Updates (January 2026 to March 2026)
January 2026 — Updated the topic to add information about the rules supported in Traceable. For more information, see Integration Overview.
Fortinet Web Application Firewall (WAF) is a powerful security solution designed to protect web applications from various cyber threats, including SQL injection, cross-site scripting (XSS), and other vulnerabilities commonly exploited by attackers. Integrating Traceable with Fortinet WAF enables organizations to bolster their security by combining Fortinet's advanced web application protection with Traceable's deep API observability and AI-driven insights. This integration allows for enhanced visibility into API traffic, real-time detection of security anomalies, and comprehensive protection for modern web applications and APIs against sophisticated attacks. Together, Traceable and Fortinet WAF provide a unified solution that enhances detection and prevention capabilities, ensuring robust security for dynamic API environments.
What will you learn in this topic?
By the end of this topic, you will be able to understand:
An overview of the steps required to set up the integration.
The prerequisites for setting up the Fortinet integration with Traceable.
The steps to integrate Fortinet with Traceable.
The view of the created custom rules.
Integration Overview
This section provides high-level information on integrating AWS WAF with Traceable and managing threats.
Installation — Traceable allows you to choose from an agent-less or agent-based deployment option. For more information on Traceable agents, see Installation.
Integration Setup — After deploying the agent, you can retrieve the credentials and configure the Fortinet integration. To do so, you must complete the following steps:
Prerequisites — Log in to your Fortinet and fetch the required credentials to configure the integration. For more information, see Before you begin.
Integration — After obtaining the credentials from the previous steps, navigate to the Traceable platform and configure the integration. For more information, see Set up the Integration.
