Updates (October 2025 to December 2025)
October 2025 — Updated the page to add information about the AI attack category (Beta) available in Traceable.
Policies in API Security Testing (AST) define the vulnerability types you want Traceable to detect in your endpoints, including any AI endpoints. AST scans execute attacks on your API endpoints and detect the selected vulnerabilities. You can select the attacks in either of the following ways:
Specific attacks — Traceable runs your selected tests on the API endpoints when you choose this option.
All attacks — Traceable runs all available tests on your API endpoints when you choose this option. However, this may be time-consuming.
Rule-based attacks—Traceable runs the available tests on the API endpoints based on the filters you apply when you choose this option. For example, the filters in the screenshot identify Security Misconfiguration and High-severity vulnerabilities.
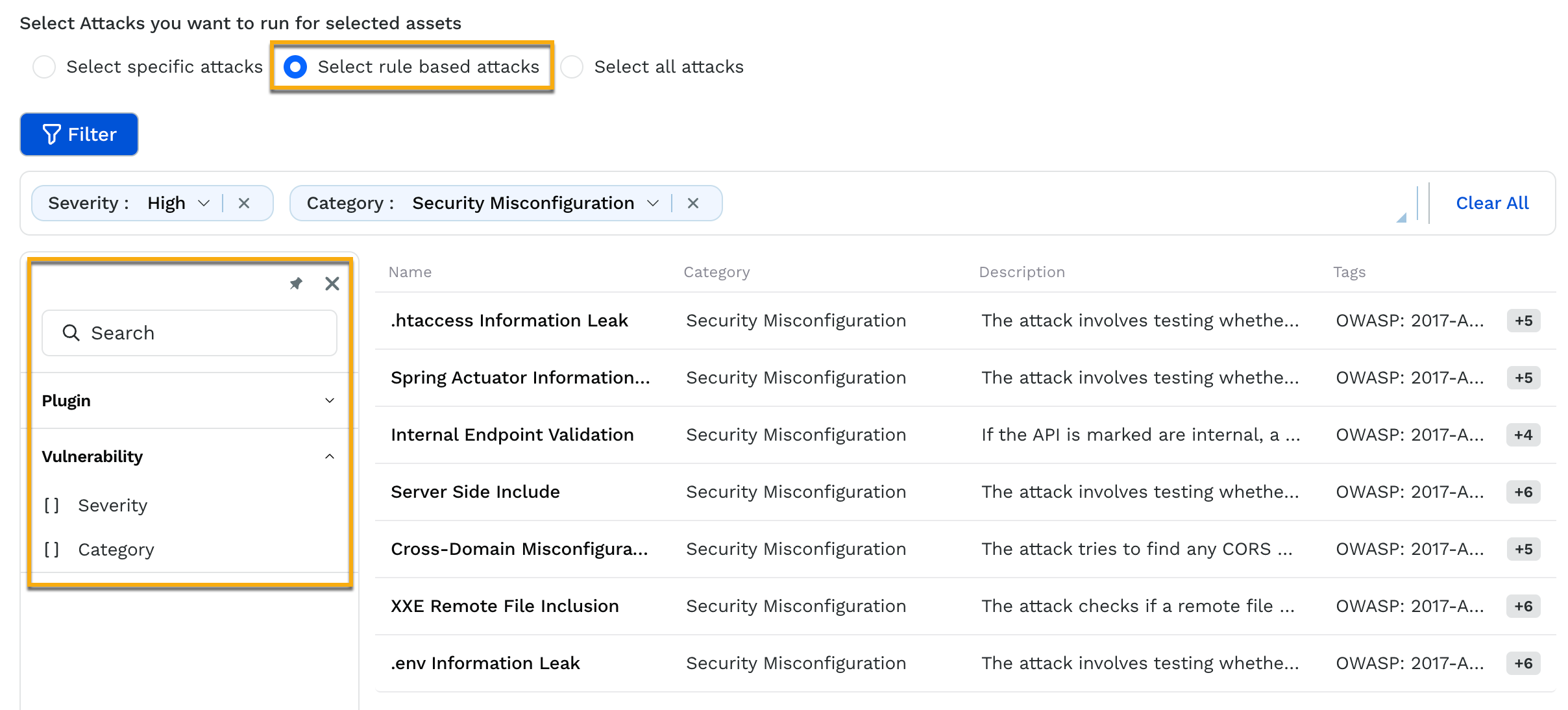
Rule-based Attacks
You can choose from the above attacks according to your requirements while creating a policy. For information on the attack recommendations you can use based on the scan you wish to create using the above policy, see Scan Creation Recommendations.
For all the categories of attacks, Traceable describes each attack and the OWASP category into which it falls. All the attacks fall into one of the following categories:
Server-side request forgery
Security misconfiguration
JSON Web Token
Access control
Insecure design
SQL injection
Authorization
Improper asset management
Remote code execution
Data Exposure
Cross-site scripting
Security headers
TLS
No SQL injection
Business logic
Authentication
AI
Note
To run a scan, you need at least one policy. Policies apply to All Environments.
Creating a Policy
To create a policy, navigate to Testing → Policies and click Create Scan Policy. Creating a policy is a 3-step process:
.png)
AST Scan Policy
Select the attacks — Specify the Policy name and select the attacks from one of the three ways listed above.
Advance configuration — You can select the following advanced configurations:
Attack methods — Choose from GET, PUT, POST, DELETE, and PATCH.
Attack coverage — This advanced option lets you choose the type of tests you wish to run:
Smoke — These are basic security tests for continuous coverage.
Optimized — Traceable runs fewer, smarter tests using selective payloads and learned data when you select this option.
Exhaustive — When you choose this option, Traceable attempts to cover all the scenarios with all possible attacks.
Run only safe attacks — Choose this option to run API Security Tests directly in the production environment. The tests run when you select this option are non-disruptive.
Save the policy — Traceable displays a policy summary as the final step. Click on Create Policy to save the policy.