Updates (October 2025 to December 2025)
December 2025 — Updated the topic to add information about the different methods to assign API ownership. For more information, see Different ways to assign ownership.
Traceable provides you with an option to assign API owners for every discovered API endpoint, helping you clearly identify the person or team responsible for developing, maintaining, and updating it. It brings accountability and clarity across engineering, security, and operations teams. For example, when a security analyst identifies an issue or policy violation in an API, ownership information makes it easy to raise a Jira ticket and route it to the correct team without delays or manual investigation. This reduces the mean time to remediation and ensures issues are addressed by the right stakeholders.
Beyond incident response, API ownership also supports better governance and collaboration. Product teams can quickly understand who owns a critical API, platform teams can coordinate changes during releases, and security teams can align risk findings with responsible owners. Traceable allows you to associate one or more owners with an API, reflecting real-world shared responsibility across teams and regions, and keeping ownership aligned with how APIs are actually built and managed.
What will you learn in this topic?
By the end of this topic, you will be able to understand:
Before you begin
Make a note of the following before you proceed:
Ensure that you have Edit access permission for the RBAC role for Discovery to assign API ownership. For more information on RBAC, see Teams and roles.
Different ways to assign ownership
Traceable allows you to assign ownership in the following ways:
Manually Assigning Ownership
Assignment using GraphQL
Dynamic Assignment
You can assign and/or edit the API ownership access using the Traceable platform. To assign or edit the ownership of an API endpoint, navigate to Discovery → Inventory → API Endpoints. In the details section of the Endpoint Details page, click the edit ( .png) ) icon corresponding to the API Ownership.
) icon corresponding to the API Ownership.
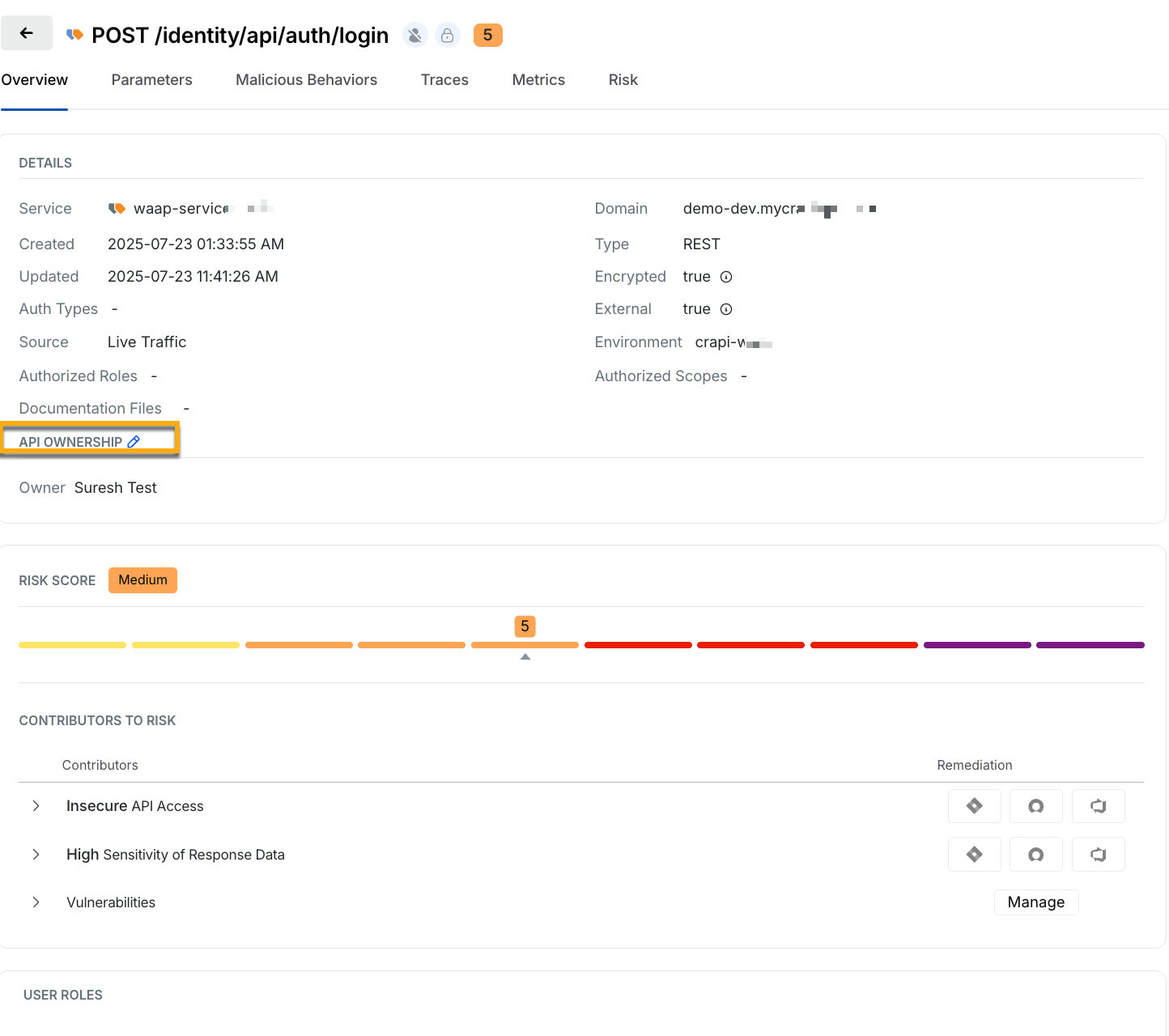
Assigning Ownership
In the Edit API Ownership window, provide the following details and save:
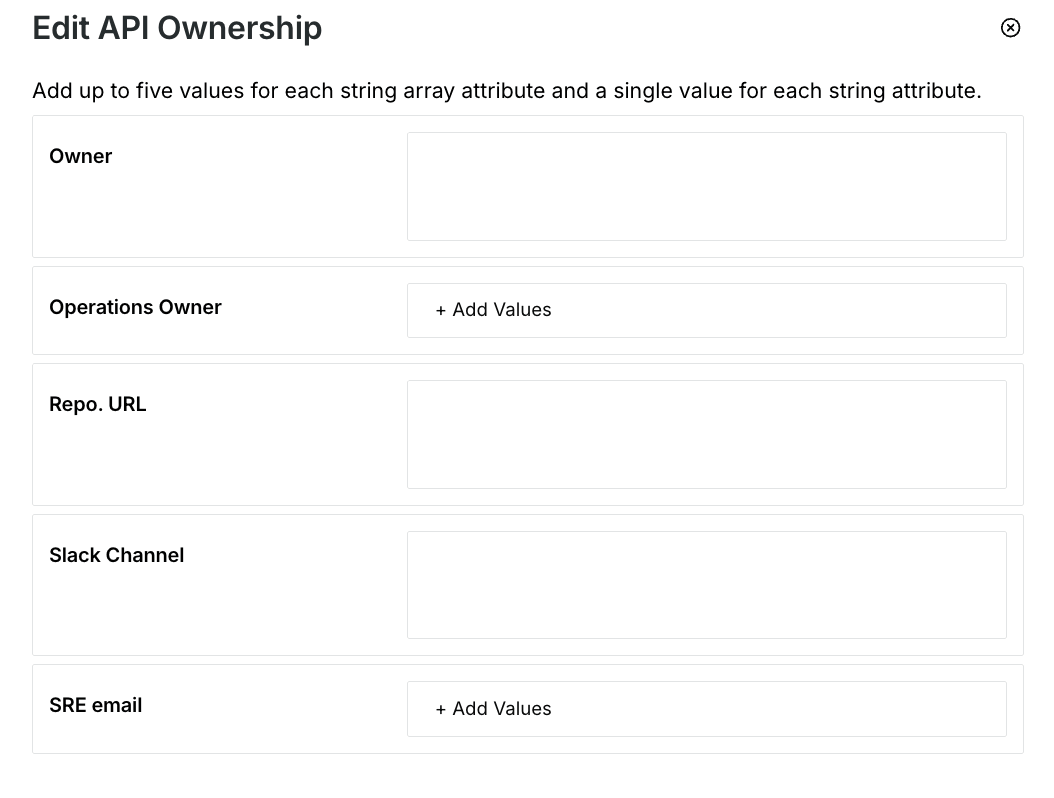
Edit API Ownership window
Owner — Specify the name of the person whom you wish to assign as the owner of the endpoint.
While the above attribute is available by default, you can also create up to five custom attributes according to your requirements. For more information, see Create an owner attribute. For example, in the screenshot above, the following are custom attributes:
SRE Email — Specify the email address to communicate any issues related to the API endpoint.
