Splunk SIEM works as a security intelligence hub, designed to give you full visibility into your organization's security posture. It goes beyond traditional security solutions by providing real-time monitoring, detection, and response to threats across your entire IT environment. Splunk SIEM helps in early detection, rapid response and collaboration which are needed to mitigate today's advanced threats.
The Splunk HTTP Event Collector (HEC) can be used to view alert notifications from Traceable in Splunk. Splunk HEC lets you send data and application events to a Splunk deployment over the HTTP and Secure HTTP (HTTPS) protocols. This helps consolidate alert notifications from Traceable into Splunk so that your operations team can review and act on the alerts. Traceable threat activity and events for different detections like Broken Object level Authorization, Broken Functional level Authorization, SQL Injection, Remote Code execution, and so on can be automatically sent to Splunk for further analysis.
Before you begin
Make a note of the following points before proceeding with integration:
- Make sure that you have the HTTP Event Collector (HEC) URL. For more information on HEC, see Set up and use HTTP Event Collector in Splunk Web.
- Make sure that you have a Splunk API token. For more information, see Create and manage organization access tokens.
Integration
To integrate Splunk SIEM with Traceable, login to your Traceable account and navigate to Integrations → SIEM/SOAR → Splunk. 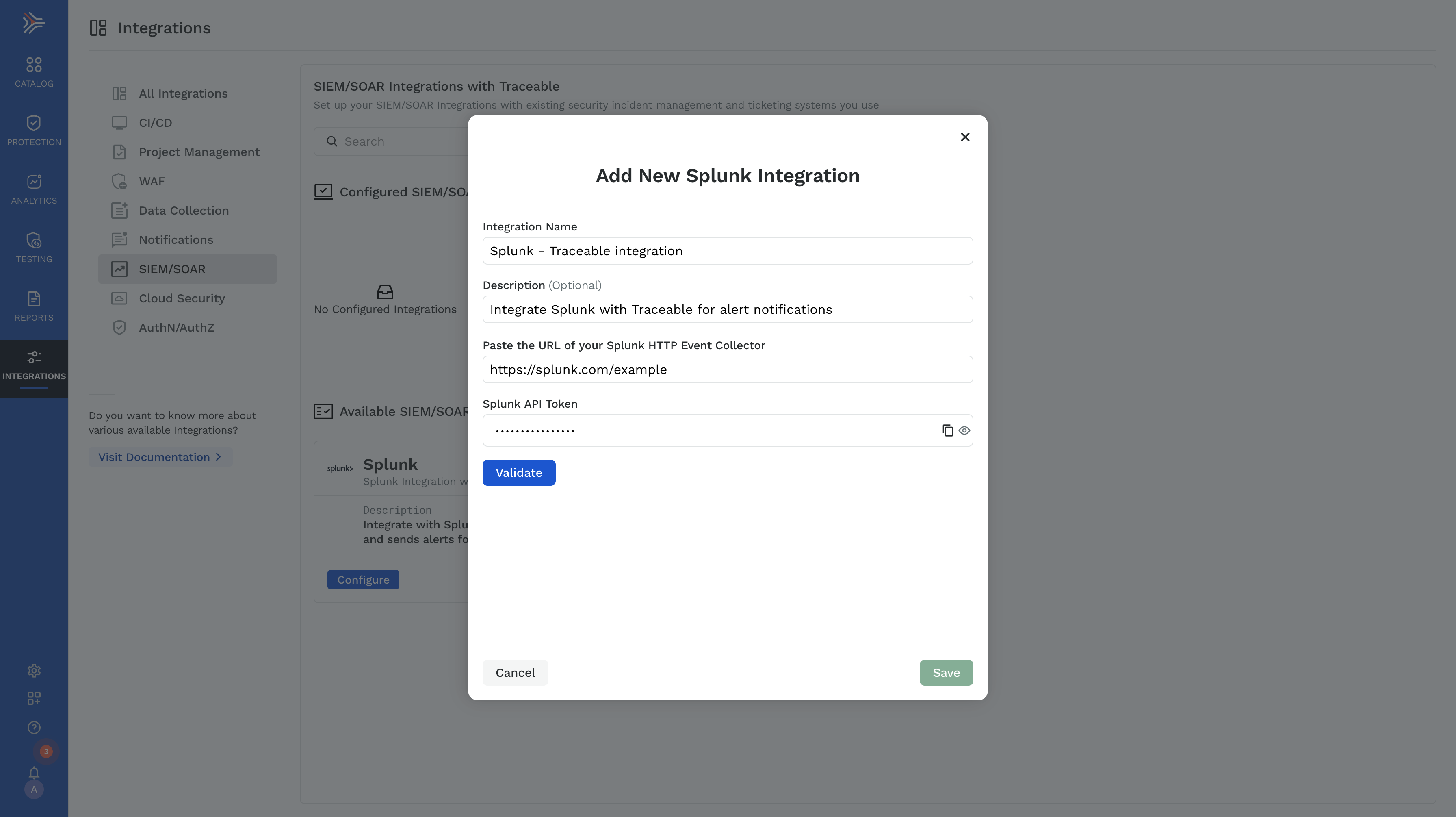
Provide the Splunk HTTP Event Collector URL and the Splunk API token. Traceable validates the URL and the API token. If the validation succeeds, the Save button is enabled.