Threat Management — After setting up the integration, you can establish rules to allow, block, or monitor IP addresses according to your specific requirements. Traceable’s integration with Fortinet supports the following types of rules:
Threat Actors — Any status change of the threat actor on the Traceable Platform is propagated to Fortinet. For example, if Traceable detects a threat actor and changes it to a deny state, then the requests from this threat actor can be blocked using Fortinet. Moreover, if you make any changes, such as adding a threat actor to the denylist or resolving the status, these changes are reflected in Fortinet within a few minutes. Traceable allows creating allowlists using allowed and snoozed states, and supports blocking using deny and suspended states under threat actors. For more information, see Threat Actors.
Malicious Source Rules (IP range only) — If you configure any custom rules to enforce blocking, the action is to be executed through Fortinet.
Custom Signature Rules — You can set up the Custom Signature rules to block incoming requests from a specific URL by matching the corresponding endpoints. For more information, see Custom Policy.
The following is a high-level integration diagram:
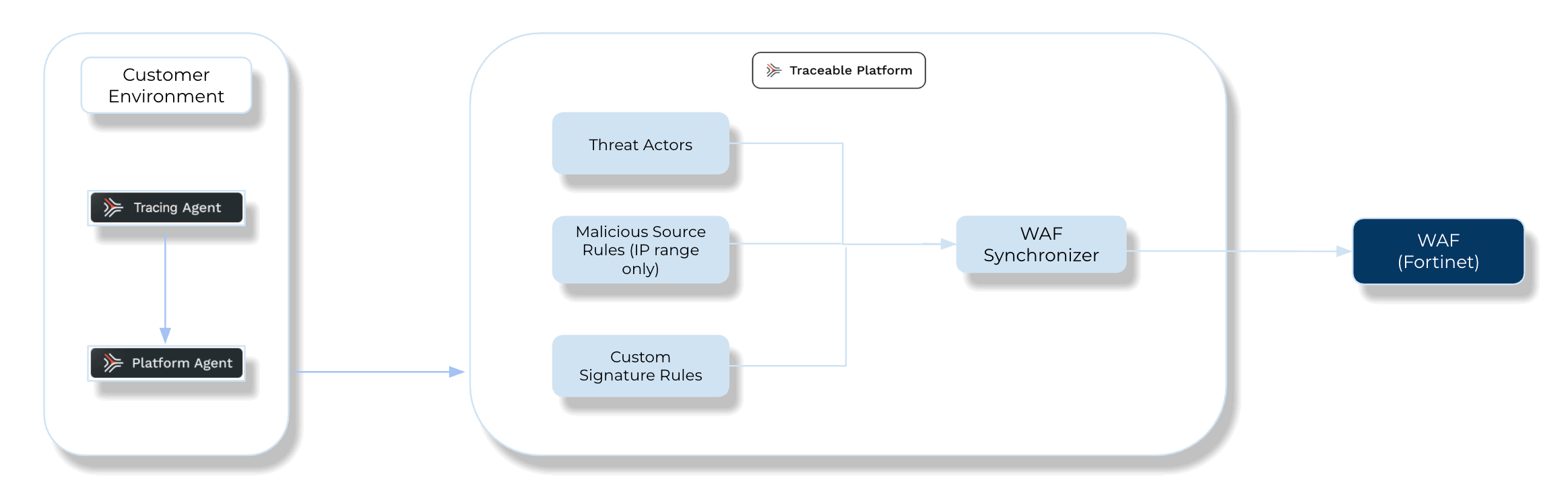
Traceable Fortinet Integration Diagram
Before you begin
Make a note of the following before you proceed with the integration:
Ensure that you have the list of supported attributes and operators for Custom Signature rules. For more information, see Support Matrix for Custom Signature Rules.
Ensure that you have the API Key. To retrieve your API Key, contact your Fortinet WAF administrator to obtain access to the key. Alternatively, you can navigate to System Settings → Settings to fetch the API key. If you are creating more than one integration, you can use the same API key for all of them.
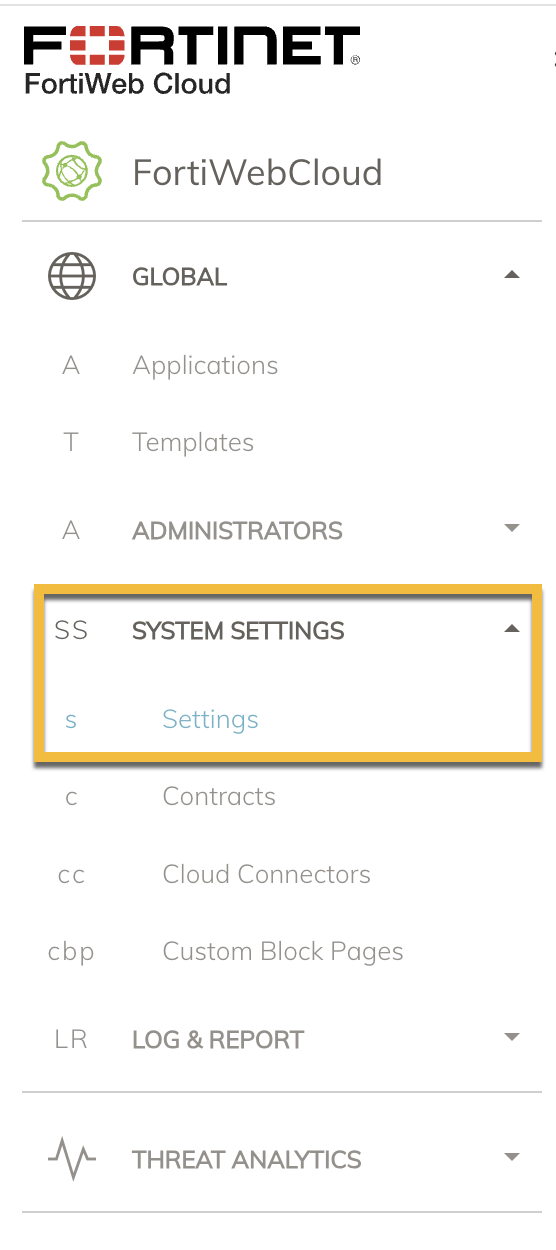
Ensure that you have the Application or Template ID. You can retrieve it from the URL. The screenshot below shows the Template ID:
.png)
Set up the Integration
To set up the Fortinet integration, log in to your Traceable account, navigate to Integrations ( ![]() ), and do one of the following:
), and do one of the following:
Search for Fortinet in the search bar.