Repo URL — Specify the repository URL associated with the particular endpoint.
Slack Channel — Specify the Slack channel to which you wish to send notifications.
Note
You can add a maximum of five values for each attribute that takes string array or multiple string values.
You can add a single value for each attribute that takes a string value.
Dynamic API Ownership Assignment in Traceable addresses scalability challenges by automatically mapping API ownership based on spans observed in live traffic. You can use GraphQL to dynamically assign ownership information to APIs. For more information, see Dynamic API Ownership.
Traceable enables you to manage API ownership programmatically using GraphQL, allowing you to create attributes, assign owners, and update ownership across APIs efficiently. Assigning an owner to the API requires using Traceable's GraphQL APIs. You can configure ownership for an individual API or for all APIs in a service. To assign the API ownership, complete the following steps:
Identify the API or service ID
Assign the API ownership
Verify that the ownership is assigned
Before you assign the ownership, you should complete the following steps:
Step 1 — Identify API ID and Service ID
To assign ownership to an API, you need to fetch the API ID. Navigate to Discovery → Inventory → API Endpoints. Click the endpoint you wish to use to assign to the API. Copy the API ID from the URL.
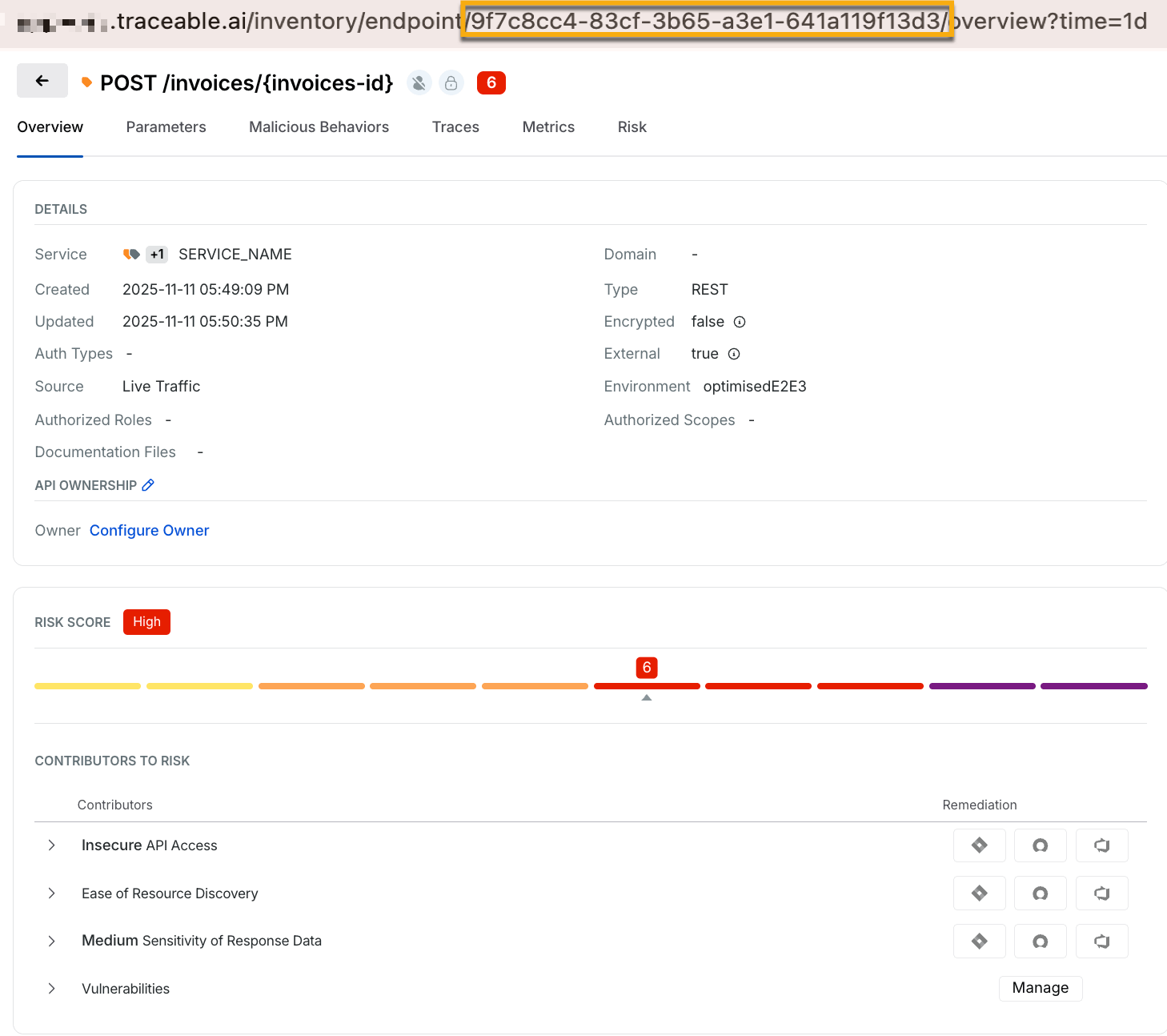
API ID from API Endpoint
Similarly, you can also fetch the service ID. Navigate to Discovery → Inventory → Services. Click the service name that you wish to use to assign ownership to APIs. Copy the service ID from the URL.
