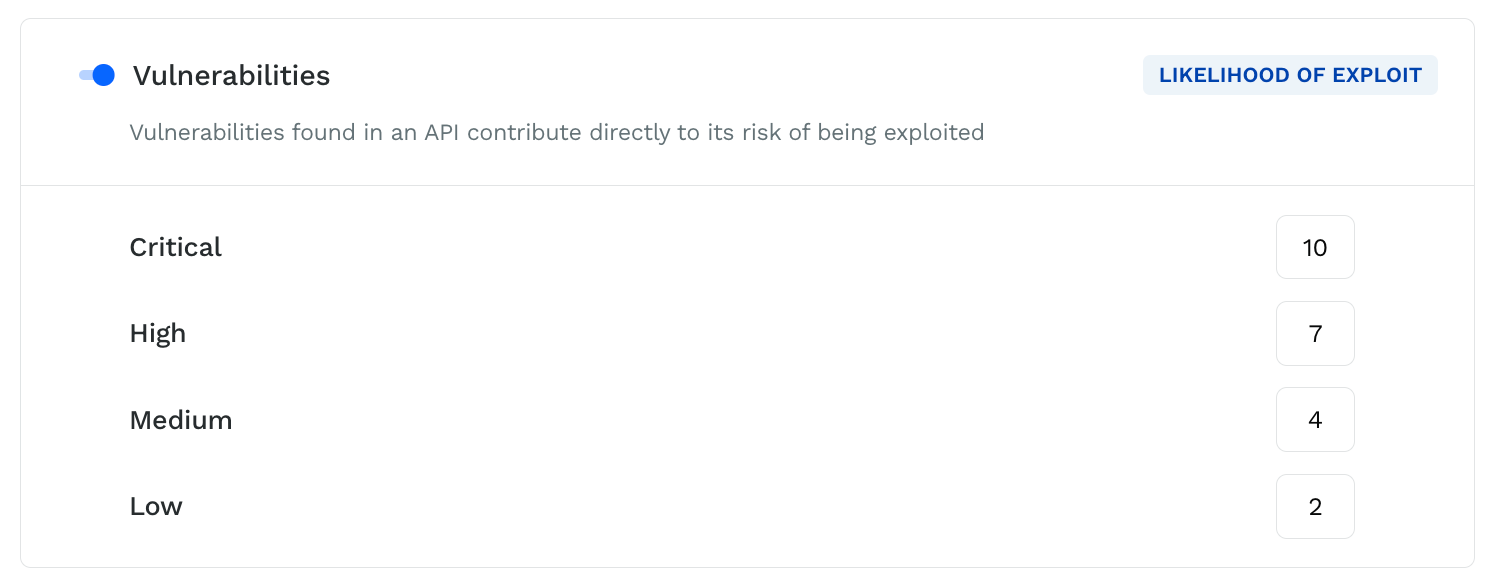
Vulnerabilities
API vulnerabilities refer to security weaknesses or flaws that exist within the interfaces of an application or system, allowing for communication with other software or systems. These vulnerabilities can be exploited by attackers to gain unauthorized access to sensitive data, execute malicious code, or disrupt the system’s functioning. Traceable categorizes vulnerabilities as High, Critical, Medium, or Low, assigning a corresponding score to each. You can customize this score to suit your API environment.
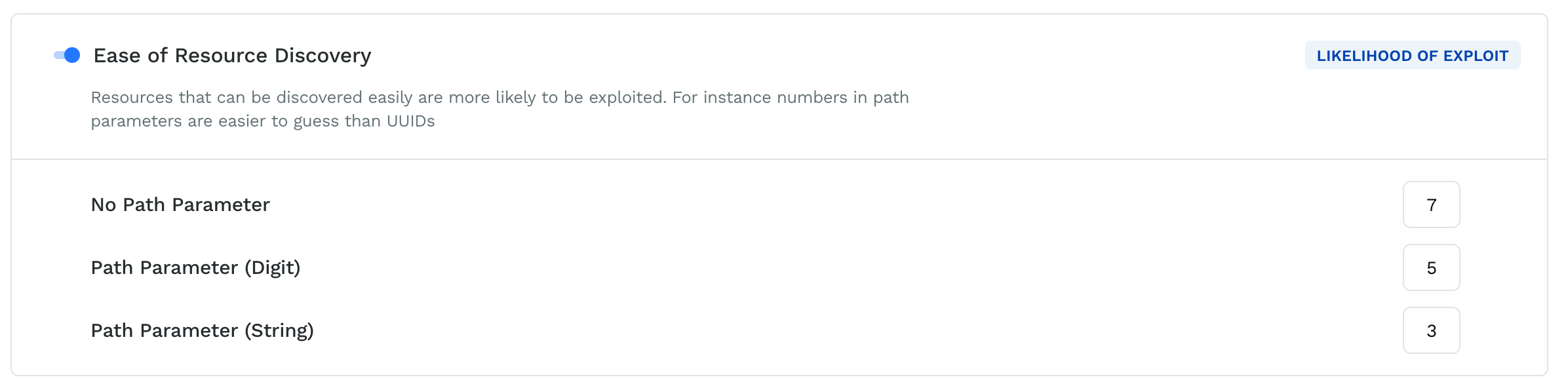
Ease of resource discovery
Ease of resource discovery regarding APIs being exploited refers to the degree to which the resources and endpoints provided by an API can be easily discovered and accessed by attackers or malicious actors seeking to exploit vulnerabilities in the API. If a resource is easily discoverable, it is more likely to be exploited easily.
Calculating likelihood score
Each sub-factor has a score ranging from 0 to 10. Traceable assigns the highest score among sub-factors as the factor score. The likelihood score is calculated by averaging the highest scores of all enabled factors.
Example
Factor | Sub-factor with the highest configured score | Score |
|---|---|---|
API Access | External non-encrypted API with no authentication | 10 |
Vulnerabilities | Critical | 10 |
Ease of resource discovery | No path parameters | 7 |
Total score = 10+10+7 = 27
Likelihood score = 27/3 = 9
A score of 9 indicates a 90% likelihood that your API may be vulnerable to the above reasons.
Note
The average is calculated by dividing by the number of enabled factors. For example, in the above calculation, if only two factors were enabled (API access and vulnerabilities and motive), then the likelihood score would be 10.
Impact of the exploit
Impact defines the effect a breach or exploitation of a vulnerability will have on your organization and business. The impact score is a key component in conducting a business impact analysis (BIA) for an organization. Traceable provides the following factors and sub-factors that impact it.
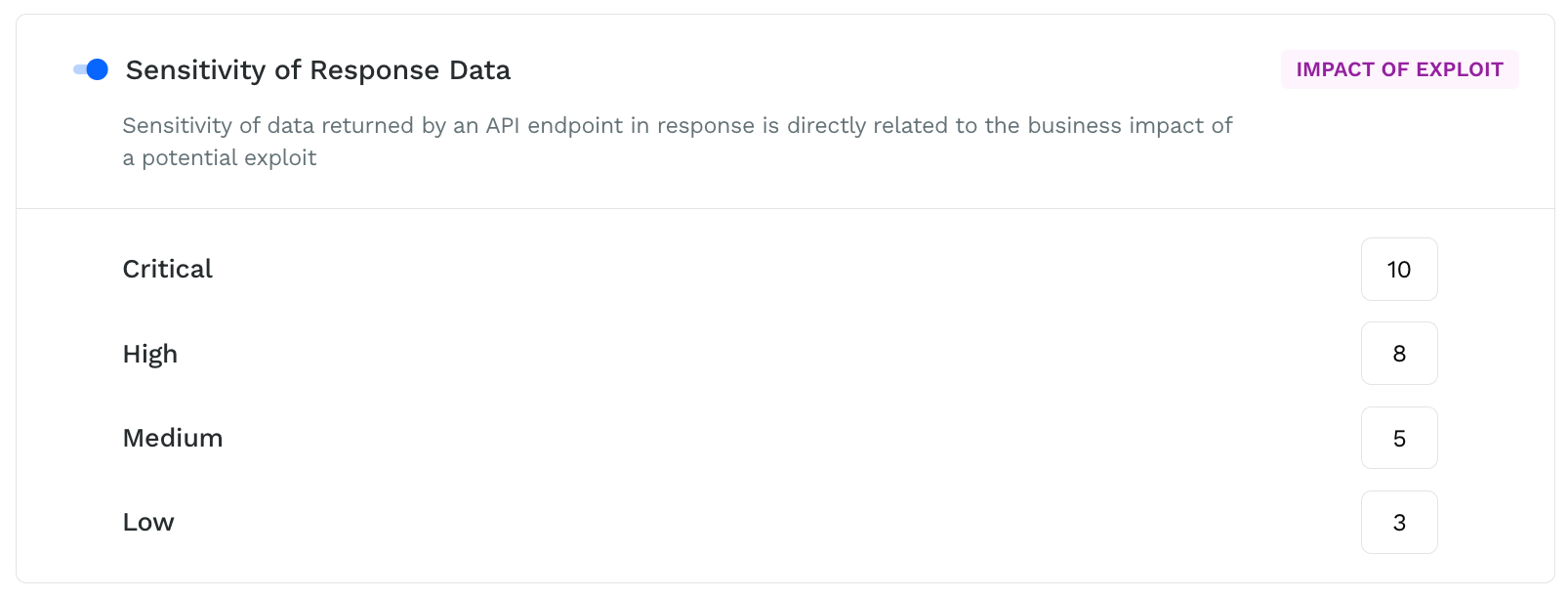
Sensitivity of response data
Sensitive data is any type of information that is considered confidential or private and that should be protected from unauthorized access or disclosure. A sensitive data exploit directly impacts the business. Traceable categorizes sensitive data as critical, high, medium, and low.
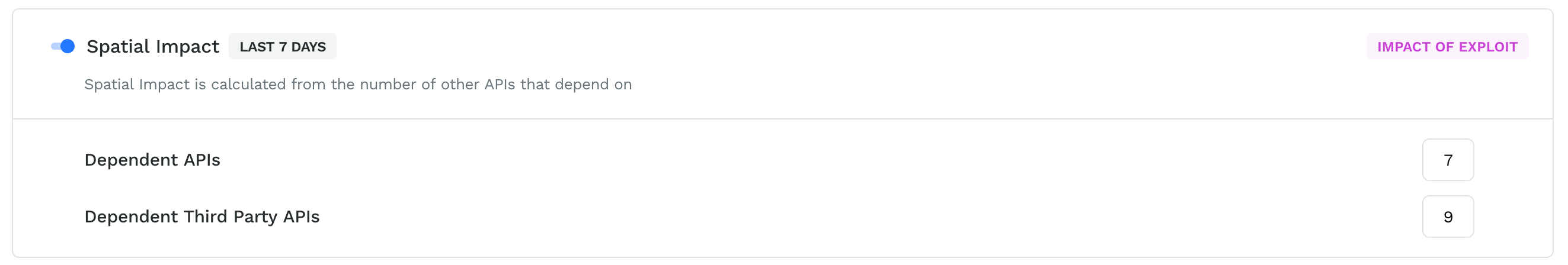
Spatial impact
The spatial impact of an API exploit refers to the extent and scope of the vulnerability or exploit's impact on the systems, applications, and users that rely on the API. The spatial impact can be localized to a specific system or application, or it can have a wider impact across multiple systems, applications, and users. In Traceable, the spatial impact is calculated from the number of other APIs that depend on the exploited API.
