Traceable’s Bot Protection Rules allow you to detect, monitor, or block known automated bots that interact with your APIs and web applications. These rules are essential in mitigating risks posed by malicious crawlers, vulnerability scanners, DDoS bots, and various forms of non-human traffic that can disrupt or compromise your services.
What will you learn in this topic?
In this topic, you will learn how to:
Understand the role of known bots and how they are classified
Use the default bot protection rules to monitor common bot behaviors
Create custom bot protection rules tailored to your environments and endpoints
Modify policy actions and scopes
View bot detection and enforcement outcomes via Bot Events and Bot Activities
Understand current limitations and deployment support
What are Bot Protection Rules?
Bot Protection Rules are rule-based configurations that let you define how your system should respond to traffic generated by bots. These bots are grouped into known bots, curated and continuously updated by Traceable’s security team. Each policy defines a scope (environments and endpoints), target bot categories, and the action to be performed (Monitor, Block, or Allow).
You can use:
Default Rules are provided out of the box, initially disabled, and set to Monitor.
Custom Rules that you can create to tailor the scope and behavior to your specific environment or risk tolerance.
Understanding the Known Bots
Known bots are those Traceable has identified using their IP addresses, user agent signatures, and behavioral patterns. These bots are organized into categories and subcategories. Examples include:
Scanners (for instance, BurpSuite, Scrapy, Nessus)
Malicious Bots (for example, DDoS tools)
Marketing and SEO Bots
Automation Tools (for example, Puppeteer, PhantomJS)
Social Media and Content Bots
These categories are dynamic. New bots may be added as they are discovered.
Default Bot Protection Rules
Traceable offers a collection of default bot protection rules for each category and its corresponding subcategories. These rules are designed to provide users with a quick starting point for monitoring or controlling bot behavior.
Key characteristics of default rules:
They are pre-configured and provided by Traceable as part of the platform.
Each policy is initially disabled and set to Monitor mode by default, meaning no active enforcement is applied until it is enabled.
Users can enable or disable these rules at any time based on their requirements.
Rules allow changes to the action (Monitor, Block, or Allow), as well as adjustments to the environment and target endpoints.
The bot category and subcategory selections are fixed and cannot be modified in default rules.
You can find these rules in the Protection → Policies section under the Bot Protection tab.
Creating a Custom Bot Protection Rule
