Updates ( July 2025 to September 2025)
September 2025 — Updated the topic to add a new HEC-supported SIEM platform, CrowdStrike, to better monitor and analyze threats in Traceable. For more information, see Generate the API Credentials from your SIEM platform.
The HTTP Event Collector (HEC) is a secure, token-based system that allows sending logs, events, and other relevant data without requiring additional software installation or login credentials. It simplifies integration, eliminates the need for agents, supports structured data, such as JSON, and enables users to monitor and respond to issues quickly.
Traceable automatically streams real-time data to the external platform, supporting seamless monitoring, analysis, and alerting. This enables you to send and collect data quickly and safely from anywhere, providing real-time visibility and actionable insights. Traceable currently integrates with the following SIEM platforms, Splunk and CrowdStrike, through HEC to deliver real-time API security data. This ensures that API-specific insights, including attack patterns, anomalies, and sensitive data risks, are streamed directly into the SIEM platform for centralized visibility. Traceable provides a seamless, secure, and scalable way to connect API security intelligence with enterprise security workflows by forwarding data through HEC. This integration connects Traceable events with threat data, helping teams investigate faster and strengthen overall response efforts.
Note
HEC is available for Splunk and CrowdStrike integration. For more information, see Generate the API Credentials from your SIEM platform.
HEC is available across all environments.
What will you learn in this topic?
By the end of this topic, you will be able to:
Understand the need for HTTP Event Collector (HEC).
Understand the prerequisites for the CrowdStrike or Splunk integration.
Understand the steps to add a new HEC integration with Traceable.
Understand the steps to set up a notification channel to receive updates about HEC.
Before you begin
Make a note of the following before proceeding with the integration:
(For Splunk only) Make sure that you have the HTTP Event Collector (HEC) URL and the API token from the Splunk platform. For more information, see Generate the API Credentials from your SIEM platform.
(For CrowdStrike only) Make sure that you have the HTTP Event Collector (HEC) URL and the API token from the CrowdStrike platform. For more information, see Generate the API Credentials from your SIEM platform.
Generate the API Credentials from your SIEM platform
Traceable allows you to integrate with the following SIEM platforms:
Splunk SIEM gives you real-time monitoring and early threat detection so your team can identify issues quickly, respond faster, and stay ahead of modern threats. By using the Splunk HTTP Event Collector (HEC), you can send Traceable alert notifications over HTTP or HTTPS directly into Splunk, where your operations team can easily review and take the necessary actions. Traceable automatically sends threat activity and detection events to Splunk for analysis and investigation. This integration simplifies monitoring and gives your team a single place to capture and respond to critical security events quickly.
To fetch the HTTP Event Collector URL and the API token for Traceable integration, see Configure HTTP Event Collector on Splunk Cloud Platform and follow the steps. Now, you can use this API token and URL for HEC integration. For more information, see Add New HTTP Event Collector Integration.
Traceable integrates with CrowdStrike via its SIEM/SOAR integration. CrowdStrike is a cloud-native platform that centralizes threat data and uses AI-driven analytics to detect and respond to security incidents. It helps us provide deep API security insights such as attack patterns, anomalous behaviors, and sensitive data exposure. This enables faster incident response, improved correlation with enterprise-wide threats, and a stronger overall security posture.
To fetch the API Key (Token) and the API URL for integrating with Traceable, log in to your CrowdStrike account and complete the following steps:
Navigate to Data Connectors → Data Connections in Falcon.
.png)
Select HEC/HTTP Event Collector, and click Configure.