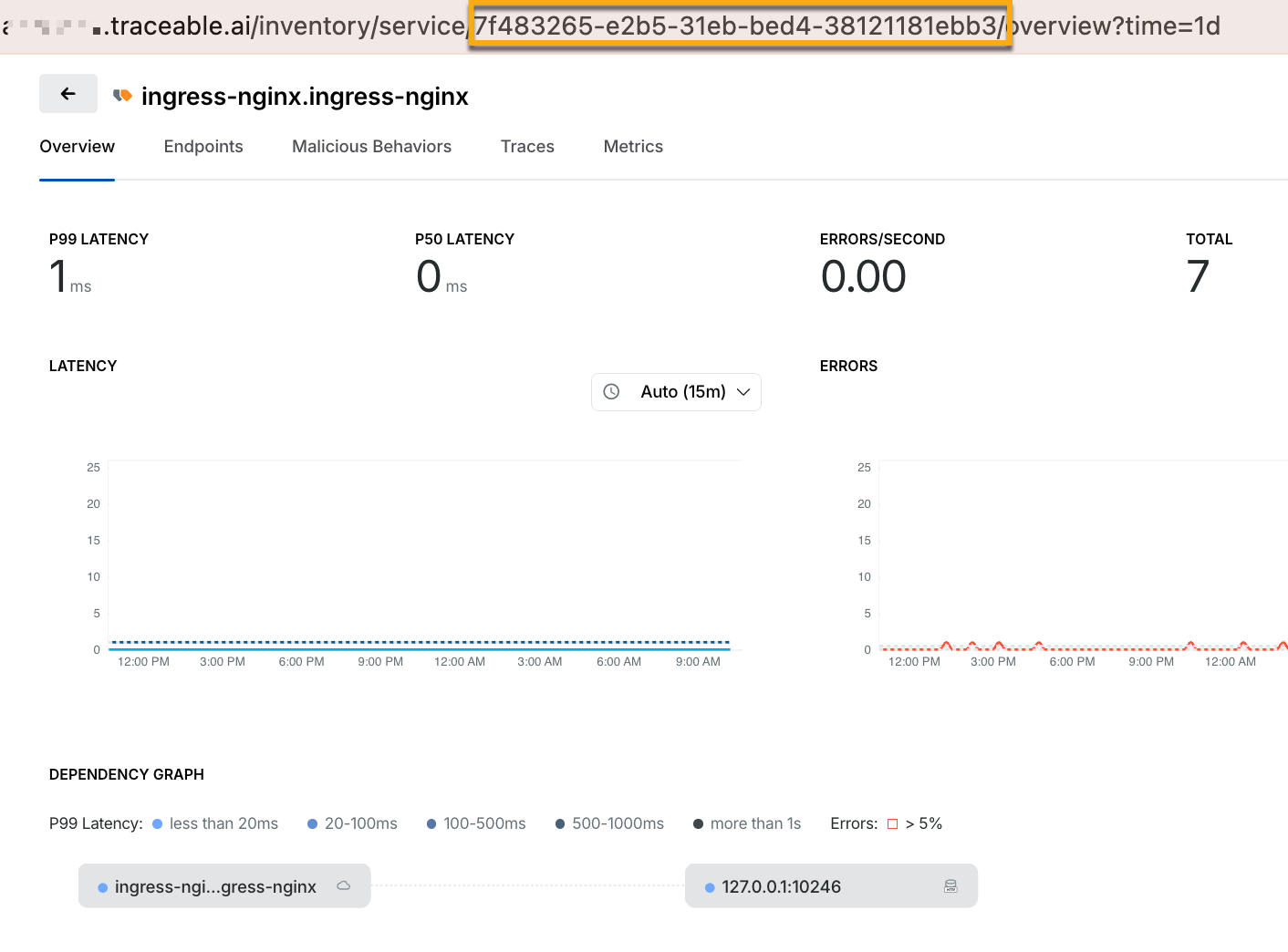
Service ID from Services
Step 2 — Assign Ownership
You can use the API ID in the following GraphQL query to assign ownership to the API:
mutation Set_owner_using_API_ids {
bulkUpdateEntities(
input: {
filterType: ID
IDs: [
"<0683697d-1a5e-37a4-8b73-951027f6d7fe>"
"<1dfd01bc-9c4f-34e6-8f33-ca7ffb61b7cb>" // Replace the placeholder IDs with the actual values
]
operation: {
operationType: SINGLE_VALUED_ATTRIBUTE_SET_OPERATION
singleValuedAttributeSetOperation: {
key: "dev-ops-owner"
value: "abc@mycompany.com"
}
}
type: "API"
}
) {
updatedCount
}
}In the above example:
Two sample APIs are assigned to the
keydev-ops-owner, with the attribute display name set to dev-ops-owner from Step 1 above.The email ID abc@mycompany.com is assigned to the attribute. This means that abc@mycompany.com is the owner of the two APIs.
Step 3 — Verify that ownership was assigned
To verify that the ownership was assigned correctly, navigate to Discovery → Inventory → API Endpoints. You can then filter the API Endpoints based on the owner value that you assigned in Step 2 above.
Once you have created the owner attribute and assigned API ownership, you can filter the API Endpoints based on the attribute. The following screenshot shows the results filter based on an ownership attribute.
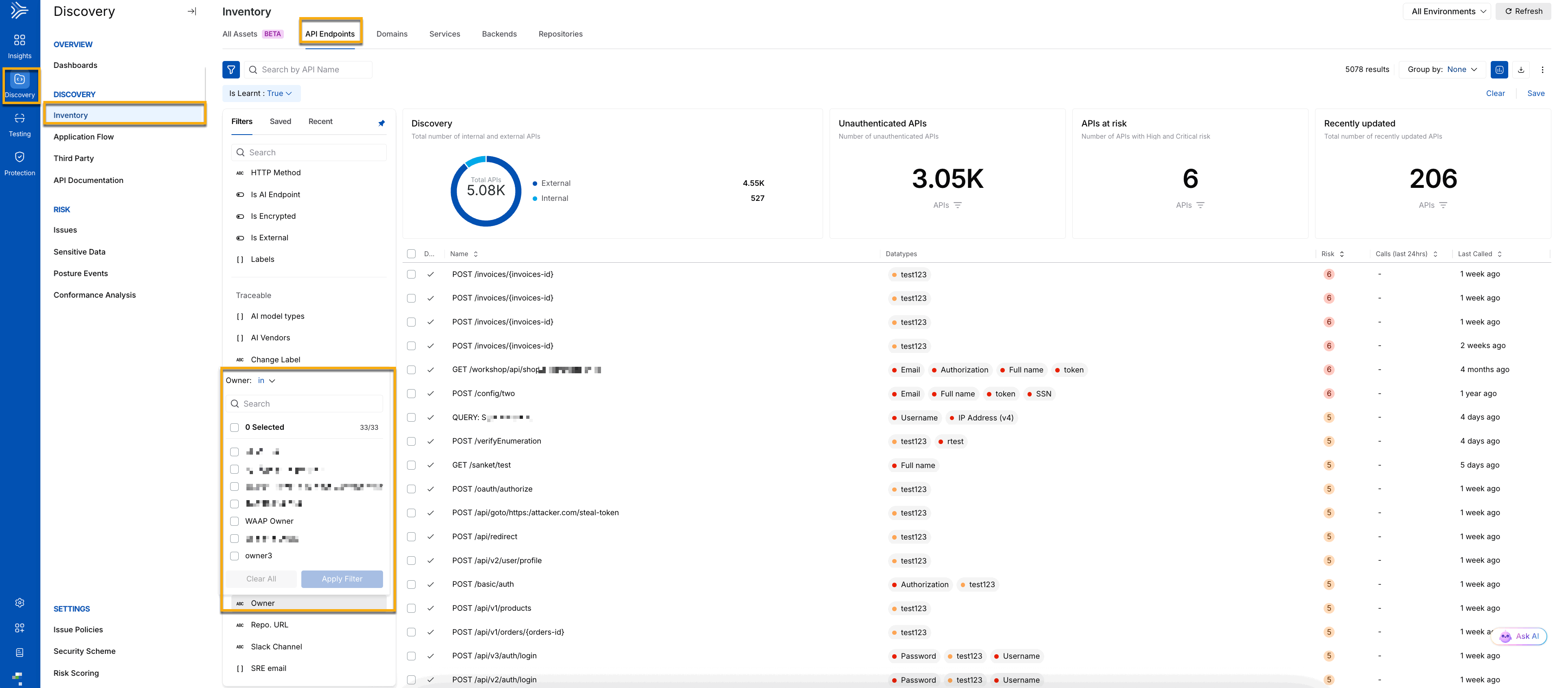
API Ownership
Miscellaneous API ownership operations