Under All Integrations, navigate to WAF → Fortinet.
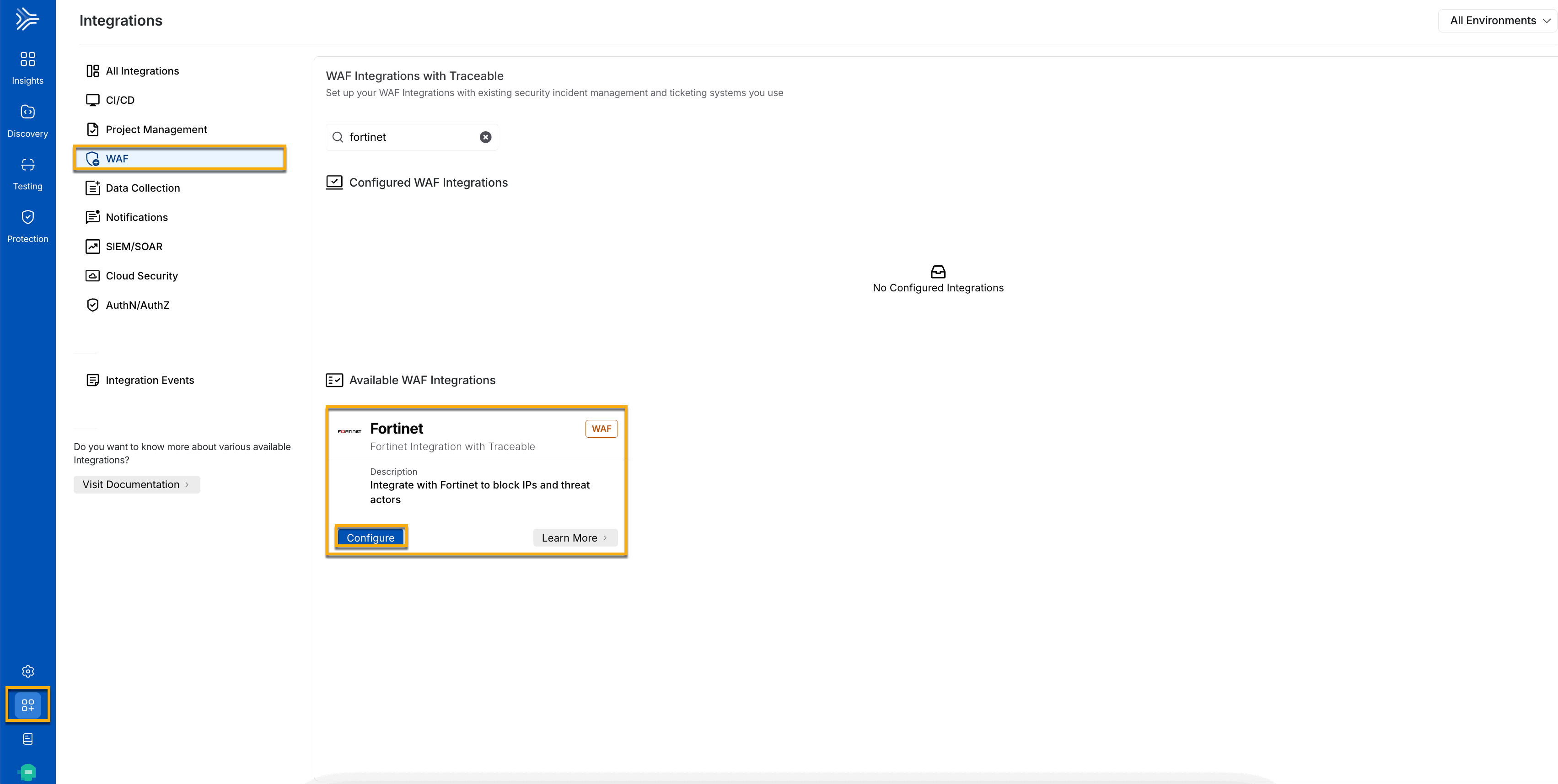
In the Fortinet widget, click Configure, and in the Add New Fortinet Integration window, complete the following details:
.png)
Add new Fortinet integration
Specify an Integration Name for the integration, for example, Fortinet_Traceable.