Custom rules provide greater control, allowing you to define how specific bots should be handled in specific environments or API endpoints.
Steps to create a custom rule:
Navigate to Protection → Policies → Bot Protection.
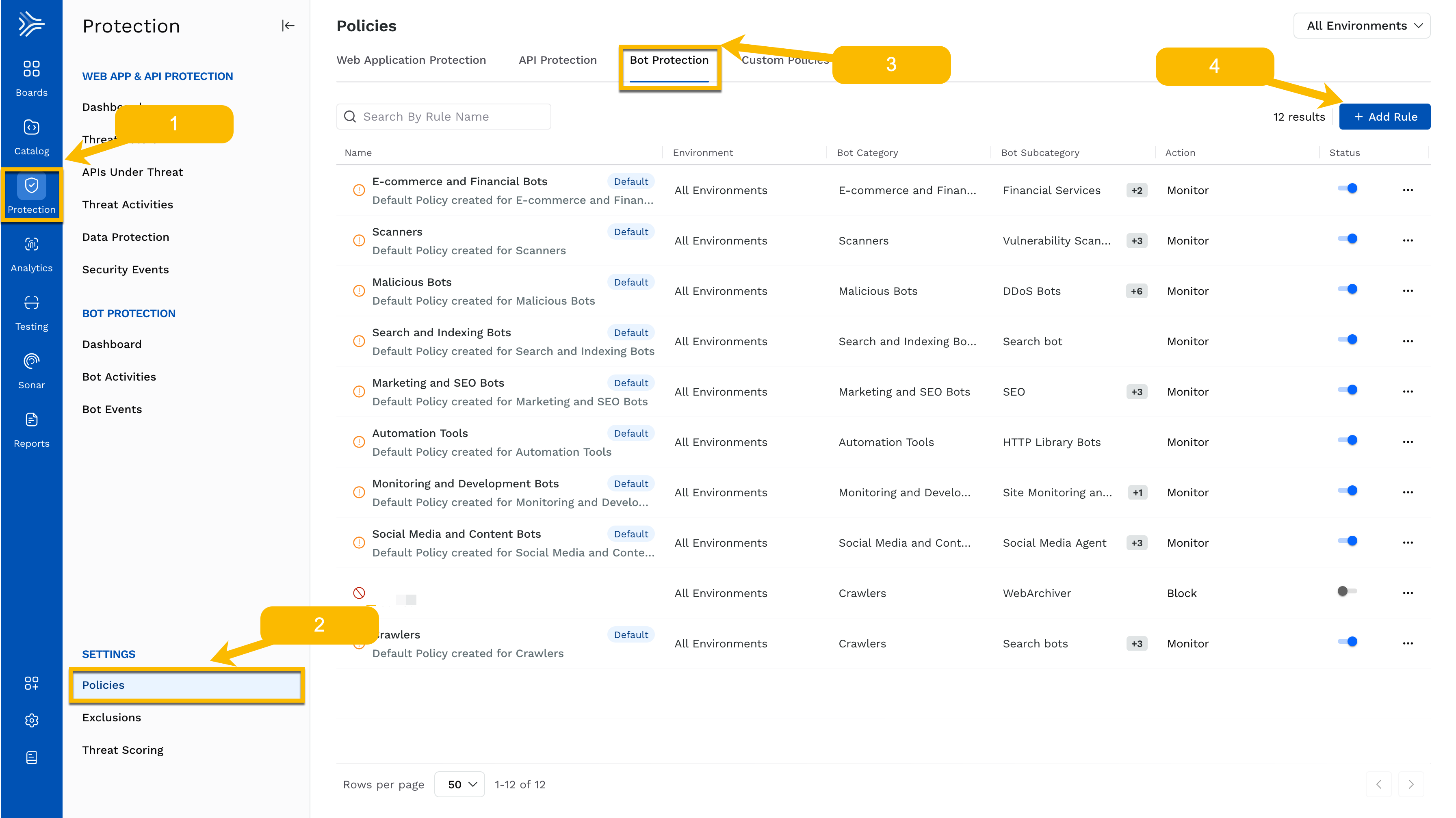
Click + Add Rule.
In the Create Bot Rule step:
Enter a name for the rule and an optional description.
Select the environment(s) where this rule will apply.
Select one or more bot categories and their corresponding subcategories. You can select full categories or drill down to specific tools or behaviors (for example, just Googlebot under Crawlers).
Select whether the rule applies to all endpoints or specific endpoints.
Click Next to proceed to the Actions step.
Choose one of the following actions:
Monitor: Log the bot activity without intervening.
Block: Prevent the bot traffic from reaching your services.
Allow: Explicitly allow traffic from these bots.
Click Next to review your selections.
Click Submit to create and activate the rule.
Once created, custom rules appear in the Bot Protection policy table alongside default rules. You can edit or delete them at any time.
Note
Cloning existing rules is not supported.
How Policy Actions Are Applied
After a policy is created, whether it is a default or custom policy, the configured action begins to take effect based on the rule's settings. These actions govern how Traceable handles bot traffic that matches the selected categories and scope.
Enabling a policy activates the associated action across the selected environment and endpoints.
Blocking actions may take a few minutes to propagate through backend systems before enforcement begins.
You can toggle a rule on or off to quickly disable or re-enable enforcement across the selected environment and endpoints.
Blocking actions may take a few minutes to propagate through the backend systems.
Viewing Bot Activity and Enforcement Events
Bot Protection rules are tightly integrated with Traceable’s Bot Activities and Bot Events views.
Bot Activities shows behavioral summaries of bot traffic across your APIs.
Bot Events presents granular, per-request details including:
Matched rule name
Bot category and subcategory
Action taken (Monitor, Block, Allow)
Encoded metadata about the decision
Access to trace and span-level data for forensic analysis
You can filter bot events by threat type, such as “Social Media Agent” or “Vulnerability Scanner,” and drill down into the associated spans.
Recommendations and Considerations
Default rules are a good starting point. You can enable them selectively and modify their actions or scope as needed.
Custom rules are recommended for targeted blocking or monitoring, especially when different environments need distinct handling.
You cannot modify the categories or subcategories in the default rules. If needed, create a custom rule with the desired selection.
Cloning existing rules is not supported.