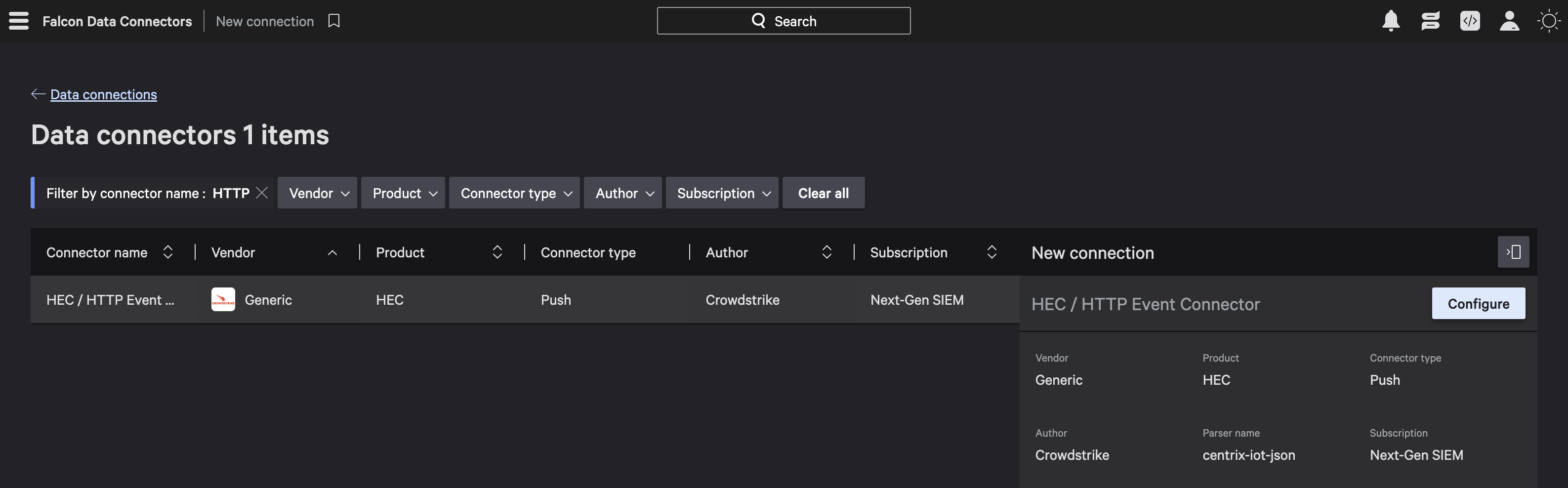
Under Add new connector provide the Connector details and Parser details to configure it.
Specify a suitable data source name, for example, traceable.
Specify a connector name, for example, traceable-http-collector.
Select kv (Generic Source) as the Parsers, and click Save.
(1).png)
Click Regenerate API Key to fetch the API key.
 (1)(2).png)
Copy the API URL and the API Key required for the integration. For more information, see CrowdStrike URL and API Token Generation.
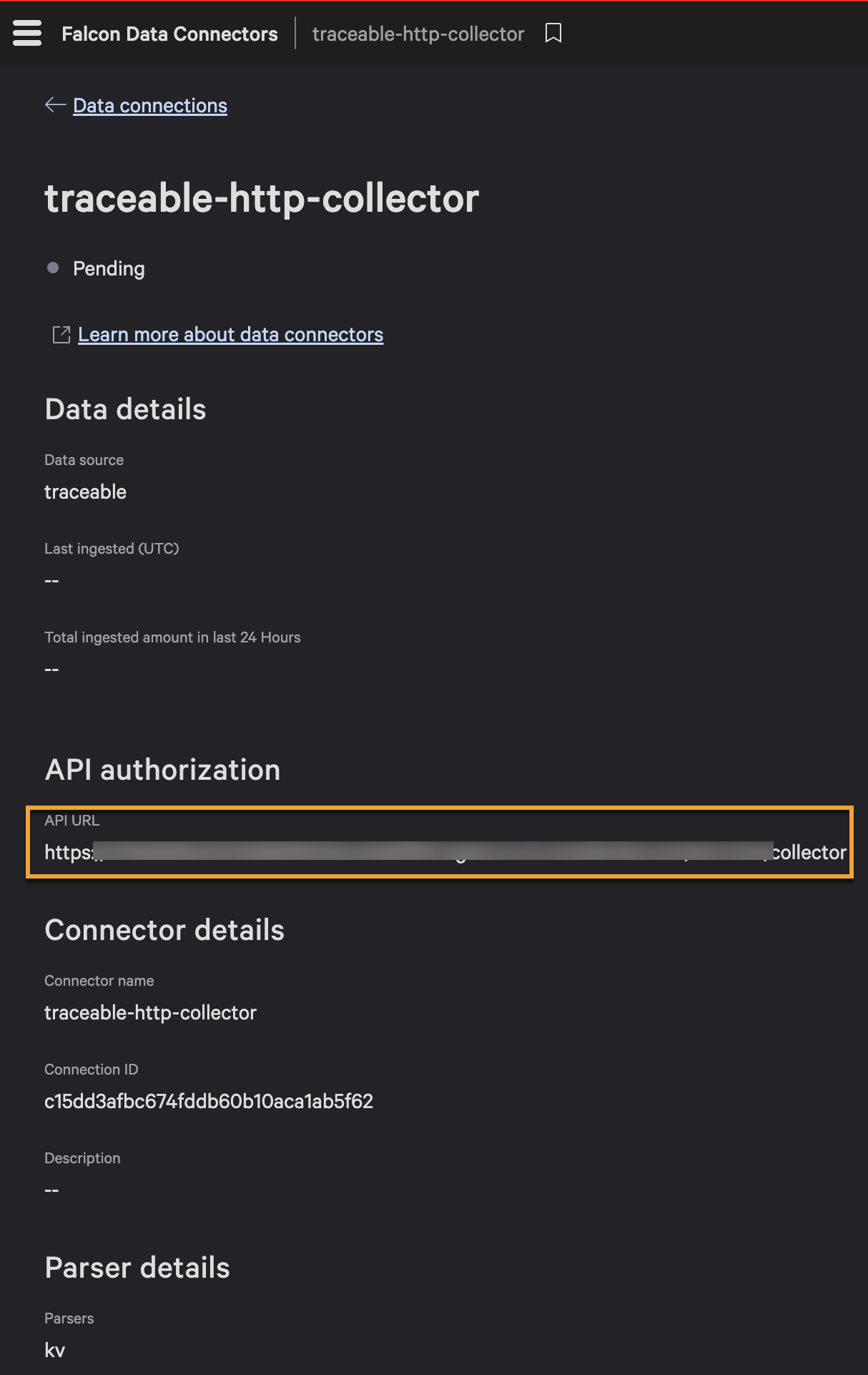
You can now use this API key( token) and the API URL for setting up the HEC integration. For more information, see Add New HTTP Event Collector Integration.
Set up the integration
The HTTP Event Collector (HEC) integration is configured to receive data over HTTP(s). You can set up this integration to allow Traceable to send security events directly to Splunk or CrowdStrike for real-time threat detection. To set up the integration, complete the following steps:
