Updates (January 2026 to March 2026)
January 2026 — Updated the topic to add information about the rules supported in Traceable. For more information, see Integration Overview.
Google Cloud Armor is a security service provided by Google Cloud Platform (GCP) to protect web applications and services from various types of cyber threats, including distributed denial-of-service (DDoS) attacks and application-layer attacks. Google Cloud Armor features a Web Application Firewall (WAF) as one of its key components. A WAF protects web applications from various security threats, such as SQL injection, cross-site scripting (XSS), and other malicious activities targeting web applications.
What will you learn in this topic?
By the end of this topic, you will be able to understand:
An overview of the steps required to set up the Azure integration.
The prerequisites for setting up the integration.
The detailed steps for the Google Cloud Armor integration with Traceable.
The support matrix for the creation of Custom Signature rules in Traceable.
Integration Overview
This section provides high-level information on integrating Google Cloud Armor (GCA) WAF with your environment and managing threats.
Integration Setup — After deploying the agent, you can retrieve the credentials and configure the Google Cloud Armor integration. To do so, you must complete the following steps:
Prerequisites — Log in to your Google Cloud Armor account and fetch the required credentials to configure the integration. For more information, see Before you begin.
Integration — After obtaining the credentials from the previous step, navigate to the Traceable platform and configure the integration. For more information, see Add New Google Cloud Armor Integration.
Threat Management — After setting up the integration, you can establish rules to allow, block, or monitor IP addresses according to your specific requirements. Traceable supports the following rules for the Google Cloud Armor integration:
Threat Actors — Traceable enables you to track any status change of a threat actor and communicate it to Google Cloud Armor. Traceable allows creating allowlists using allowed and snoozed states, and supports blocking using deny and suspended states under threat actors. For example, if Traceable detects a threat actor and changes it to a deny state, then the requests from this threat actor can be blocked using Google Cloud Armor. For more information, see Threat actors.
Malicious Source Rules (IP Range only) — Traceable allows you to configure any malicious source rules under Protection → Policies → Custom Policies → Malicious Sources tab to enforce blocking or allow for IP ranges to be executed through Google Cloud Armor. For more information, see Custom policy. Traceable recommends going through the allow list conditions before creating any IP-range rules. For more information, see IP address allowlist.
Custom Signature Rules — Traceable allows you to set up Custom Signature rules under Protection → Policies → Custom Policies → Custom Signatures tab to block incoming requests from a specific URL by matching the corresponding endpoints. For more information, see Custom Policy and Custom signature rules support matrix.
The following is a high-level integration diagram:
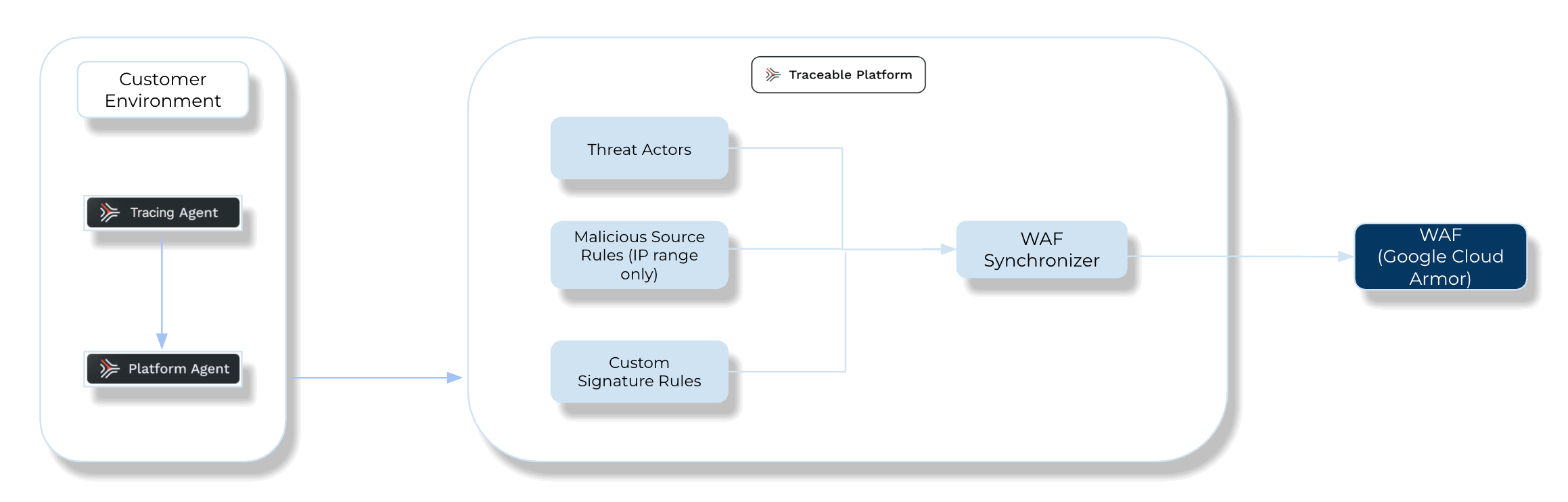
Traceable Google Cloud Armor Integration Diagram
Before you begin
Make a note of the following before you proceed with Google Cloud Armor’s integration with Traceable.
