GitHub Actions is an automation and workflow tool that GitHub provides. It allows developers to automate tasks and define workflows using YAML files. Workflows are triggered by events such as code pushes or pull requests and can include a series of actions. Actions are reusable tasks that can be combined to create workflows. GitHub Actions is commonly used for continuous integration/continuous deployment (CI/CD) pipelines.
Traceable integrates with GitHub Actions by running security scans in staging environments. Traceable helps you by finding vulnerabilities in the early stages of SDLC, giving developers and product security engineers more time and context to prioritize the mitigation of vulnerabilities and build secure APIs. The topic explains how to configure and use Traceable XAST CI/CD integration and how to run the scan during the build step.
Before you begin
Make a note of the following before integrating GitHub actions with Traceable:
Make sure that you have an active account and repository on GitHub.
It is helpful if you have a basic understanding of GitHub actions and workflows. For information, see GitHub actions documentation.
Integration
Integrating Traceable xAST with GitHub workflows using GitHub actions entails finding a GitHub action, understanding the inputs, outputs, and a sample GitHub action workflow.
GitHub action
All the GitHub actions by Traceable are currently available in GitHub repository. In addition, the Traceable AST actions are available in a YAML file at: https://github.com/Traceableai/ast-action/blob/main/action.yml
Understand the inputs
The following table explains the various inputs.
Input | Description |
|---|---|
| Scan action: init/ run/ init and run/stop. |
| The name of the scan. |
| Access the token from the Traceable Platform. You can fetch the access token by navigating to Your Account ( |
| The Traceable CLI version to be used. For more information, see Traceable CLI. |
| The environment for which AST should observe the traffic. |
| List of plugins you wish to run the AST scan for. |
| Include the URL patterns to test. |
| Exclude URL patterns from the scan. |
| Target URL for the tests. |
| URL for the Traceable server. This does not apply to SaaS users. |
| Timeout for a scan when it goes in the IDLE state. |
| Reference environment from where AST should pick up the API specifications. |
| Max retries for the scan after a failure. |
| The AST suite name as defined on the Traceable platform. |
| A comma-separated list of GraphQL schema IDs uploaded to the Traceable platform. |
| A comma-separated list of GraphQL SDL file paths. |
| Enables extracting the GraphQL schema by running introspection on the target URL. |
Sample GitHub actions workflow
The following is a sample workflow showing how to configure the AST GitHub action.
name: Test Traceable AST Init And Run Action With AST Scan Suite
on:
push:
branches:
- main
pull_request:
workflow_dispatch:
jobs:
InitAndRunAstScan:
runs-on: ubuntu-20.04
steps:
- name: Checkout
uses: actions/checkout@v3
- name: Init and run scan action
uses: Traceableai/ast-action@main
with:
step_name: 'init and run'
client_scan_token: ${{ secrets.CLIENT_SCAN_TOKEN_DEMO }}
cli_version: 'latest'
scan_suite: 'github-actions-test-suite'
traceable_server: ${{ secrets.TRACEABLE_SERVER_DEMO }}
- name: Stop Scan
if: always()
uses: Traceableai/ast-action@main
with:
step_name: 'stop'
client_scan_token: ${{ secrets.CLIENT_SCAN_TOKEN_DEMO }}
traceable_server: ${{ secrets.TRACEABLE_SERVER_DEMO }}
functionalTest:
runs-on: ubuntu-20.04
steps:
- name: Run a loop as functional test (This is sample)
run: |
for ((i=1;i<=100;i++));
do
echo $i
doneAs you can see in the above workflow:
A scan is initiated with the scan action steps that take the following parameters as input:
client_scan_tokenscan_suitetraceable_server
You can also configure additional parameters mentioned in the inputs table above. Alternatively, you can configure assets, attacks, evaluation criteria, etc., and create a scan suite on the Traceable platform. You can then initiate a scan by only using the suite name as the value in the
scan_suiteparameter above.Traceable executes functional tests and runs scans that take the the following parameters as input:
client_scan_tokentraffic_envcli_version
Triggers
GitHub workflow supports a wide range of triggers. You can read more about them at Events that trigger workflows.