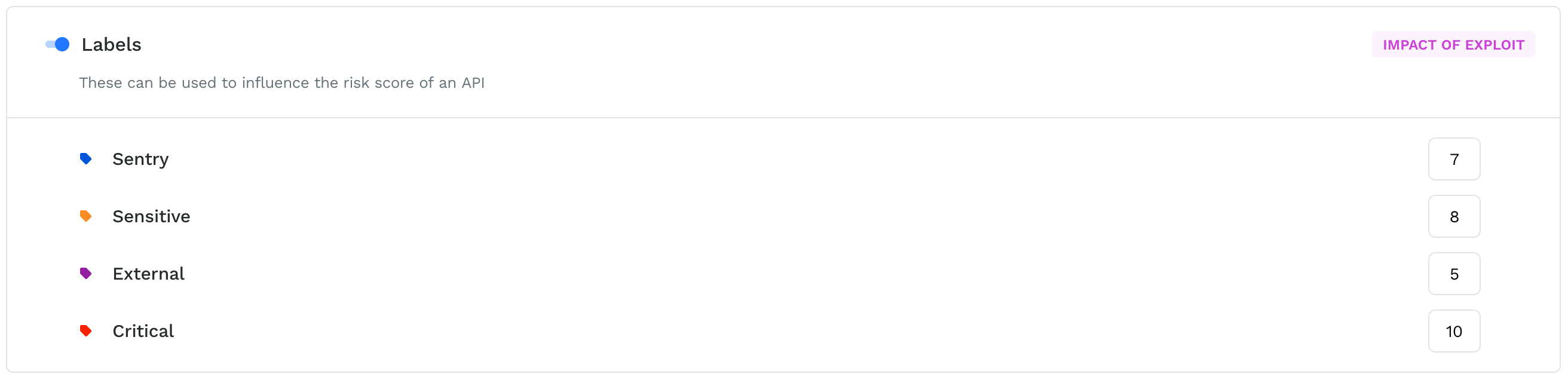
Labels
Labels form another impact category. Based on your understanding of your APIs, you can assign a score between 0-10 to the labels. This score would apply to all the API endpoints where you apply this label.
The impact score is calculated in the same way as the likelihood score. For more information, see Calculating likelihood score.
Calculations
Calculating the risk score for an endpoint consists of the following two steps:
Configure or update the lookup table. Traceable provides default values in the lookup table that will work for the majority of use cases. Before changing the default values, ensure you understand your API environment and the possible score combinations of likelihood and impact. The values can range from 0 to 10.
Find the intersection value of likelihood and impact in the lookup table to determine the risk score.
Lookup table and risk level
The lookup table maps the levels of likelihood and impact to an overall risk score value (numeric). From the Traceable platform's home page, navigate to Discovery → Settings → Risk Scoring → Calculations tab to customize the lookup table. Customizing the table is completely optional.
.png)
Lookup table
Based on your environment and risk assessment, you can configure the risk score that you want to assign for different combinations of likelihood and impact.
Calculate risk score
Based on the parameter value for each factor of likelihood and impact, the score for each factor is:
Likelihood score = (10+10+7)/3 = 27/3 = 9
Impact score = (10+9+10)/3 = 29/3 = 9.66. This would be approximated to the nearest integer, that is, 10.
(1).png)
The risk score from the lookup table would be 10, based on the intersection of a likelihood score of 9 (critical) and an impact score of 10 (also critical).
View the risk score
The risk is calculated based on the configurations that you completed above. The configurations affect the risk score of future traffic. It does not impact the current risk scores of an API endpoint until that API endpoint receives fresh traffic after the configurations are changed. You can view the risk score and the reason for that score by navigating to the Discovery → Inventory → API Endpoints tab.
.png)
The above screenshot displays the risk score of 6, along with the contributing factors that contributed to this score. It is an external unencrypted API. To correct your API definition, you can file a JIRA from this screen. For more information on Traceable's JIRA integration, see JIRA integration.
You can also view the contributing score of each category by navigating to the Risk tab. The page displays the category score that contributes the most to the overall risk score.