This section describes the miscellaneous API ownership operations you can perform using Traceable’s GraphQL APIs, including creating owner attributes, assigning or removing ownership at scale, and managing single-valued and multi-valued owner attributes.
Create an owner attribute
To create an owner attribute, use Traceable's GraphQL API. For more information on setting up a client and using Traceable's API, see Public APIs.
Note
Make sure that you have the Edit access permission for the RBAC role for Discovery to create a new owner attribute. For more information, see Teams and roles.
You can skip this step if you wish to use the Owner attribute as your default.
You can use the following GraphQL query to create an owner attribute:
mutation CreateAttribute {
createAttribute(
attributeMetadataInput: {
displayName: "DevOps Owner"
identifier: { key: "dev-ops-owner", scope: "API" }
type: STRING_ARRAY
}
) {
displayName
name
scope
type
}
}The
displayNameis the name that you wish to assign to the attribute. In the above example, an attribute named DevOps Owner is created.You can use
STRINGinstead ofSTRING_ARRAYif you wish to create a single-value attribute. For example, in the above snippet,STRING_ARRAYis used. Using this, you can assign multiple values.
Once you have created the ownership attribute, wait a few minutes for the change to take effect in the Traceable platform. A minimum interval of five minutes is recommended before proceeding to the next step. Navigate to Discovery → Inventory → API Endpoints to view the attribute.
Assign ownership of all API Endpoints under a service
You can assign ownership of all API endpoints under a particular service.
