Action Log is nothing but an audit log of actions taken. Traceable captures all your actions in the Settings (![]() ) → Account → Action log. The action log is available in the following two categories:
) → Account → Action log. The action log is available in the following two categories:
Traceable — This category captures all the actions taken by Traceable, such as threat actor status changes and severity changes.
User-related — This category captures all the actions taken by users, such as logging in and out.
Traceable collects the action log entries from all the environments and shows them for the last 1 day by default. However, you can change it to view entries for a custom duration according to your requirements. To do so, from the Duration drop-down in the page’s top right corner, click Custom, and select the time duration for which you want to view the action logs.
You can also download the logs as CSV from the Action drop-down. While downloading, you can also select the number of rows that you want to download.
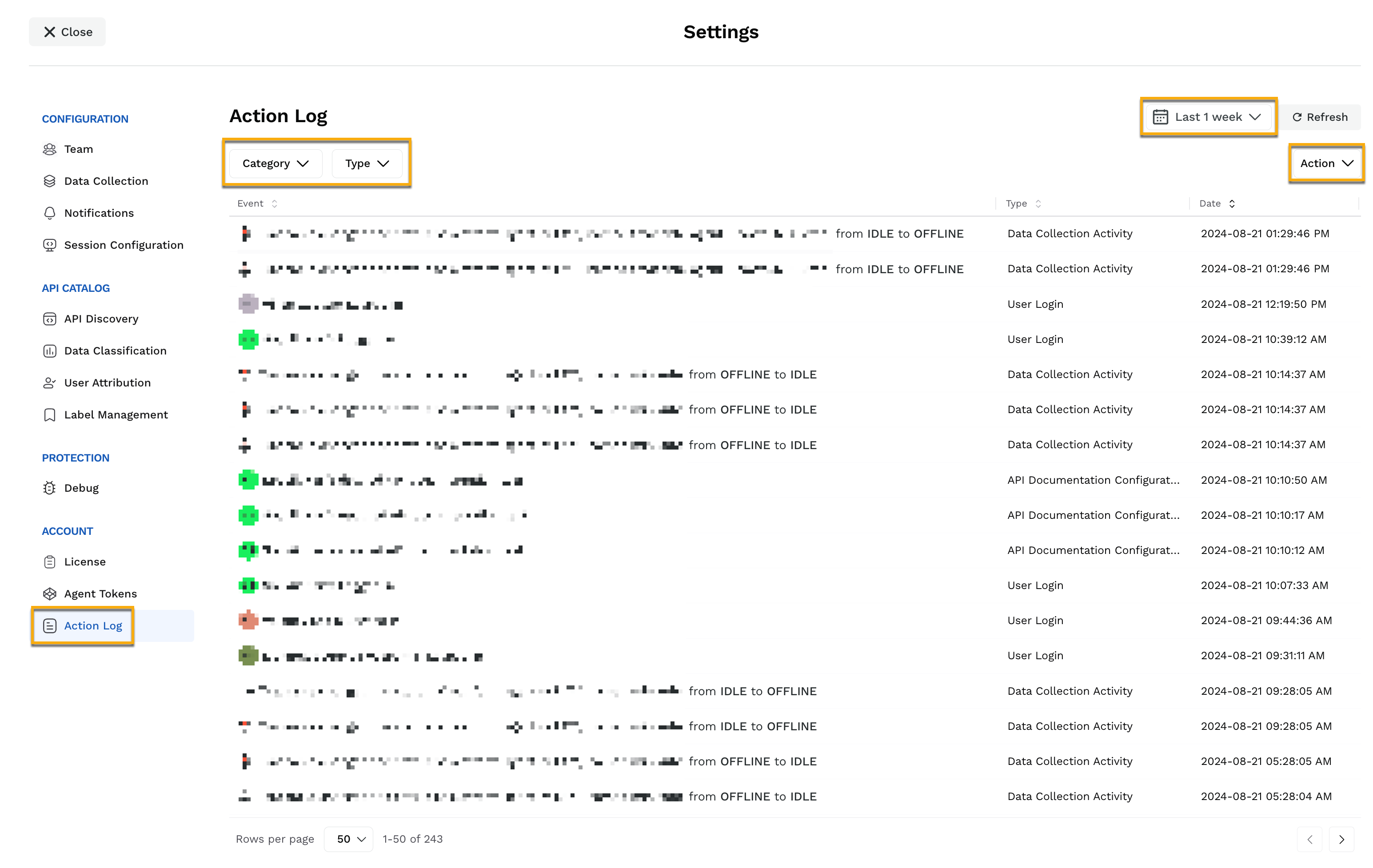
You can also select the category of actions to filter based on whether the action was carried out by you (the user) or Traceable. The actions carried out by Traceable are denoted by the Traceable icon (![]() ).
).
Following is a list of types of action logs that are captured for both the categories:
Action | Description |
|---|---|
Agent token change | Logs updates in the agent tokens. |
API documentation configuration change | Logs updates in the configuration of the uploaded API documentation. |
API naming rule configuration change | Logs updates in the API naming rules. |
AST scan change | Logs updates in the AST scans. |
AST scan policy change | Logs updates in the AST policies. |
AST scan suite change | Logs updates in the AST suites. |
Data classification configuration change | Logs updates in the Data Classification page under Settings. |
Data collection activity | Logs updates in the Data Collection configurations. |
Exclude rule configuration change | Logs updates in the exclude rules you configure. |
Integration change | Logs updates across integrations. |
Label configuration change | Logs updates in the Label Management page. |
Notification configuration change | Logs updates in the Notifications page. |
Protection configuration change | Logs updates in the configurations across API Protection. |
Risk scoring configuration change | Logs updates in Risk Scoring page under Catalog. |
Team user change | Logs additions, deletions, and changes to team members and their roles. |
Threat actor severity change | Logs updates in the severity of threat actors. |
Threat actor status change | Logs updates in the status of threat actors. |
Threat scoring configuration change | Logs updates in Threat Scoring page under Protection. |
User login | Logs instances and methods of users logging in to the platform. |
User logout | Logs instances when users sign out of the platform. |
Traceable logs all actions except for logged and blocked threat activities. You can view these threat activities by navigating to the Protection → Threat Activity page and selecting Alerted or Blocked from the Status filter.
You can also set up notifications for the above action log types, including logged and blocked threat activities. For more information, see Notification.
Threat actor details from the action log
You can view details about each action log entry. You can view all the events a threat actor generates by clicking on the displayed IP address or the username in the log entry. Traceable displays the Activity Log of that threat actor or attacker in the Protection → Threat actors section.
In the same log entry, you can also click the Drill-down (![]() ) icon to navigate to the Traces page and view all the traces generated by the threat actor.
) icon to navigate to the Traces page and view all the traces generated by the threat actor.