Google Cloud Armor security policy — A security policy is a set of rules that defines what action needs to be taken under which conditions, how traffic should be handled by the Web Application Firewall (WAF), and other security features. Security policies enable you to define criteria and take actions to safeguard your web applications against various attacks and security threats.
Make sure you have the following from Google Cloud Armor security policy:
The Name of the security policy, for example, traceableai.
Whether the Scope of the policy is Regional or Global.
The configured Response code.
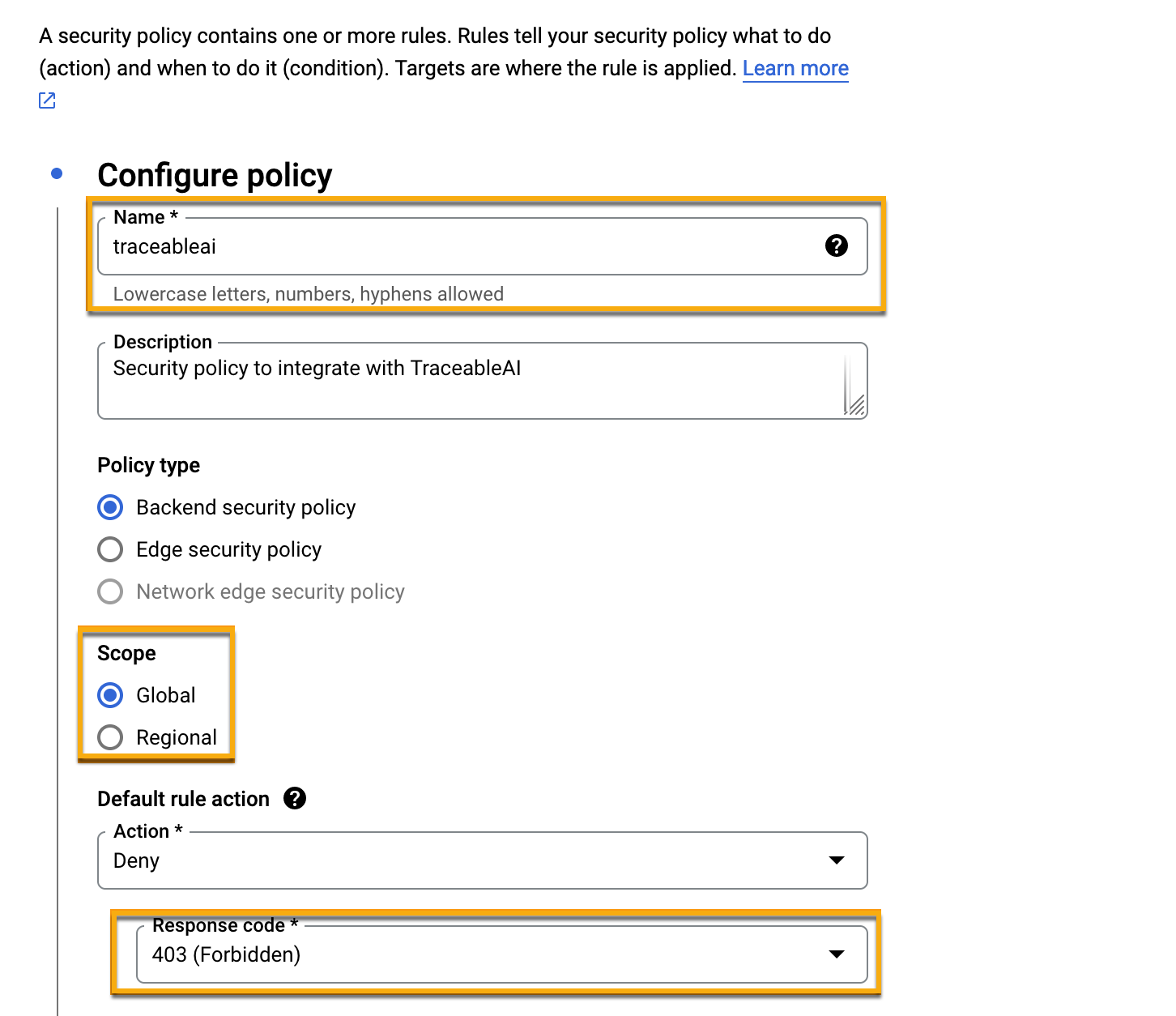
Google security policy configuration
Roles required — The following is a list of roles needed for the integration:
compute.securityPolicies.getcompute.securityPolicies.listcompute.securityPolicies.usecompute.securityPolicies.updatecompute.securityPolicies.deletecompute.backendServices.setSecurityPoliciescompute.regionSecurityPolicies.createcompute.regionSecurityPolicies.deletecompute.regionSecurityPolicies.getcompute.regionSecurityPolicies.listcompute.regionSecurityPolicies.updateFor