Vulnerability Types are the security weaknesses in your application that Traceable can detect during API security testing. Traceable checks for these weaknesses, as they may be potential threats, such as a JWT anomaly or local file inclusion. Traceable allows you to configure and manage vulnerability types according to your requirements.
Vulnerability Types
The vulnerability types are divided into two categories:
Traceable — This category lists the out-of-the-box vulnerability types Traceable provides. These vulnerability types help you identify some of the most common threats. While default values are assigned to each attribute in a vulnerability type, you can edit some of these attributes according to your requirements. For more information, see Traceable vulnerability type.
Custom — This category lists the vulnerability types you create by defining logic, such as severity and tags, according to your requirements. For more information, see Custom vulnerability type.
While creating a policy, you can select the vulnerability type you want Traceable to check for in your APIs. Based on your selection, Traceable checks for vulnerabilities as part of scans.
Note
Custom vulnerability types should be linked to a custom plugin for it to be visible while creating a policy.
Traceable Vulnerability Type
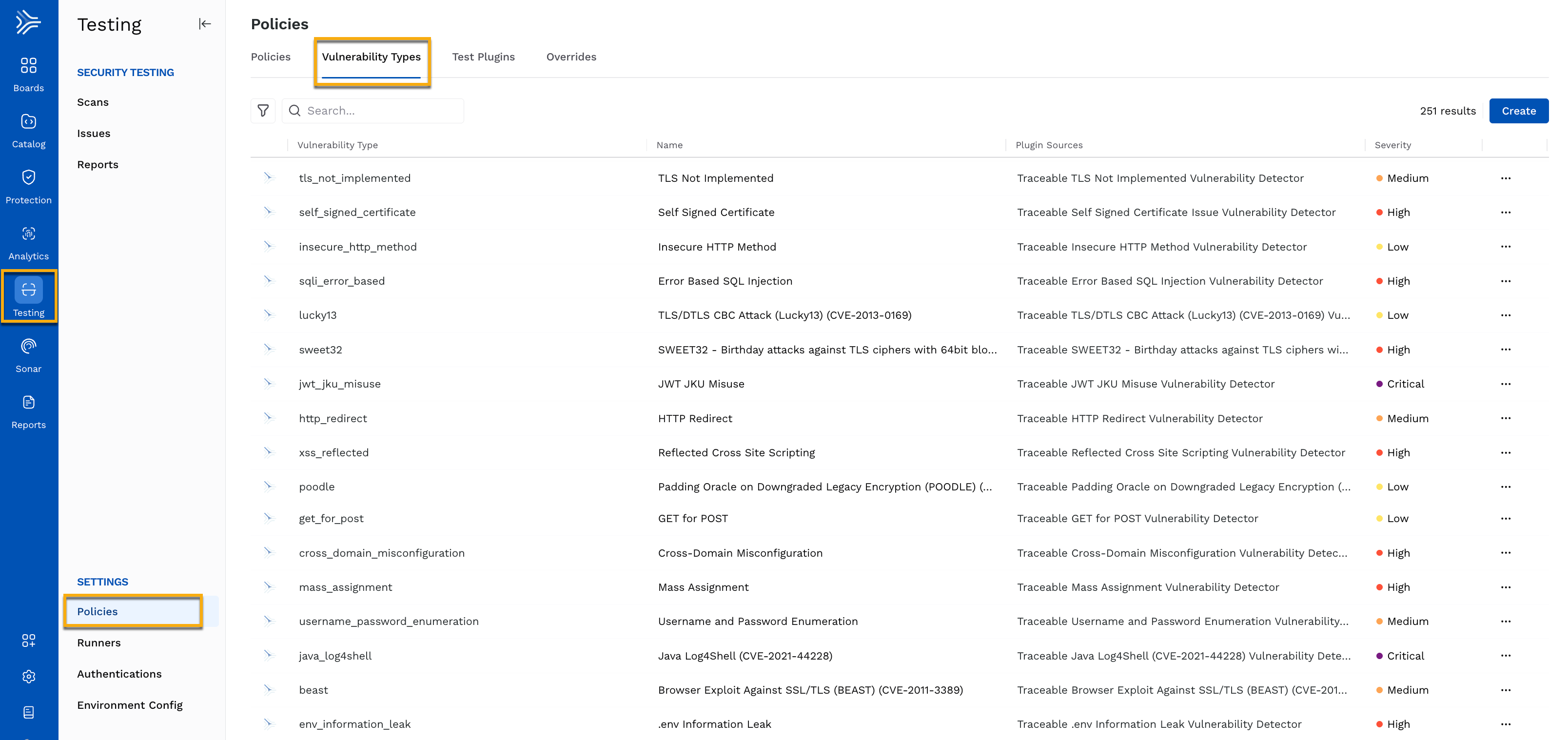
Traceable, by default, provides you with some vulnerability types on the Vulnerability Types page. On this page, under the Traceable tab, you can view the following:
Vulnerability Type — The type of vulnerability Traceable can detect.