Note
Make sure that you have the Edit access permission for the RBAC role for Discovery to execute this.
You can use the following GraphQL query to assign ownership to APIs under a service. You can fetch the service ID as elaborated in Step 1 of manually assigning ownership section.
mutation Set_owner_using_service_id {
bulkUpdateEntities(
input: {
filterType: ATTRIBUTE
filters: {
key: "ServiceID"
operator: EQUALS
value: "<6dfd8560-4767-38f4-9cd1-6769be68929e>" // Replace the placeholder value with the actual service ID
}
operation: {
operationType: SINGLE_VALUED_ATTRIBUTE_SET_OPERATION
singleValuedAttributeSetOperation: {
key: "owner"
value: "bob@mycompany.com"
}
}
type: "API"
}
) {
updatedCount
}
}In the above example:
All APIs under Service ID are assigned to the owner attribute with the value bob@mycompany.com. This means that all the APIs under the mentioned Service ID would have bob@mycompany.com as the owner.
Note
When you assign ownership to APIs under a service, and if new APIs are added to the same service in the future, ownership is not transferred to the latest APIs. For example, if you initially assigned ownership to three APIs under a service and later added two more APIs to the same service, then for the two new APIs, you would need to assign ownership.
Remove API ownership using API Endpoint IDs
You can remove the API ownership of all API endpoint IDs.
Note
Make sure that you have the Edit access permission for the RBAC role for Discovery to execute this.
