After a scan execution is complete, the Scan Details page highlights key information about the scan. It provides comprehensive information on the identified issues, the APIs covered (tested), the list of scan runs performed, and the specific tests executed during each scan run.
Understanding and Leveraging
What will you Learn in this Topic?
By the end of this topic, you will understand:
The details shown for each scan
How can you leverage the details in each tab to analyze the test results and customize security testing
Understanding and Leveraging Scan Details
The following tabs outline the key details displayed in each scan tab and explain how you can utilize the data to tailor and analyze tests according to your requirements.
The Issues tab details the vulnerabilities Traceable identified as part of the scan. It lists the Open or Reopened issues grouped by name and key details like severity and last seen time. You can use this tab to analyze the issues and prioritize remediation according to your requirements. For more information on issues, the key components visible on the page, and how you can drill down into each issue and leverage it, see Issues Overview and Management, respectively.
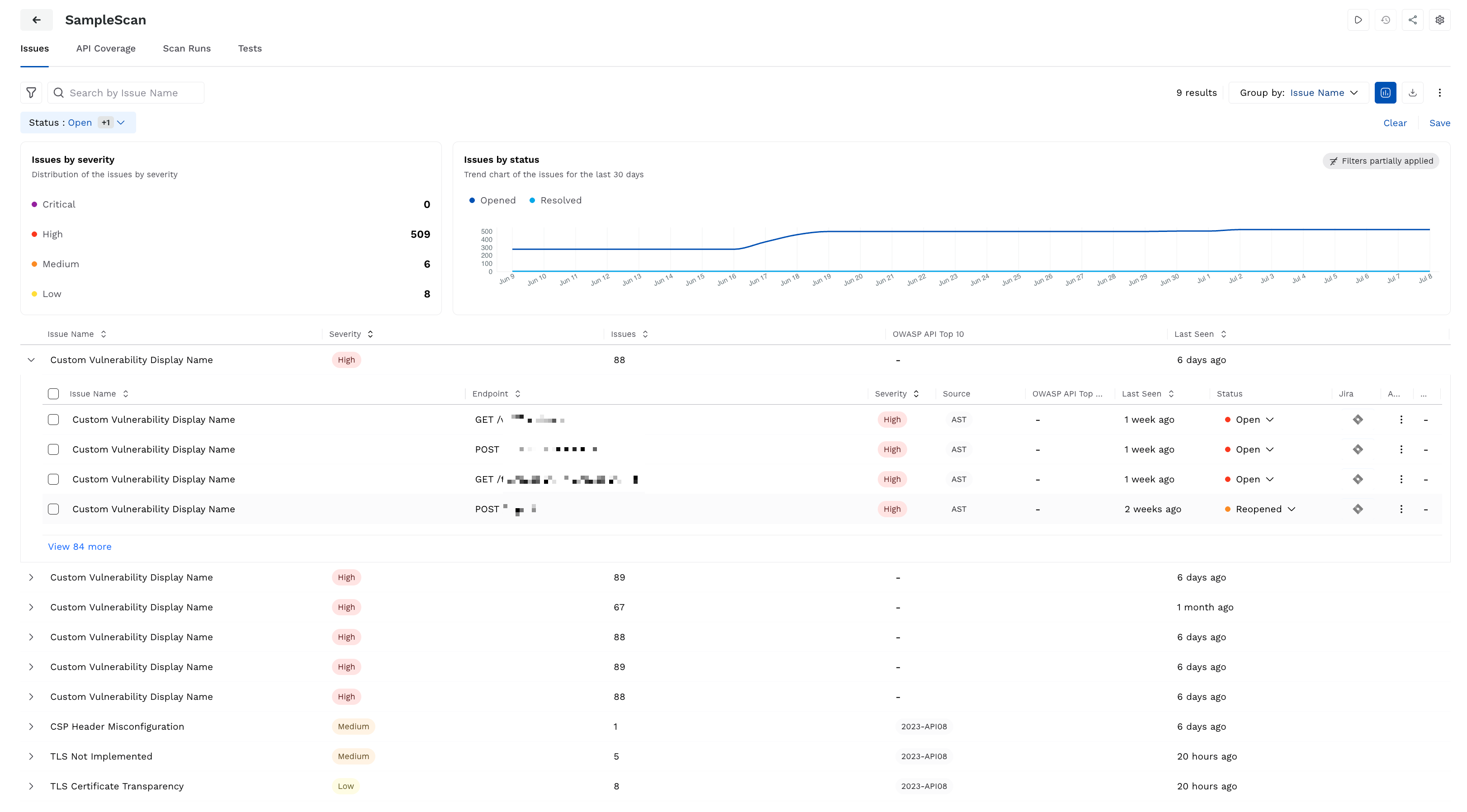
Issues in a Scan
When you drill down into an issue, Traceable shows the evidence corresponding to it. This evidence contains key details such as the Assertions and Mutations that Traceable used to detect the issue. You can customize the vulnerability (issue) detection by modifying these assertions and mutations and/or adding new ones from their respective tabs, according to your requirements. For more information, see Mutation and Assertion Overrides.
Auto-Resolution of Issues
Traceable, by default, auto-resolves issues in the following scenarios:
Time-based scenario — An issue has not been detected in any of the scans for 60 days since its last occurrence.
Scan-based scenario — An issue has not been detected in 15 consecutive scans since its last observation.
While the above are default thresholds, you can contact Traceable Support to modify them according to your requirements.
Example: How auto resolution works
Consider an API endpoint that is being scanned for the Weak JWT Algorithm attack:
The endpoint has been scanned five times, and the most recent scan detected the issue (vulnerability).
Time-based scenario — This condition is not satisfied, as the issue was just detected, which resets the 60-day timer. The countdown starts only after the most recent detection date.
Scan-based scenario — This condition is not satisfied, as it requires 15 consecutive scans without detection of the issue (vulnerability). As the most recent scan detected the issue, the scan-based counter is reset to zero.
Traceable resolves the issue automatically if:
15 consecutive scans do not detect the issue.
60 days pass without the issue being detected.
The API Coverage tab provides details on how and which API endpoints Traceable exercised or covered during a scan. This helps you understand which endpoints were tested, the thoroughness of testing, and whether any vulnerabilities were identified. This view helps you understand and validate the effectiveness and API reachability based on the scan configurations.
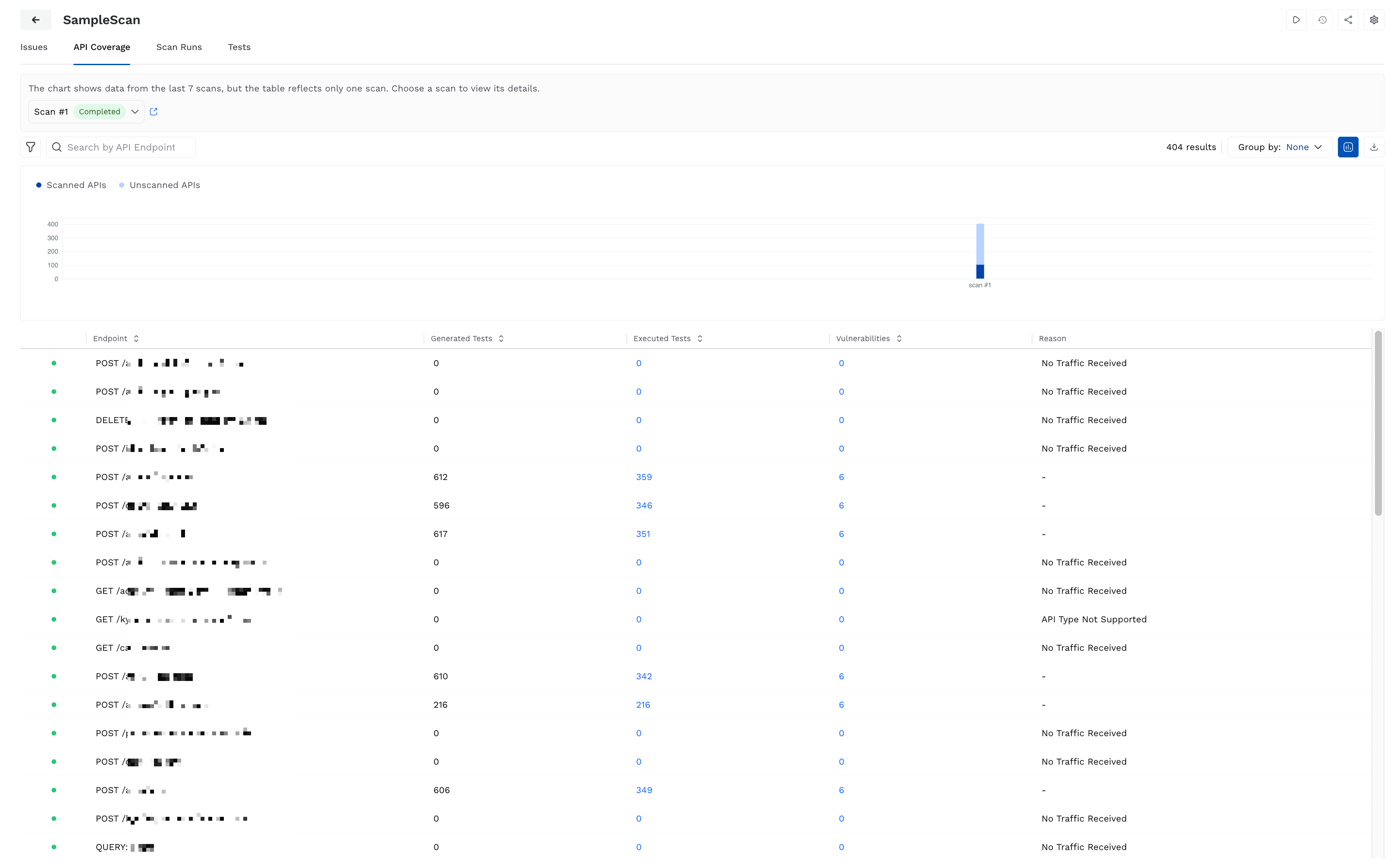
API Coverage in Scans
Understanding the API Coverage Tab
The top of the tab shows API coverage (scanned and unscanned APIs) over the past seven scans. You can use this chart to track scanning consistency and validate the scan progress. Below the chart, Traceable shows a table with the following details:
Status — The scan indicator indicates whether the API is reachable (green dot) or not (red dot).
Endpoint — The API endpoint name scanned as part of the scan run.
Generated Tests — The number of tests generated for scanning the endpoint.
Executed Tests — The number of tests executed from the number of generated tests for the endpoint.
Vulnerabilities — The number of issues (vulnerabilities) identified on the endpoint.
Reason — Specifies the reason if no tests were executed on the endpoint, for example, No Traffic Received.
