Mutation is the modification of API inputs during security testing to discover vulnerabilities (issues). By sending altered data, mutation simulates real-world attacks to expose vulnerabilities such as injection and improper error handling in your application system. Similarly, Assertion is also used as part of the testing. It is the validation process where the expected responses of APIs are compared against the actual ones. This ensures that the APIs are secure and behaving as expected under conditions similar to those in mutations.
Mutations and Assertions in Traceable’s AST are components defined as part of the test and custom plugins. They enable you to customize API assessment and validate the expected behavior, respectively. While Traceable provides some default values to the mutations and assertions pre-defined in the test plugins, you can customize them to override the existing values according to your requirements. For example, an API might receive response codes other than 200 OK. In this case, you can override the existing mutation such that the response code of the mutated request can vary from the original response code, preventing false positives. These overrides can help increase the efficiency of the AST scans.
Apart from customizing the existing overrides, you can configure new overrides according to your business use case. You can configure them from the Evidence page of an issue detected by an AST scan. Upon configuration, Traceable executes these overrides for all future scans until you disable or delete them. It also shows all new and customized overrides on the Evidence page of future scans and the Overrides tab on the Policies page.
Note
Configuring new overrides or customizing existing ones is available for Traceable-defined test plugins only. For custom plugins, you can add or modify the mutation and assertion functions in the code. For more information on these plugins, see Custom Plugins.
Configuring a New Override
Overrides enable you to manually adjust or redefine values in the assertion and mutation functions associated with the test and custom plugins. For example, you may have strict rate-limiting policies to prevent excessive API traffic and DDoS attacks. However, some users may need to bypass these limits under certain conditions. For such scenarios, you can configure an override to allow certain endpoints, identified by an IP address or API key, to exceed the defined limits without triggering the rate-limiting alerts.
To configure a new override, complete the following steps:
Navigate to Testing → Scans and select the scan for which you want to configure an override.
In the Scan Details page, in the Issues tab, expand the issue name and select the vulnerability (issue) for which you want to add an override.
In the Issue Detailed View, Overview tab, expand the Evidence section.
Do one of the following according to your requirements:
In the top right of the Assertions tab, click + Add Assertion.
Click the Mutations tab, and click + Add Mutation.
In the pop-up window that appears, specify the following fields:
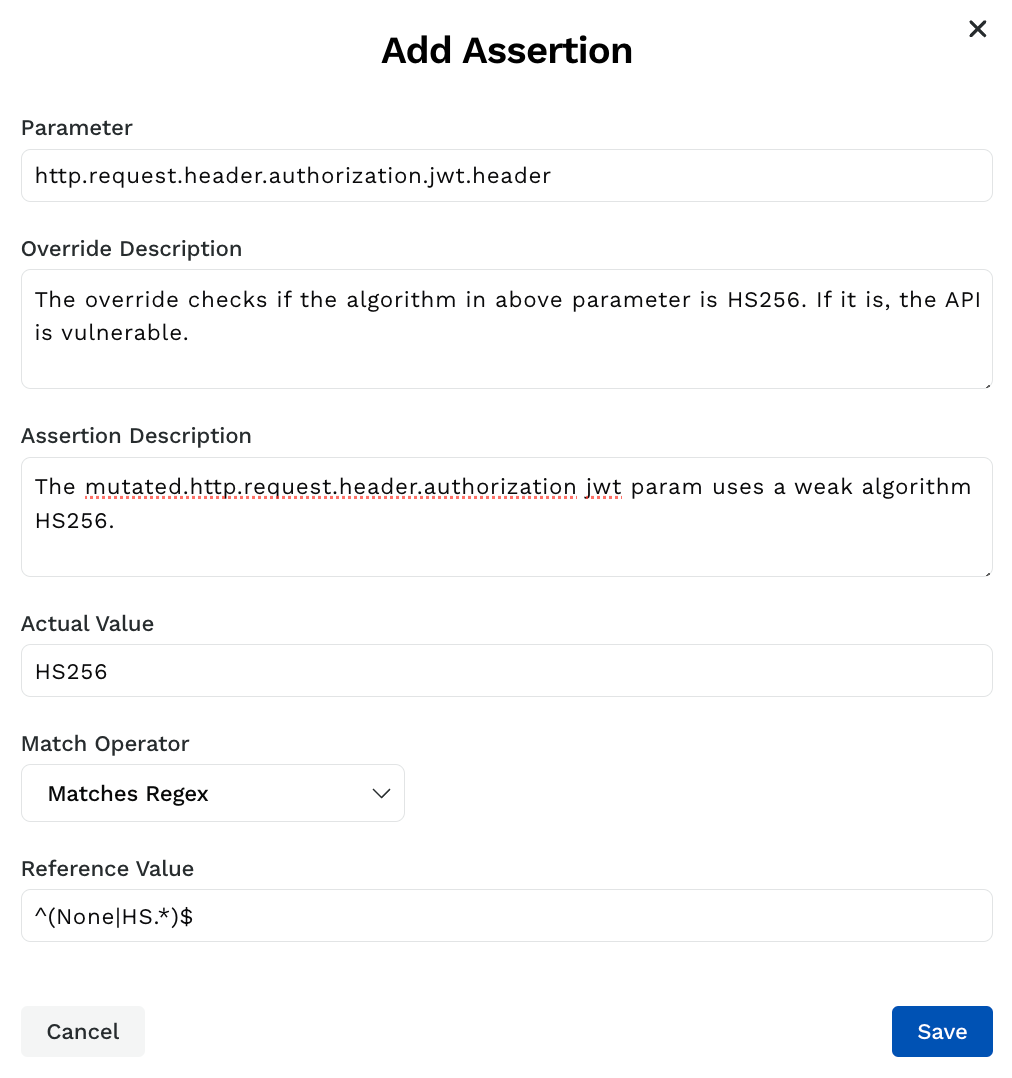
Parameter — The parameter on which you want to apply the override. Traceable searches for this parameter in the API endpoints configured as part of the scan.