Step 1 — Add New HTTP Event Collector Integration
Log in to your Traceable account, navigate to Integrations ( ![]() ), and do one of the following:
), and do one of the following:
Under All Integrations, search for HTTP Event Collector in the search bar.
Under All Integrations, navigate to SIEM/SOAR → HTTP Event Collector.
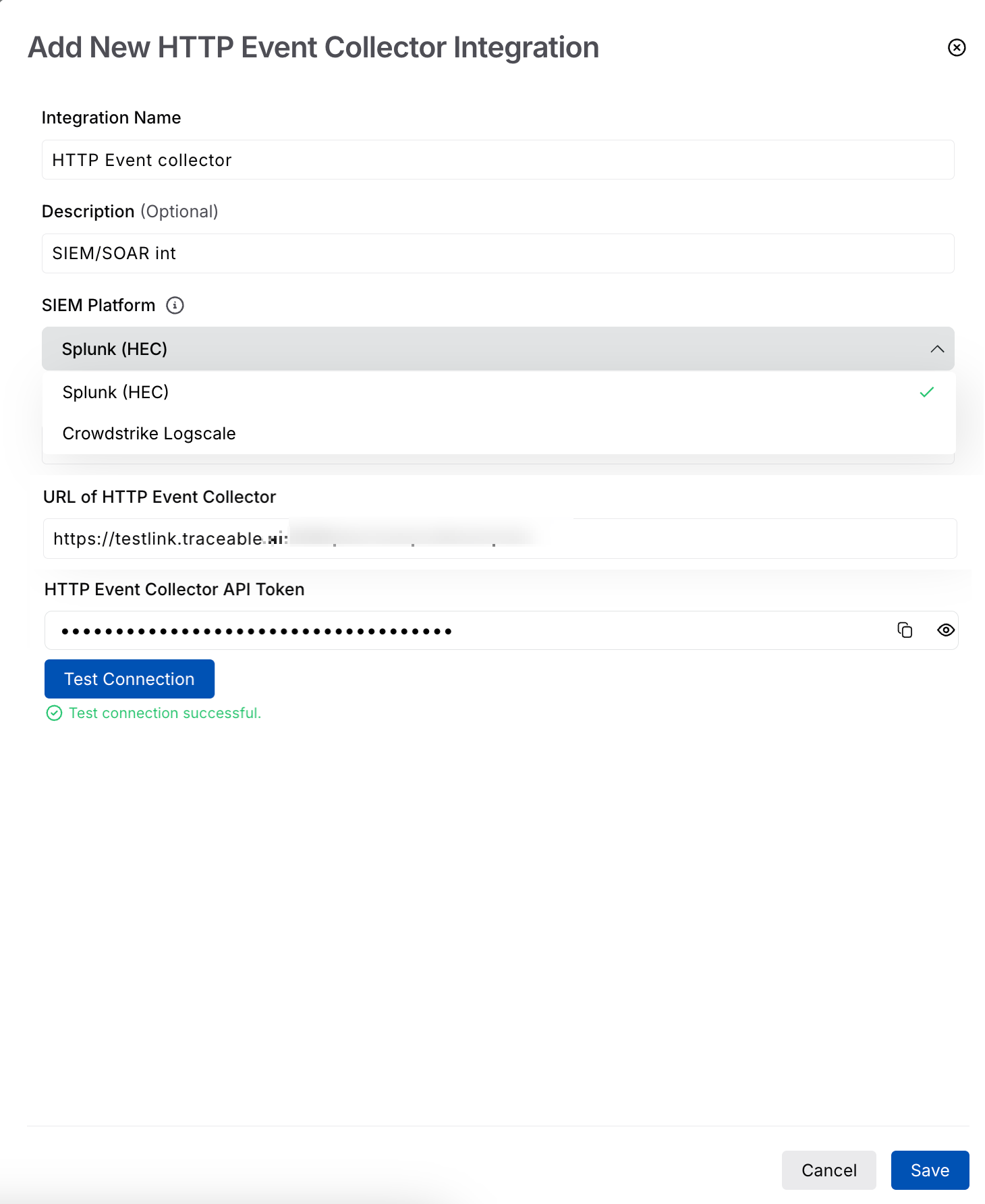
Add new HEC integration
In the Add New HTTP Event Collector Integration window, complete the following steps:
Specify the Integration Name, for example, HTTP Event Collector.
(Optional) Specify the Description, for example, SIEM/SOAR int.
Select either of the following from the SIEM platforms drop-down.
Specify the URL of the HTTP Event Collector fetched from the above chosen SIEM platform. For more information, see Before You Begin section.
Specify the HTTP Event Collector API Token fetched from the above chosen SIEM platform. For more information, see Before You Begin section.
Note
It is mandatory to provide a token while configuring this integration in Traceable.
Click Test Connection. Traceable validates the URL and the API Token. Once the validation succeeds, click Save.
Step 2 — Create a notification channel
You must create a notification channel to receive notifications when an event is triggered. To create a channel, log in to your Traceable account, navigate to Settings (![]() ) → Notifications → Create Channel, and complete the following steps:
) → Notifications → Create Channel, and complete the following steps:
.png)
Create Channel
Specify a name for the channel, for example, HEC_Channel.
Enable the HTTP Event Collector Webhook toggle. For more information, see Notifications.
Once you have enabled the toggle, click Save.
