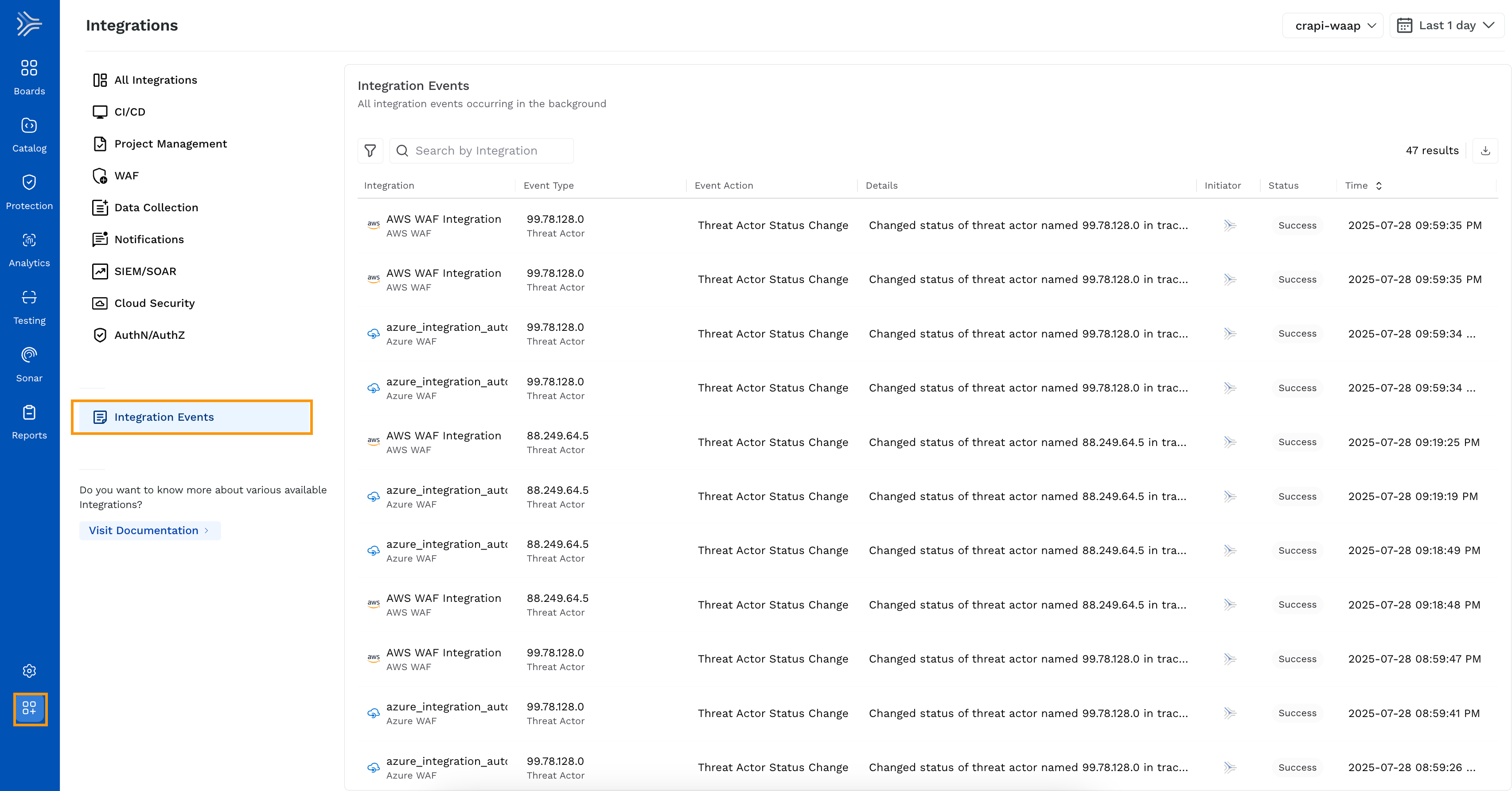
The Integration Events page in Traceable provides a comprehensive log of actions and events generated for integrations, such as WAFs. These events are displayed in the Traceable platform and help track Create, Update, and Delete operations, as well as status changes, for various integrations.