Use the following GraphQL query to remove ownership of APIs.
mutation Remove_owner_using_API_ids {
bulkUpdateEntities(
input: {
filterType: ID
IDs: [
"0683697d-1a5e-37a4-8b73-951027f6d7fe"
"1dfd01bc-9c4f-34e6-8f33-ca7ffb61b7cb" //Replace the placeholder value with the actual IDs
]
operation: {
operationType: ATTRIBUTE_UNSET_OPERATION
attributeUnsetOperation: { key: "owner" }
}
type: "API"
}
) {
updatedCount
}
}In the above example:
The ownership of two APIs is being removed.
Remove the owner of all API Endpoints under a service
You can remove ownership of all API endpoints associated with a particular service.
Note
Make sure that you have the Edit access permission for the RBAC role for Discovery to execute this.
Use the following GraphQL query to remove ownership from all the APIs under a service:
mutation Remove_owner_using_service_id {
bulkUpdateEntities(
input: {
filterType: ATTRIBUTE
filters: {
key: "Service ID"
operator: EQUALS
value: "6dfd8560-4767-38f4-9cd1-6769be68929e" // Replace the value with the actual Service ID
}
operation: {
operationType: ATTRIBUTE_UNSET_OPERATION
attributeUnsetOperation: { key: "owner" }
}
type: "API"
}
) {
updatedCount
}
}In the above example, the ownership of all the API Endpoints under the service with Service ID 6dfd8560-4767-38f4-9cd1-6769be68929e is removed.
Adding an owner to a multivalued owner attribute
You can add an owner to a multivalued owner attribute.
Note
Make sure that you have the Edit access permission for the RBAC role for Discovery to execute this.
You can use the following GraphQL query to add owners to a multivalued owner attribute:
mutation Add_owner_to_multi_valued_attribute_using_API_id {
bulkUpdateEntities(
input: {
filterType: ID
ids: ["0683697d-1a5e-37a4-8b73-951027f6d7fe"] // Replace the ID with the actual IDs
operation: {
operationType: MULTI_VALUED_ATTRIBUTE_OPERATION
multiValuedAttributeOperation: {
key: "dev-ops-owner"
type: ADD
values: ["charlie@mycompany.com", "david@mycompany.com"]
}
}
type: "API"
}
) {
updatedCount
}
}In the above example:
Two owners, charlie@mycompany.com and david@mycompany.com, have been assigned to the API Endpoint with
ID0683697d-1a5e-37a4-8b73-951027f6d7fe.
Remove the owner from a multivalued owner attribute of an API Endpoint
You can remove the owner from a multivalued owner attribute. You can use the following GraphQL query to remove an owner:
mutation Remove_owner_to_multi_valued_attribute_using_service_id {
bulkUpdateEntities(
input: {
filterType: ATTRIBUTE
filters: {
key: "Service ID"
operator: EQUALS
value: "6dfd8560-4767-38f4-9cd1-6769be68929e" // Replace the Value with the actual Service ID
}
operation: {
operationType: MULTI_VALUED_ATTRIBUTE_OPERATION
multiValuedAttributeOperation: {
key: "dev-ops-owner"
type: REMOVE
values: ["charlie@mycompany.com"]
}
}
type: "API"
}
) {
updatedCount
}
}In the above example:
charlie@mycompany.com has been removed as an owner from all API endpoints associated with Service ID 6dfd8560-4767-38f4-9cd1-6769be68929e.
Delete the owner attribute
You can delete an existing owner attribute using GraphQL.
Note
Make sure that you have the Edit access permission for the RBAC role for Discovery to execute this.
You can use the following GraphQL query to delete the owner attribute:
mutation DeleteAttribute {
deleteAttribute(
attributeIdentifierInput: { key: "dev-ops-owner", scope: "API" }
) {
success
}
}In the above example, the dev-ops-owner attribute that we created earlier is removed.
It may take a few minutes for the change to reflect in the Traceable platform.
Rename the display name of an owner attribute
You can rename an already existing owner attribute using the GraphQL API.
Note
Make sure that you have the Edit access permission for the RBAC role for Discovery to execute this.
You can use the following GraphQL query to display the name of the owner attribute:
mutation UpdateAttribute {
updateAttribute(
attributeUpdateInput: {
identifier: { key: "dev-ops-owner", scope: "API" }
displayName: "Operations Owner"
}
) {
displayName
name
scope
type
}
}In the above example, a new display name has been assigned to dev-ops-owner. The new name is Operations Owner.
It may take a few minutes for the change to reflect in the Traceable platform.