Step 3 — Set up a notification rule
Traceable sends a notification through the channel when an event matches the selected category and type. It allows you to be notified if any rule you create triggers an event. To set up the notification, log in to your Traceable account, navigate to Settings (![]() ) → Notifications → Create Notification, and complete the following steps:
) → Notifications → Create Notification, and complete the following steps:
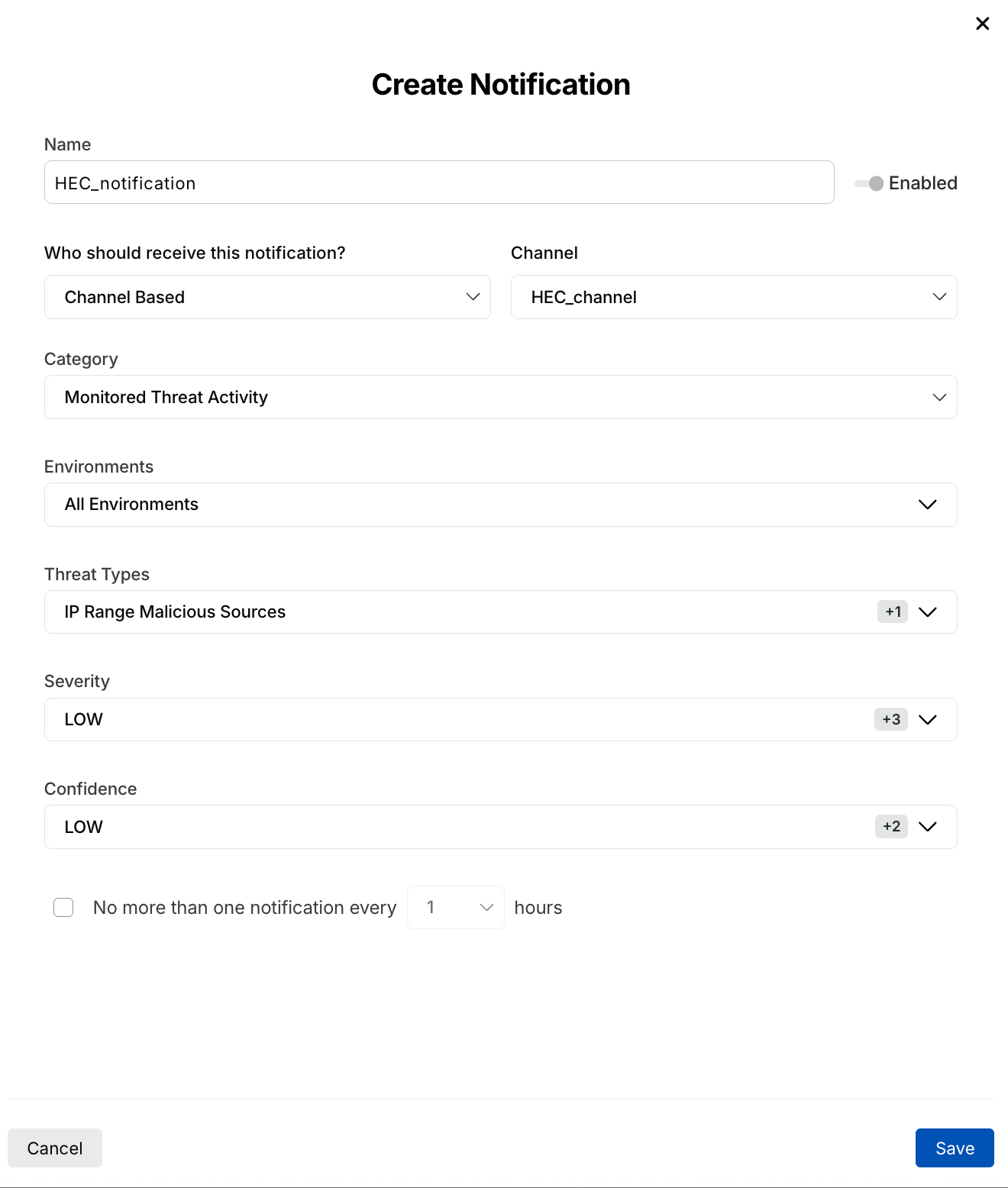
Create Notification
Specify a Name for your notification, for example, HEC_notif.
Select Who should receive this notification from the drop-down, for example, Channel Based.
Select the Channel that you created in Step 2 above, from the drop-down, for example, HEC_Channel.
Select the Category from the drop-down. For more information, see Notifications.
Select the Threat Types according to your requirements.
Select All Environments under Environments.
Click Save.
Once you have completed these steps, proceed to the demo for a hands-on interactive walkthrough of your HEC integration set up.
Demo and Example
The following interactive demo walks you through the steps to navigate, integrate the HTTP Event Collector (HEC) with Traceable, and create channel notifications.
After you configure the integration, Traceable monitors your application traffic and detects security events. When it identifies a threat, it generates a notification and sends the event data via the HTTP Event Collector (HEC).