Override Description — A description of the override.
Assertion/Mutation Description — A description of the original assertion or mutation.
Actual Value — The original value or attribute present in the API trace. You can skip this field as Traceable auto-populates it according to the value it finds in the API trace.
Match Operator — The operator corresponding to the parameter field above.
Reference Value — The value or pattern based on which you want Traceable to apply the assertion or mutation. Traceable uses the match operator you select above to evaluate the parameter’s actual value against this reference value.
Click Save.
Customizing an Existing Override
To customize an existing override, complete the following:
Navigate to Testing → Scans and select the scan for which you want to customize the override.
In the Scan Details page, in the Issues tab, expand the issue name and select the vulnerability (issue) for which you want to add an override.
In the Issue Detailed View, Overview tab, expand the Evidence section.
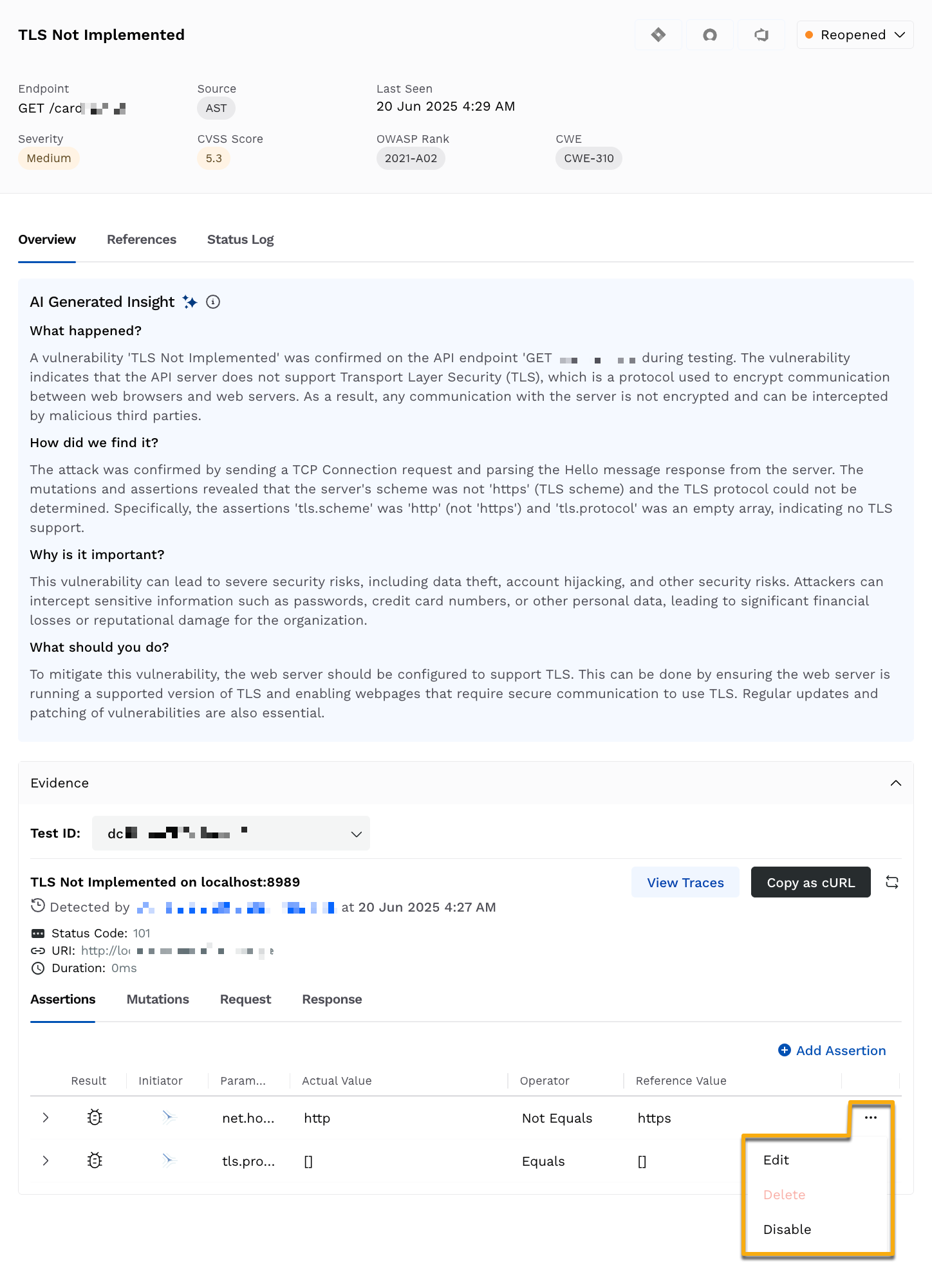
From the Assertion or Mutation tab, click the Ellipse icon corresponding to the assertion or mutation you wish to edit.