Plugin Sources — The test plugin that detects the vulnerability type. For more information, see Plugins.
Severity — The severity assigned to the vulnerability type.
You can also edit some attributes in these pre-defined vulnerabilities to fine-tune them according to your requirements. To edit a pre-defined vulnerability type, complete the following steps:
Editing Traceable Vulnerability Type
Click the Ellipse (
 ) icon corresponding to the vulnerability type you want to edit.
) icon corresponding to the vulnerability type you want to edit.Click Edit.
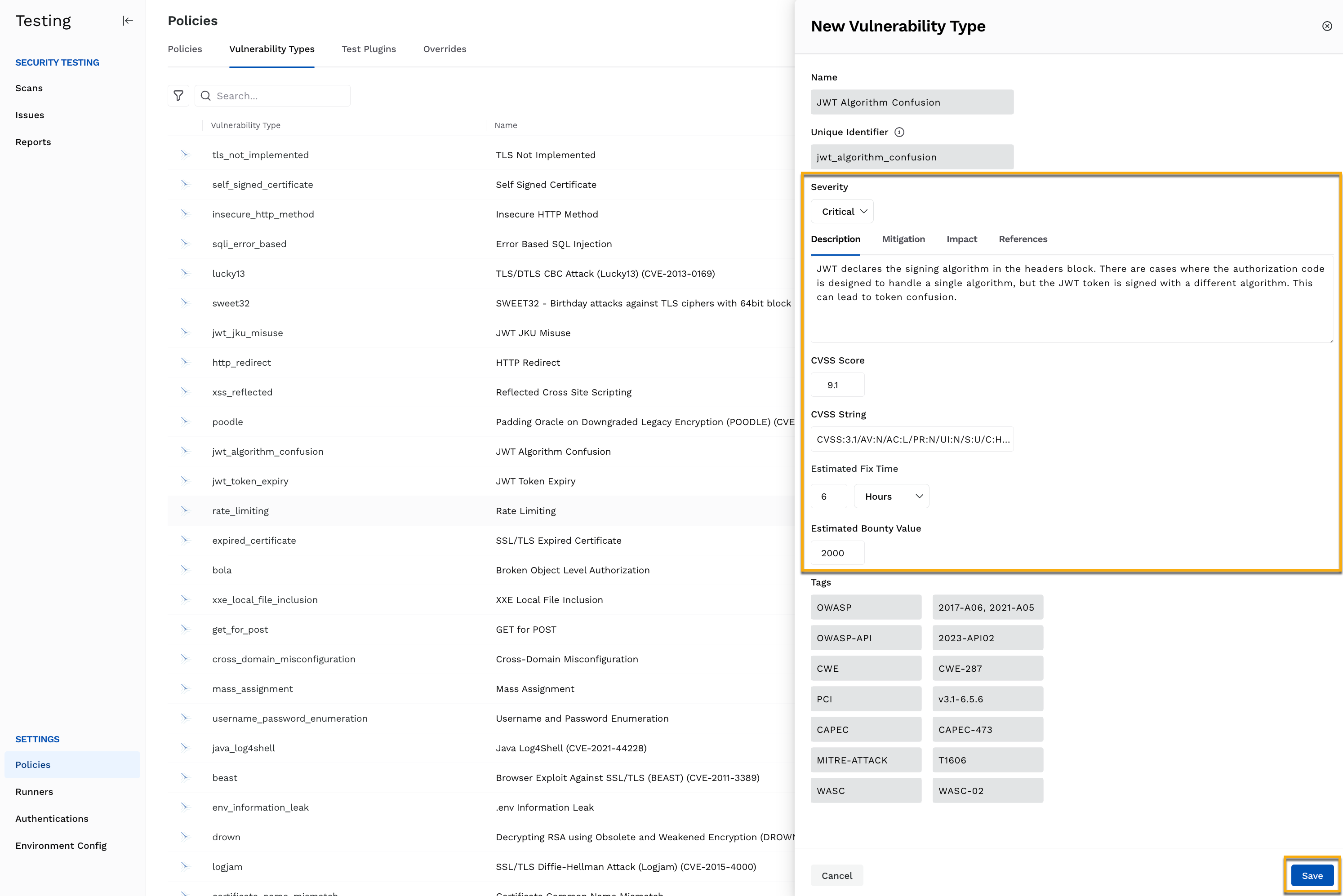
In the Edit Vulnerability Type screen, do the following according to your requirements:
Update the Severity, for example, Critical.
Update the Description, Mitigation, Impact, and References tabs.
Update the CVSS score, for example, 9.8.
Update the CVSS string, for example, CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H.
Update the Estimated Fix Time (hours), for example, 18.
Update the Estimated Bounty Value, for example, 2000.
Click Save.
You can reset the vulnerability type to its original state by clicking the Ellipse (![]() ) icon → Reset.
) icon → Reset.