The details shown in the above table are for the latest scan by default. From the top of the tab, you can select the scan for which you wish to view the API coverage details. Traceable populates the table in the tab based on the scan you select.
Traceable also provides the following features in the tab:
Search bar — Locate an endpoint by typing its name.
Filter icon — Refine the data shown in the tab by API name, reachability, existence of vulnerabilities, and/or scanning of APIs. Post-application, you can also save the filter for later use. The saved filters are visible under Filter → Saved tab.
Group By drop-down — Group the data shown in the tab by Reachability, Reason for Skipping, or view it ungrouped (None).
Visualization toggle — Show or hide the chart highlighting API coverage over the past 7 scans.
Download icon — Download the list of APIs covered for offline analysis.
Leveraging Data Shown in the Tab
Consider a scenario where you have set up a scan that targets critical APIs in the HighTechApp environment. After a few scans have completed, you come to the API Coverage tab to validate the effectiveness of scan configurations.
You identify endpoints like POST /login and GET /transactions/get have a high number of generated and executed tests and the number of issues that may have been identified. This highlights the effectiveness of the scan configurations. However, at the same time, you identify that endpoints like POST /users and POST /card/unblock have 0 Generated and Executed Tests, and No Traffic Received as the reason. This highlights the following:
The APIs were inactive during the scan.
The APIs did not have any traffic corresponding to the traffic type you configured during scan creation.
In these scenarios, you can do the following:
Modify the traffic type for the scan based on where traffic is available for Traceable to scan the endpoint.
Verify if the endpoints are still in use in your application ecosystem.
Similarly, there can be scenarios where the number of executed tests is greater than 0, and the number of issues (vulnerabilities) identified is 0. In such scenarios, if you think the API coverage is lower than expected, you can do the following:
Validate and/or change the traffic type to represent real-world usage.
Modify the policy (attack sets) that you want Traceable to use for testing the endpoints.