Click Edit.
Modify the fields according to your requirements in the pop-up window that appears.
Click Save.
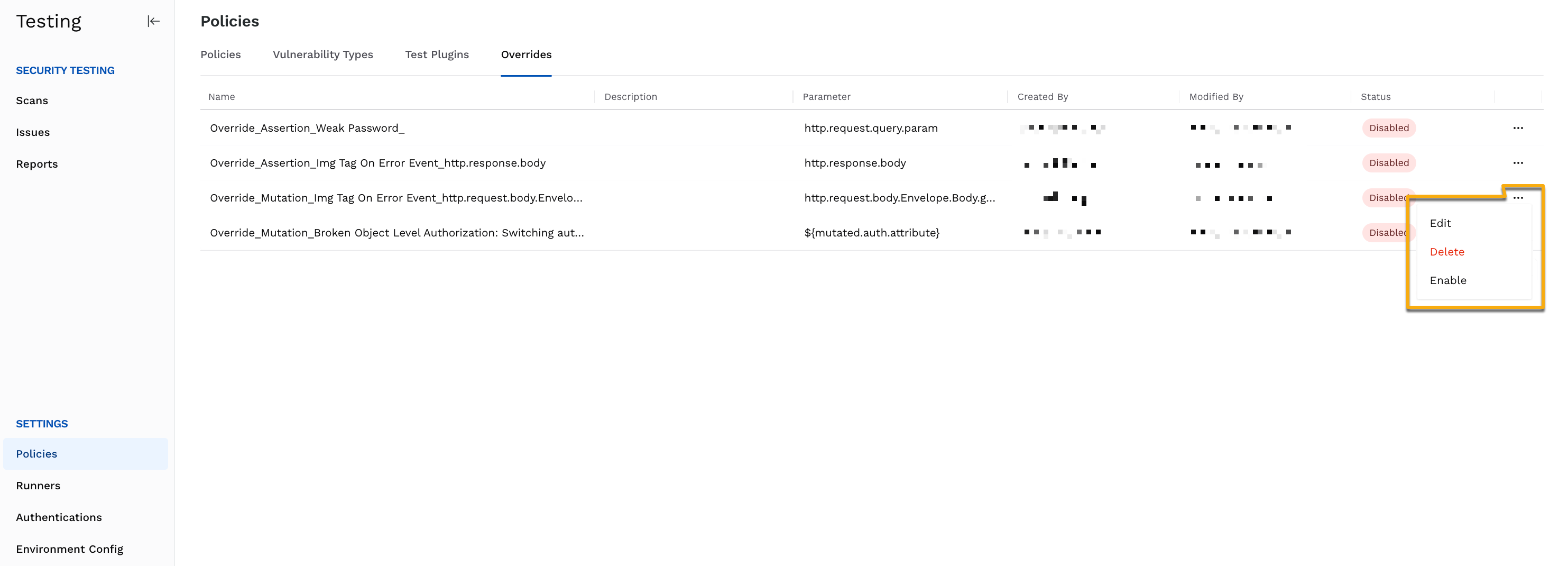
Actions on Overrides
You can carry out the following actions on pre-defined or configured assertion and mutation overrides according to your requirements:
Edit the overrides to modify fields.
Delete the overrides.
Note
A deleted override cannot be restored.
You cannot delete pre-defined overrides.
Disable overrides if you do not want Traceable to detect vulnerabilities (issues) based on those overrides.
Note
If you disable an override, the corresponding mutation or assertion is also disabled, which means that the plugin does not consider the mutation or assertion during execution.
You can execute the above actions from the following pages:
Evidence section in an Issue’s Detailed View
Overrides tab in the Policies page