more information on Google Cloud Armor security policy, see Configure Cloud Armor security policies.
Google Cloud Armor Project ID — Every Google project has a unique project ID assigned to it.
Service account key — A Service Account Key, also known as the JSON key, is a credentials file that allows authentication of a service account within Google Cloud Platform (GCP). It is required for enabling secure, programmatic access to GCP services and is essential for configuring a Google Cloud integration. For more information, see Create Service Account Key. Ensure that the service account key is created with the roles specified in the above section.
Add new Google Cloud Armor integration
To add a new Google Cloud Armor integration, navigate to the Integrations page from the bottom left corner of your Traceable account, and do one of the following:
Search for Google Cloud Armor in the search bar.
Navigate to WAF → Google Cloud Armor.
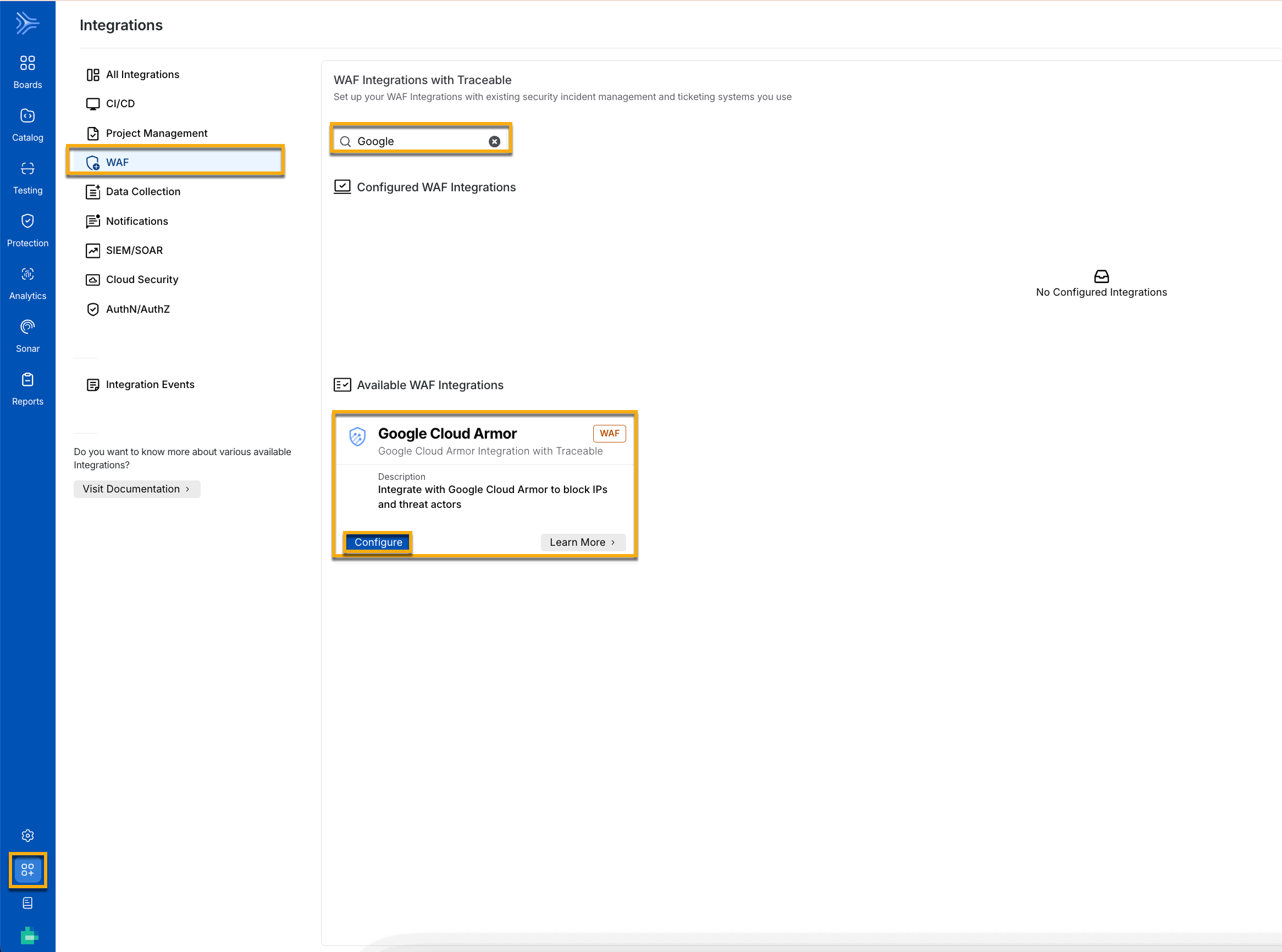
GCA Navigation
Click Configure on the Google Cloud Armor tile and complete the following steps in the Add New Google Cloud Armor Integration window:
Specify an Integration Name, for example, Google Cloud Armor integration.
(Optional) Specify a Description, for example, GCA Traceable integration.
Select one or more Traceable Environments from the Environments drop-down.
Specify the Google Cloud Armor Project ID fetched above in the Before You Begin section.
Specify the Service account key fetched above in the Before You Begin section.
Specify the Policy Name configured in the Google Cloud Armor security policy, for example, traceableai.
Specify the Policy type you configured in the Google Cloud Armor security policy above in the Before You Begin section.
Specify the Blocking Action Response Code from the drop-down list. This should match the response code you configured in the Google Cloud Armor security policy above, in the Before You Begin, for example, 403.
Click Test Connection. The Save button is enabled only after Traceable validates a successful connection.
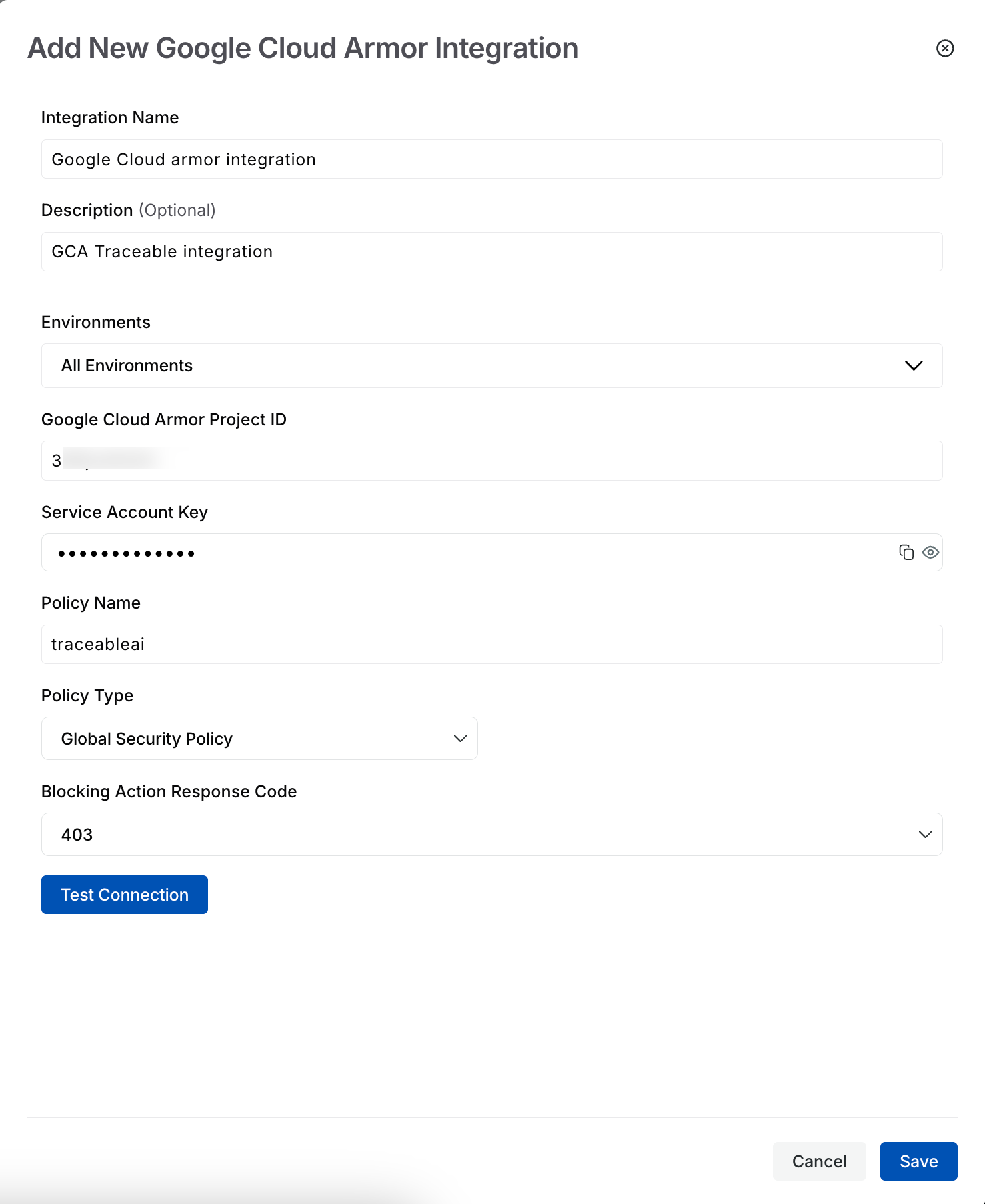
Add new GCA Integration
Note
Traceable assigns a priority to each rule. Make sure that this priority is not changed in the Google Cloud Armor security policy.
If you are creating a Malicious source rule in Traceable, there is a limit of 10 IP addresses per single rule. If you have more than 10 IP addresses in a rule, the first 10 IP addresses are considered, while the remaining addresses are ignored.
If you delete the integration, the security policy in Google Cloud Armor gets deleted. However, if you do not wish the policy to be deleted, do not add
compute.securityPolicies.deleterole to the service account key. However, if your security policy is attached to a target, such as a virtual load balancer, the policy will not be deleted.X-Forwarded-For (XFF) and X-Real-IP are not supported, only public IPs are supported.
Upon successful integration, you can see the Traceable-created rules as part of your Google Cloud Armor security policy.