Verify if the authentications defined, if any, are blocking Traceable from scanning the endpoints thoroughly.
The Scan Runs tab provides a list of all scan executions for the scan configuration in reverse chronological order, with the latest scan run at the top. Each row in the tab represents an individual scan execution and helps you track scan performance and behavior over time.
.png)
Scan Runs
Understanding the Scan Runs Tab
The tab shows a table with the following details:
Status — Indicates whether the scan was completed successfully or was aborted.
Scan Run — Indicates a scan execution in reverse sequential order.
Duration — The time taken for scan completion.
Tests Generated — The number of tests generated for scanning the endpoints.
Tests Executed — The number of tests executed from the number of tests generated for the endpoints.
Scanned APIs — The number of endpoints scanned during the scan run.
Vulnerabilities — The number of issues (vulnerabilities) identified in the scan run.
Start Time — The timestamp to indicate when the scan began.
The above details help you understand the scan consistency and detect anomalies such as aborted scan runs and inconsistent test counts.
Traceable also provides the following features in the tab:
Filter icon — Refine the data shown in the tab by scan Status, vulnerability Severities detected in the scan, and/or Vulnerable APIs. Post-application, you can also save the filter for later use. The saved filters are visible under the Filter → Saved tab.
Group By drop-down — Group the data shown in the tab by Status, or view it ungrouped (None).
Download icon — Download the list of scan runs for offline analysis.
Leveraging Data Shown in the Tab
Consider a scenario where you created a scan that runs once daily. You can use the Scan Runs tab to compare scan executions and scan statuses over time.
Let us say that Scan #7 generated the highest number of tests and executed successfully. This indicates a comprehensive API coverage and scan execution. However, Scan #3 got aborted midway, executed only 100 tests, and scanned only 3 APIs. This may have been caused due to multiple reasons, such as environmental error or authentication failure. In this scenario, you can analyze the issues and set up alerts so that the scan does not get aborted mid-way.
Consistent values across the Tests Executed and Scanned APIs columns help you confirm scan stability, while the reduced count of vulnerabilities helps you validate security measures that you may have taken.
Any sudden drop or spike in either of the above values may indicate a change, such as API reachability, availability, to configuration issues. The Scan Runs tab acts like an audit trail, helps you analyze any change, and:
Identify and troubleshoot aborted scans.
Validate whether newly added APIs are being tested in the scans.
Confirm whether the identified issues are increasing or decreasing.
Modify scan configurations according to your requirements.
The Tests tab provides granular information on all the tests executed during a scan run. While Traceable selects the latest scan run by default, you can change it according to your requirements using the drop-down at the top. This tab helps you navigate how Traceable executed tests on each endpoint, if the response code was as expected, and if any issues (vulnerabilities) were identified.
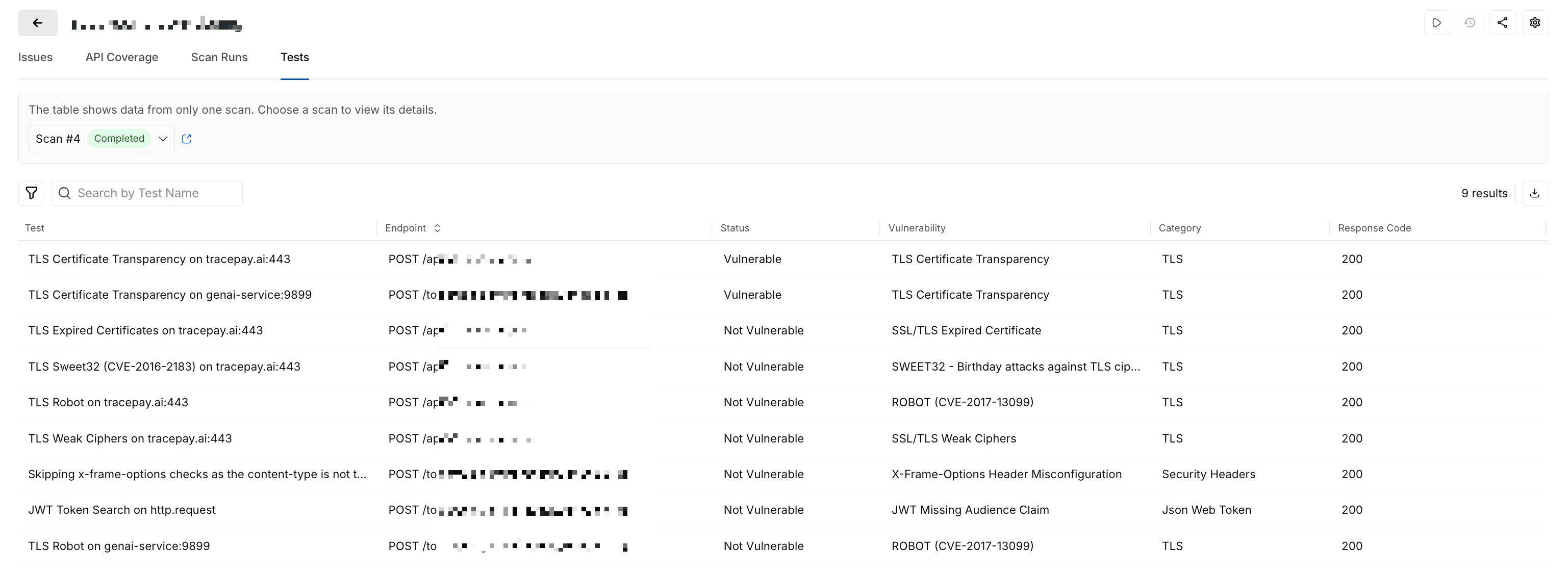
Tests for a Scan Run
Understanding the Tests Tab
The tab shows data for the latest scan run and includes the following details:
Test — The name or type of test executed as part of the scan.