(Optional) Specify the Description.
Select the environment(s) for which you wish to integrate Fortinet. You can also choose All Environments, which will integrate Fortinet with all the available environments.
Specify the API Key. For more information, see Before you begin.
Specify the Rule scope. You can apply this integration at an Application or Template level. A template-level integration will be applied to all the applications using the template. This means that all the rules applicable to the template will also be applied to applications that inherit from that template. Meanwhile, application-level integration applies to a specific application in Fortinet.
Click Test Connection and after verification save is enabled.
Click Save to save the integration.
View the Rules
You can view the custom rules by navigating to Advanced Applications → Custom rules.
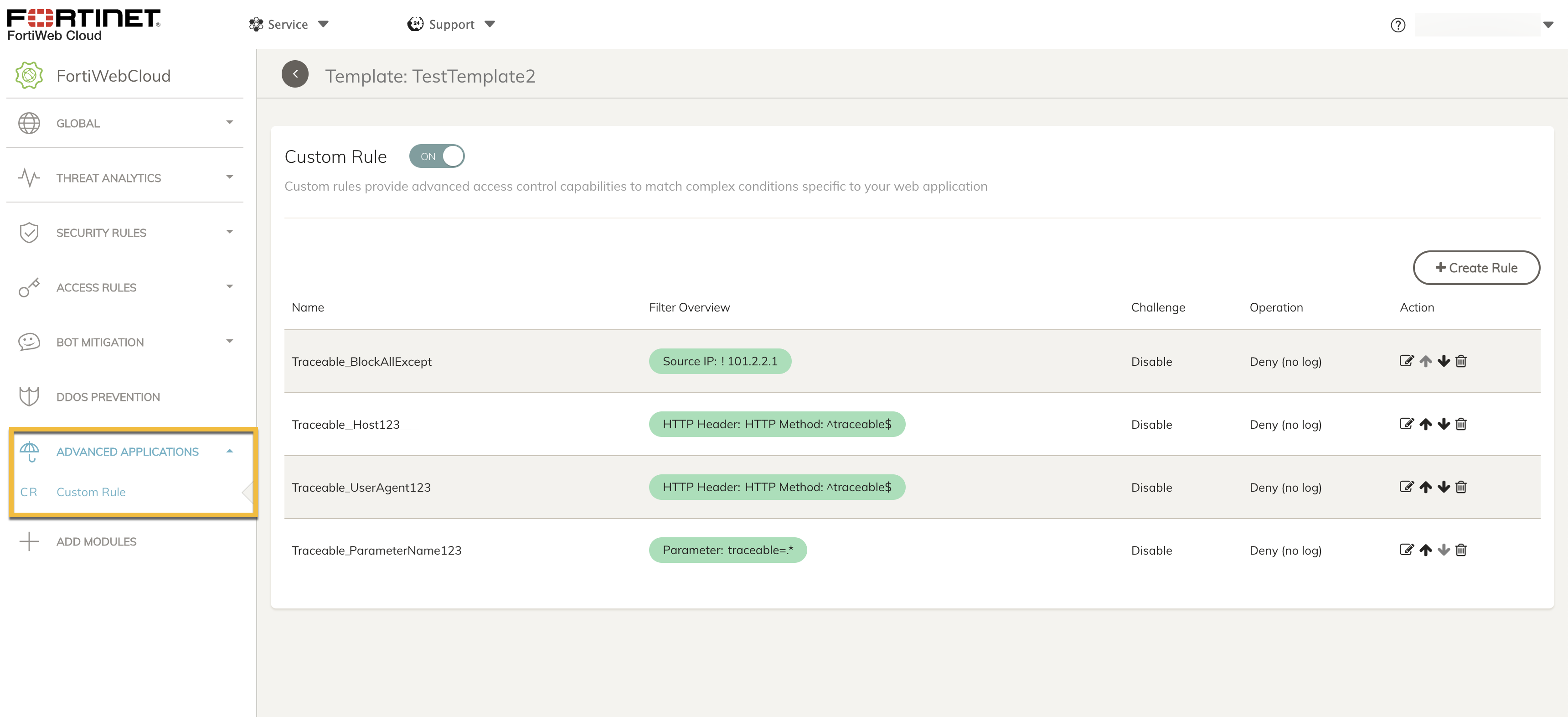
Viewing Custom Rules
Note
If a rule is deleted from a template, it is automatically deleted from all the applications that inherit that template.