Custom Vulnerability Type
You can create custom vulnerability types by specifying various attributes according to your requirements. You can use these vulnerability types while creating a custom plugin.
To define a custom vulnerability type, complete the following steps:
Creating Custom Vulnerability Type
In the page’s top right corner, click Create.
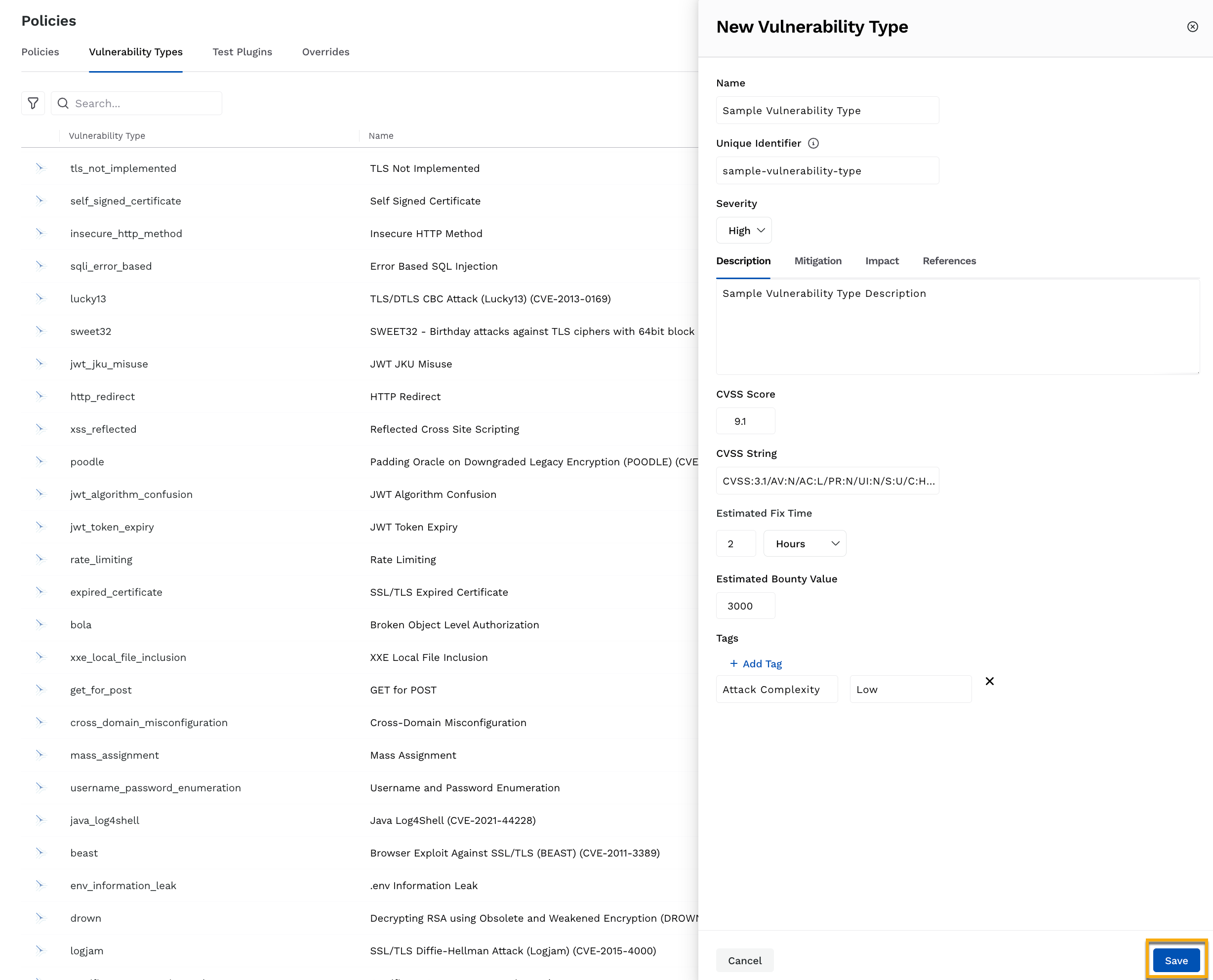
In the New Vulnerability Type pop-up window, complete the following:
Specify a Name for the vulnerability type.
(Optional) Modify the Unique Identifier Traceable automatically generated based on the name you specified above.
Select the Severity of the vulnerability type.
Specify the Description, Mitigation, Impact, and References for the vulnerability type.
Specify the CVSS Score.
Specify the CVSS String.
Select the Estimated Fix Time.
Specify the Estimated Bounty Value.
Click + Add Tag and specify the Key and Value for custom labels that you wish to assign to the vulnerability.
Click Save.
Note
The Name, Unique Identifier, and Tags cannot be modified post-creation.
You can view the created vulnerability type under the Custom tab. You can also click the Ellipse (![]() ) icon corresponding to a vulnerability type to edit or delete it.
) icon corresponding to a vulnerability type to edit or delete it.