Endpoint — The API on which the test was executed.
Status — The result of the above test from either of the following:
Vulnerable — The test detected an issue in the endpoint.
Not Vulnerable — The test did not detect any issue in the endpoint.
Error — The test was not completed. You can hover over the status for additional details on the occurred error.
Vulnerability — The vulnerability type for which the test was executed.
Category — The category to which the above vulnerability type belongs.
Response Code — The status code returned by the API endpoint post-test execution.
The above details help you understand and correlate tests in endpoint behavior and evaluate vulnerability detection.
Traceable also provides the following features in the tab:
Search bar — Type and locate any of the above details.
Filter icon — Refine the data shown in the tab based on various metrics. Post-application, you can also save the filter for later use. The saved filters are visible under Filter → Saved tab.
Download icon — Download the list of tests associated with a scan for offline analysis.
Leveraging Data Shown in the Tab
Consider that you ran a scan and navigated to the Tests tab to validate the executions. Upon navigating, you notice that several tests corresponding to the POST /login endpoint have the Status as Error. Hovering over the status shows that the connection timed out while executing the test on the endpoint. This indicates that the endpoint may have been unresponsive during the scan execution or may have a misconfiguration. You can use this information to analyze the availability and configuration of endpoints, ensuring that scans are executed without errors.
Clicking a test opens its detailed view that highlights the following information:
Test Details — Lists information, such as the tested endpoint, the status code returned by the endpoint, and the Trace ID associated with the test. You can also view the traces associated with the endpoint and copy the test as a cURL command. These options help you analyze and debug the endpoints in case of any issues. Once you have made the changes, you can run the test again.
Note
Traceable does not capture Traces for a test in the following scenarios:
When the Test Status indicates an Error (The APIs are not reachable).
When the Category of the identified vulnerability is TLS.
When the Attack Methodology Type for a plugin is Passive.
Assertions — Lists the validations Traceable has executed to identify the vulnerabilities. The Result column in this tab indicates whether the Assertion result was determined as vulnerable or not. You can use this information to analyze the validations and add new assertions or modify the existing ones according to your requirements. For more information, see Mutation and Assertion Overrides.
Mutations — Lists the modifications Traceable has made to the original request to test the endpoint. You can use this information to analyze the modifications Traceable makes and add custom mutations or modify existing ones according to your requirements. For more information, see Mutation and Assertion Overrides.
Request and Response — Details the HTTP headers, cookies, and body of the API request and the corresponding response. You can use this data to debug and confirm whether or not sensitive data is being exposed through the API.
You can use the data shown in the Tests tab and do the following:
Verify the detected issues (vulnerabilities).
Analyze the executed tests, how Traceable executed them, and the reason for failure.
Enhance the testing logic by modifying the tests according to your requirements.