Traceable adds all the threat actors to a single rule and synchronizes with Fortinet WAF.
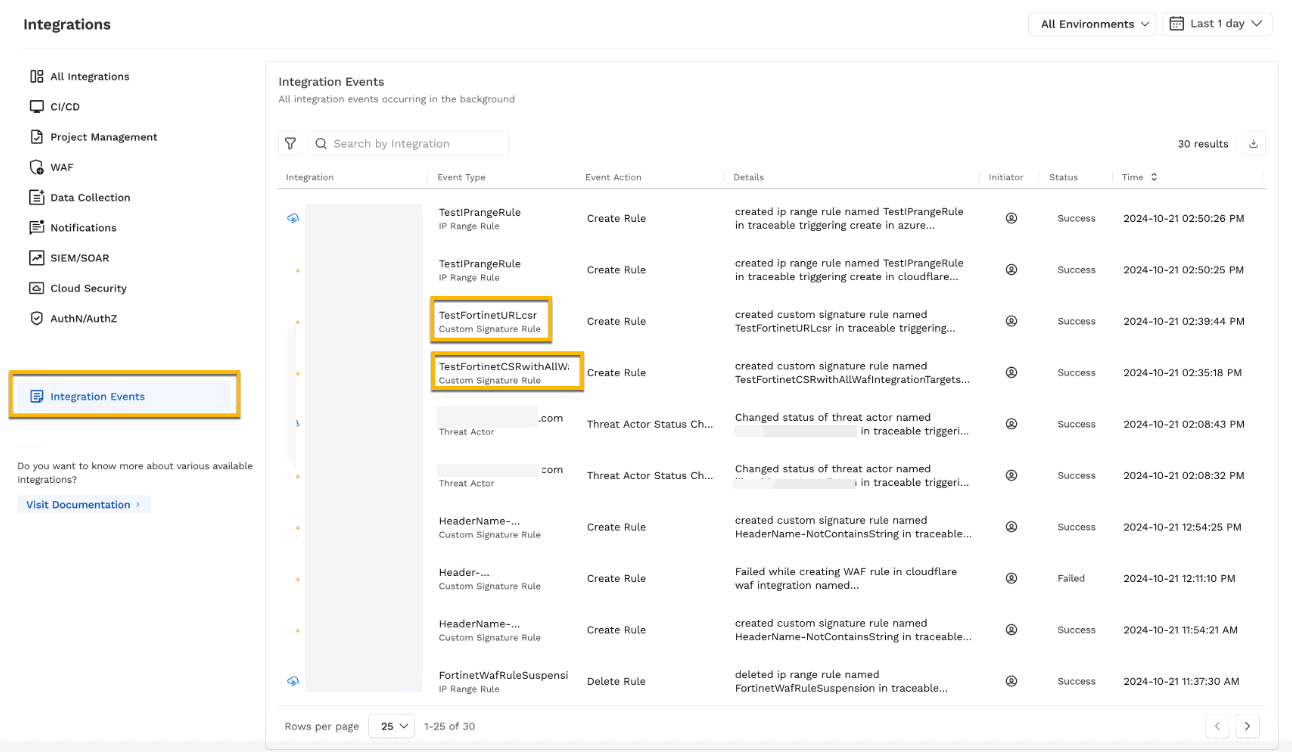
A maximum of 24 rules can be created in Fortinet WAF. To view which rules have been synchronized, navigate to Integrations → Integration Events.
When you delete an integration in Traceable, all the rules are deleted from Fortinet.
If you have more than one Template in Fortinet and wish to integrate them, you must create multiple integrations in Traceable.
If you wish to block a request, you must manually enable blocking in Fortinet.
Integration Events