Integration events occur in the background and are associated with specific actions, such as rule creation, updation, or deletion. This enables users to monitor integration-specific activities and their outcomes.
Supported integrations
Integration events are currently supported for the following WAFs:
AWS
Azure
Akamai
Cloudflare
Fortinet
Google Cloud Armor
F5
Imperva
Events are generated only for these integrations and within their configured environments.
View integration events
To view the integration events, navigate to the Integrations( ![]() ) → Integration Events page.
) → Integration Events page.
Event Categories
The Integration Events page provides details on the following types of actions:
Action | Description |
|---|---|
Create | Generated when a new rule or configuration is successfully created. |
Update | Generated when an existing rule or configuration is modified. |
Delete | Generated when an existing rule or configuration is removed. |
Threat Actor Status Changes | Generated when the status of a Threat Actor changes. |
Columns in the Event Table
The Integration Events table contains the following columns:
Columns | Description |
|---|---|
Integration | Identifies the integration, for example, AWS, Azure, and Akamai. |
Event Type | Describes the category of the event, for example, Threat Actor Status Change, and Malicious Source Rule. |
Event Action | Details the specific action performed, for example, Create, Update, or Delete. |
Details | Provides additional information about the event outcome, including success, unsupported, or failure messages. |
Initiator | Indicates the user or system responsible for initiating the event. |
Status | Displays whether the event was a Success, Unsupported, or Failed. |
Time | Shows the timestamp of the event. |
Detailed Behavior
Rule Creation
Supported Rules:
For valid rule configurations, successful creation events are generated.
Unsupported Rules
Third-party WAF Limitations:
An Unsupported Operation event is generated when the third-party WAF provider does not support specific attributes or actions. For example:Allow IP Range Rule in Akamai: This generates an Unsupported Operation event because Akamai does not support this action.
SecRule or Attribute Rule: Generates an Unsupported Operation event for all WAFs where these rule types are unsupported.
Traceable-Specific Limitations:
No integration event is generated for rule types not supported by Traceable, for example, Alert-type rules or unsupported configurations. This ensures that customers can differentiate between limitations imposed by third-party WAF providers and those inherent to Traceable's functionality.Custom Signature Rules:
No event is generated for WAFs that do not support Custom Signature Rules, for example, Azure.
Unsupported configurations or actions within these rules will not result in an Unsupported Operation event.
Rule Updates
Successfully Created Rules:
Updates to valid configurations generate successful update events.
Updates to unsupported configurations generate unsuccessful update events, and the previous rule is deleted.
Uncreated or Invalid Rules:
Updates to invalid configurations do not generate events.
Updates to valid configurations generate successful update events, creating the rule.
Alert-Type Rules:
Updates to Alert configurations result in rule deletion, but no event is generated.
Transitioning from Alert to Allow/Block:
If valid for the WAF, the rule is created, and a corresponding event is generated.
Rule Deletion
Successfully Created Rules:
Deletions generate successful deletion events.
Unsupported or Uncreated Rules:
Deletions do not generate events.
Complex Custom Signature Rules
If a custom signature rule includes multiple payload types and at least one is unsupported, for example, Attribute or SecRule, the rule is deemed unsupported, and an Unsupported Operation event is generated during both creation and update actions. This ensures that rules containing any invalid payload types are flagged for correction.
Threat Actor Status Changes
Status changes for Threat Actors, for example, from Active/Monitored to Allow/Block/Deny and vice-versa, generate corresponding integration events.
Environment-Specific Events
Integration events are environment-specific. If a rule or WAF integration is configured in a particular environment, events are generated only within that environment. You must switch environments in the Integration Events page to view relevant events.
Caveats
For any Create, Update, or Delete action, only one integration event is generated, if applicable.
Environment-specific configurations limit events related to rule creation and deletion.
No events are generated when updating an invalid configuration or deleting unsupported rules.