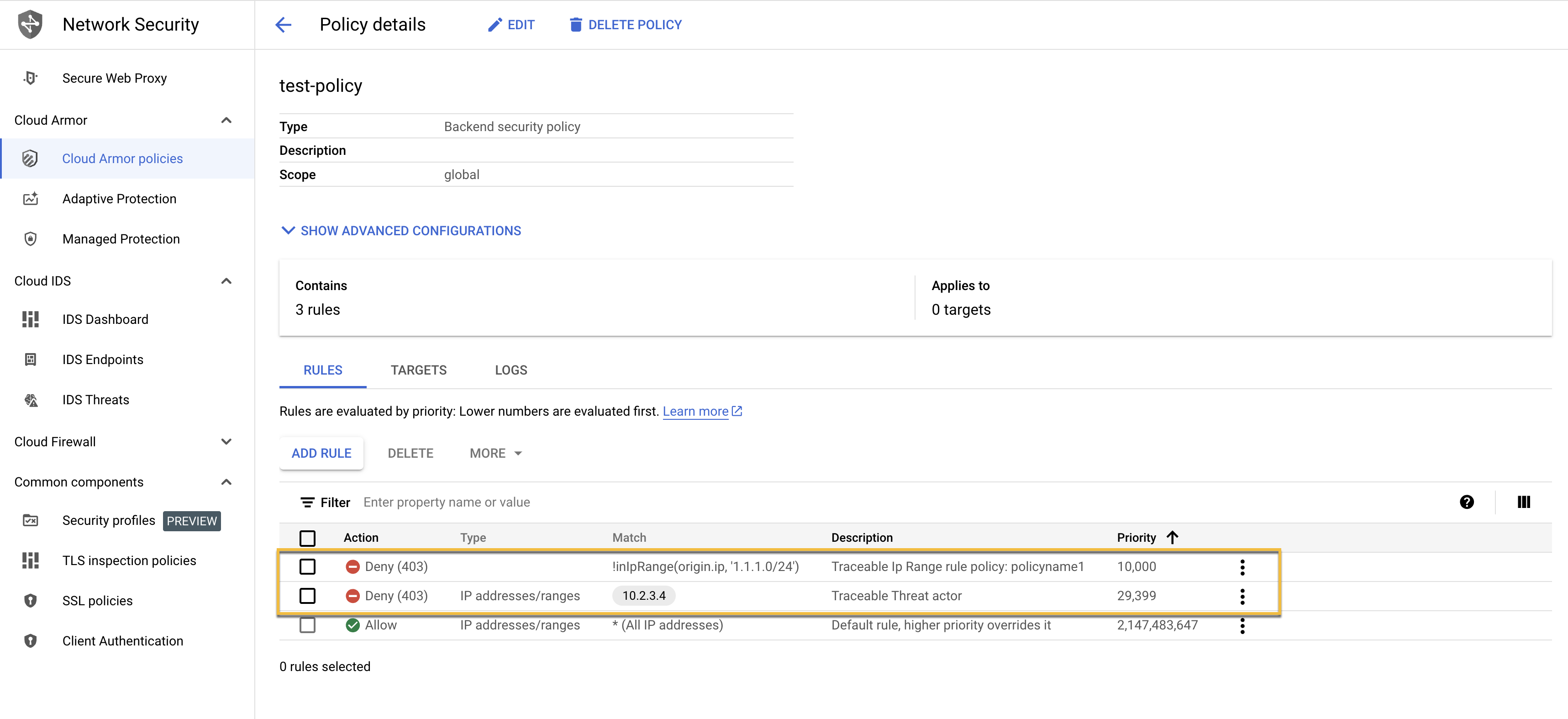
Traceable created rules in GCA
Custom signature rules support matrix
Custom signature rules allow you to define precise security policies in Google Cloud Armor using the Common Expression Language (CEL). These rules evaluate the specific request attributes, such as IP addresses, headers, URIs, and HTTP methods, to help protect your applications from unwanted or malicious traffic. For more information on attributes and expressions, see Google Cloud Armor Language Support. The Support Matrix table below describes the attributes and the supported operations to create custom signature rules in Traceable. For more information, see Support Matrix for Custom Signature Rules.