Report
The following is a sample AST report once the scan is executed. The report shows various details about vulnerability categories, subcategories, and severity.
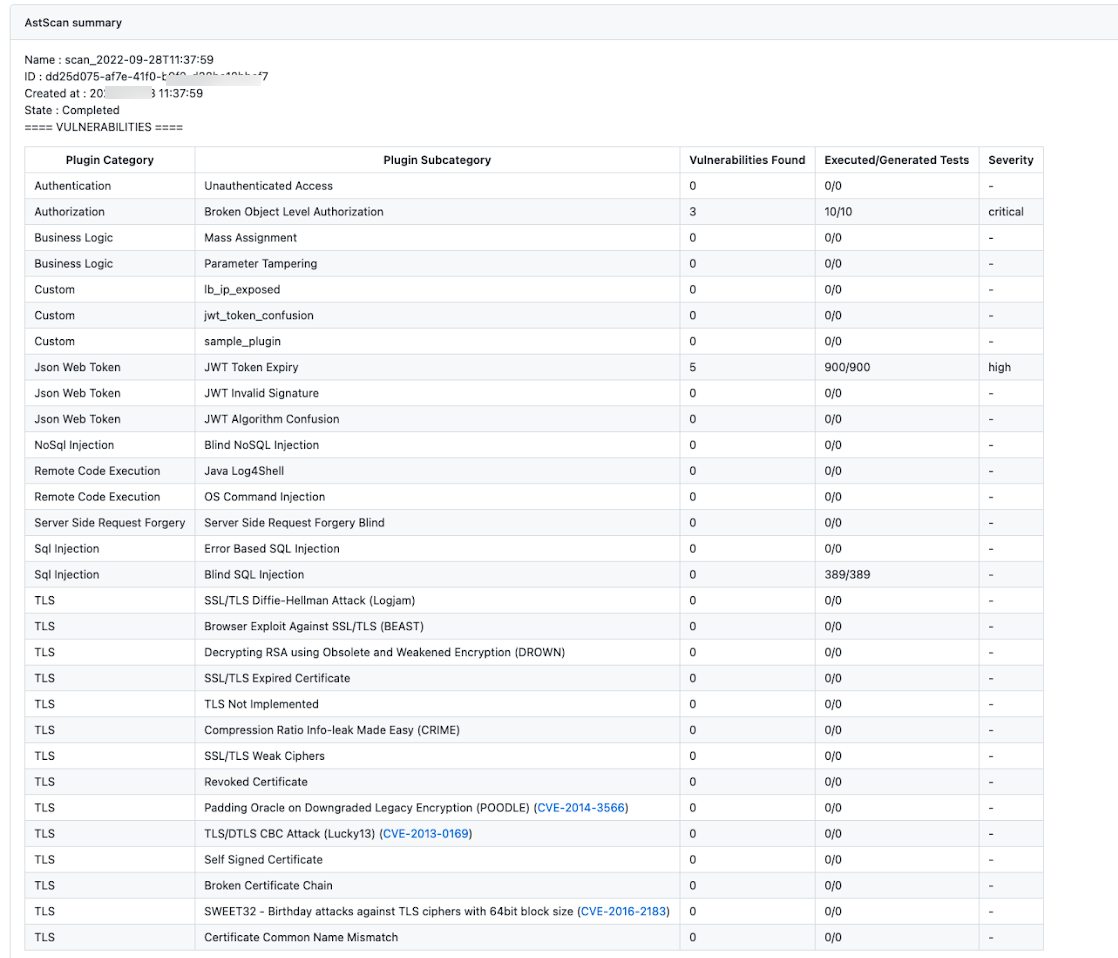
You can view the report from the summary section as shown below: